SlashNext Blog
Phishing, social engineering, and modern threats.
Featured Article
Decoding ‘ClickFix’: Lessons from the Latest Browser-Based Phish
ClickFix is a social engineering attack that tricks users into running malicious commands on their own devices – all under the guise of a routine security check. Disguised as something familiar, like a Cloudflare CAPTCHA, it convinces users to copy and paste dangerous code without realizing the risk. We’ll break down how ClickFix works, examine […]
Featured Article
10 Ways URL Analysis & Enrichment Can Help Ease Your SOC’s Challenges in 2020
On-demand phishing URL analysis solutions can help ease your SOC teams’ pain and challenges.
Blog Subscription

Multi-Channel Threat Blindspot Will Leave Your Organization Vulnerable to Breach
In today’s hyper-connected world, modern workers rely on a multitude of communication and collaboration tools to get work done efficiently. Email, SMS, Slack, Microsoft Teams – the average employee juggles between 6…

The Tolly Group Report Highlights SlashNext’s Gen AI-Powered Email Security Prowess
In the ever-evolving landscape of cyberthreats, email remains a prime target for malicious actors, with zero-hour Business Email Compromise (BEC) and advanced phishing attacks posing significant risks to organizations. A recent…

Understanding Credential Phishing
Credential phishing is a type of cyberattack where attackers attempt to deceive your employees into providing their sensitive information, such as their Microsoft usernames and passwords. What is not obvious is credential phish…

Understanding Business Email Compromise (BEC)
What is Business Email Compromise? Business Email Compromise (BEC) is a sophisticated form of cybercrime where attackers use email to deceive and defraud organizations. Unlike typical phishing attacks that cast a wide net, BEC …

Sophisticated Smishing Compromises Employee Accounts, Accesses Corporate Gift Card Systems
We at SlashNext want to draw attention to the alarming trend of cybercriminals exploiting advanced techniques to target retail corporations, as highlighted in the recent FBI Private Industry Notification (PIN). The threat actor…

SlashNext Introduces Gen AI for Spam and Graymail
SlashNext introduced a groundbreaking service, SlashNext Gen AI for Spam and Graymail, this week. This service is the first of its kind to use a generative AI large language model (LLM) for detecting and filtering spam and gray…

From Caesar to Cyberspace: The Growing Menace of Obfuscated Phishing Scams
In the world of cybersecurity, it often feels like we’re revisiting familiar problems, albeit with a modern twist. The essence of the issue isn’t about the emergence of entirely new types of cyberattacks but rather …

Think Security Training Will Save You From Phishing Attacks? Think Again!
What’s Required: Intercept phishing attempts before they reach the intended targets In the vast and intricate web of cybersecurity threats, phishing attacks stand out for their deceptively simple yet alarmingly effective …

Evolving Cyber Threats: Insights and Strategies from the 2023 FBI IC3 Report
Latest FBI IC3 Report shows a record year for cybercrime: record-setting $12.5 billion in losses The 2023 FBI IC3 report reveals not just numbers but narratives that underscore the adaptability and cunning of today’s cybe…

Threat Actors are Exercising New Attack Techniques to Bypass Machine Learning Security Controls
“Conversation Overflow” attacks are the latest attempt to get credential harvesting phishing emails into your inbox SlashNext threat researchers have uncovered a dangerous new type of cyberattack in the wild that uses clo…
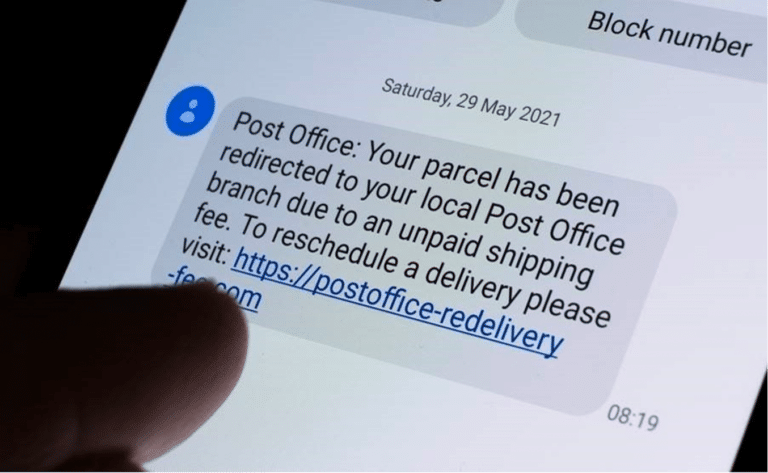
SMS Gateways Allow Cybercriminals to Flood Phones With SMS Phishing Messages For Just €0.004 ($0....
Our team has been investigating the latest services and infrastructure available to cybercriminals for orchestrating SMS phishing campaigns. After analysing cybercrime forums, it is clear that SMS gateways are currently a highl…

Silent, Yet Powerful Pandora hVNC, The Popular Cybercrime Tool That Flies Under the Radar
Pandora hVNC is a remote access trojan (RAT) that has been advertised on cybercrime forums since 2021. Surprisingly, it has received little attention from the cybersecurity community. Despite this, it remains a widely used tool…
It’s Time to Get Started with SlashNext
Learn how to leverage the industry’s best zero-hour phishing protection in your environment.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.


