SlashNext Complete™
Next Gen AI messaging security to stop threats and exploits in Microsoft 365, Zoom, Teams, Slack and other messaging channels.
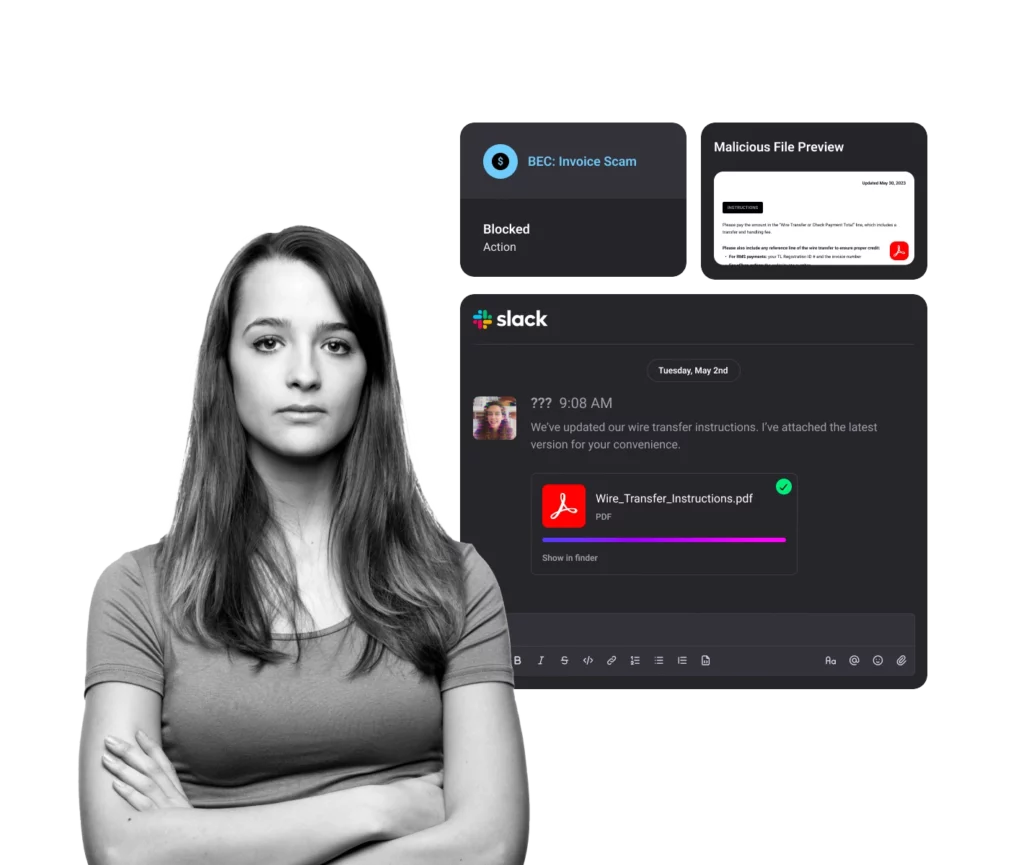
BEC and SMS Attacks are the Top Threats Impacting Business Today

Growing Threats
83% of organizations report mobile threats are growing more quickly than other device threats and lead to successful breaches.

Sophisticated Phishing
With automation and AI technology, BEC and spear phishing can easily adapt until successful.
Data Breach Cost
The average global cost of a data breach is $4 million with losses exceeding $10.3 billion annually.
A Complete Cloud Security Platform to Stop the Most Evasive Threats in Real-Time
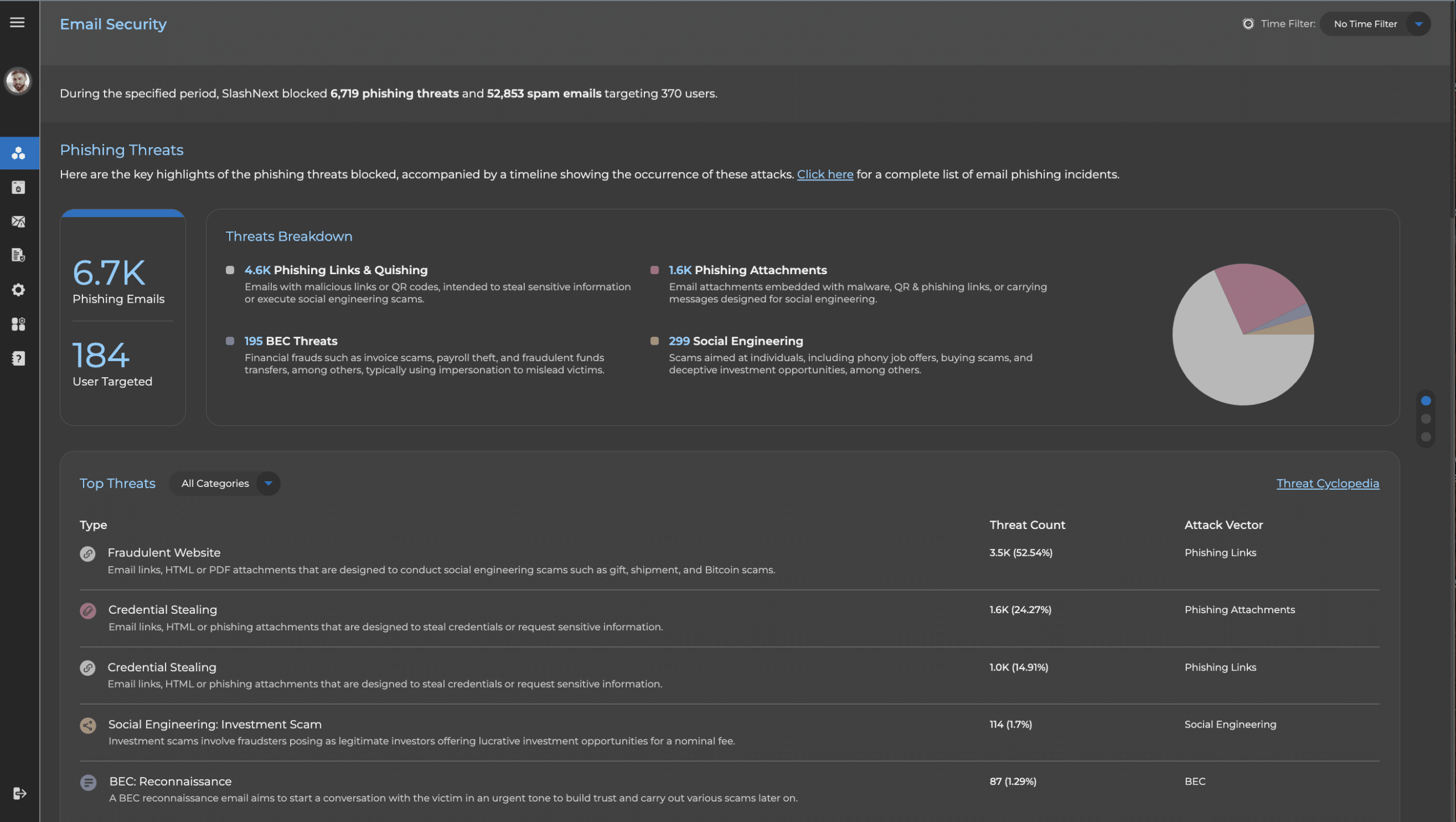
Keep users safe with a more effective approach that uses natural language processing, computer vision, and machine learning with relationship graphs, generative AI, and deep contextualization to stop zero-hour threats in real-time with 99.9% accuracy and 1 in 1 million false positives. This unique combination of techniques sees through evasion tactics and accurately detects threats, even those hosted on compromised websites and legitimate infrastructure.
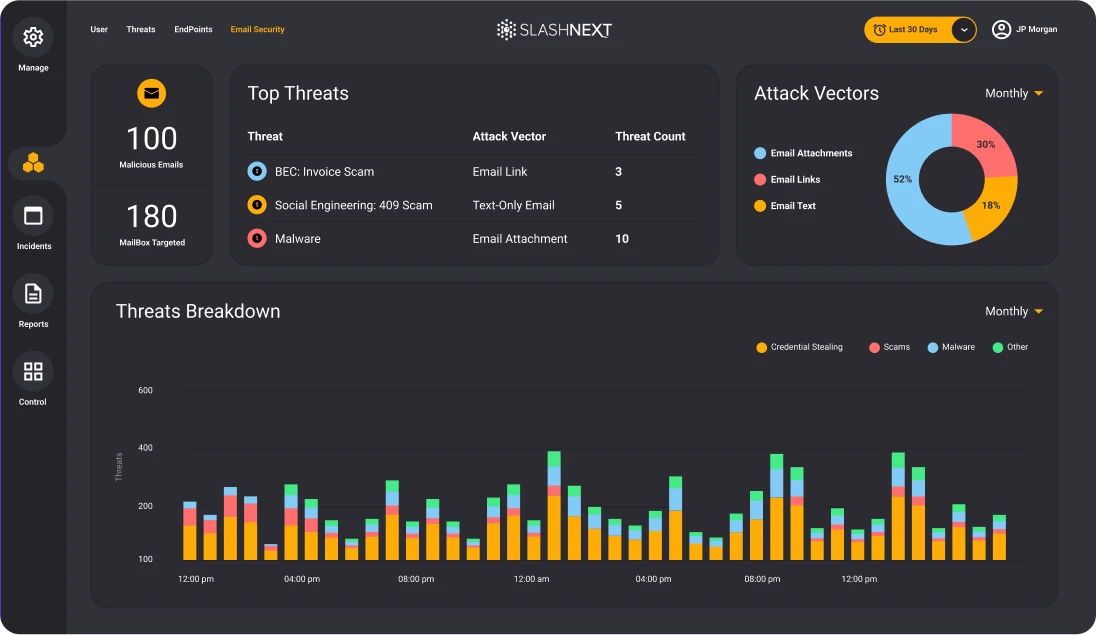

Best Zero-Hour Link, File and BEC Detection

Quick and Easy Implementation

Comprehensive Management and Controls
SlashNext Next Gen AI Email + Messaging Security
SlashNext AI technology stops threats in email plus all other messaging channels that compromise users and lead to a data breach.
Cloud Email Security for Microsoft 365
SlashNext’s Integrated Cloud Email Security provides a full defense-in-depth approach by supplementing Microsoft Defender with protection that is purpose-built to anticipate and stop the vast number of sophisticated zero-hour linked-based attacks, natural language-based attacks, malicious attachments and exploits that evade Microsoft Defender for Office 365.
Set-up to detection in 5 minutes using Microsoft Graph API and a phenomenal ROI with twice the protection at half the cost of secure email gateway (SEG) solutions.
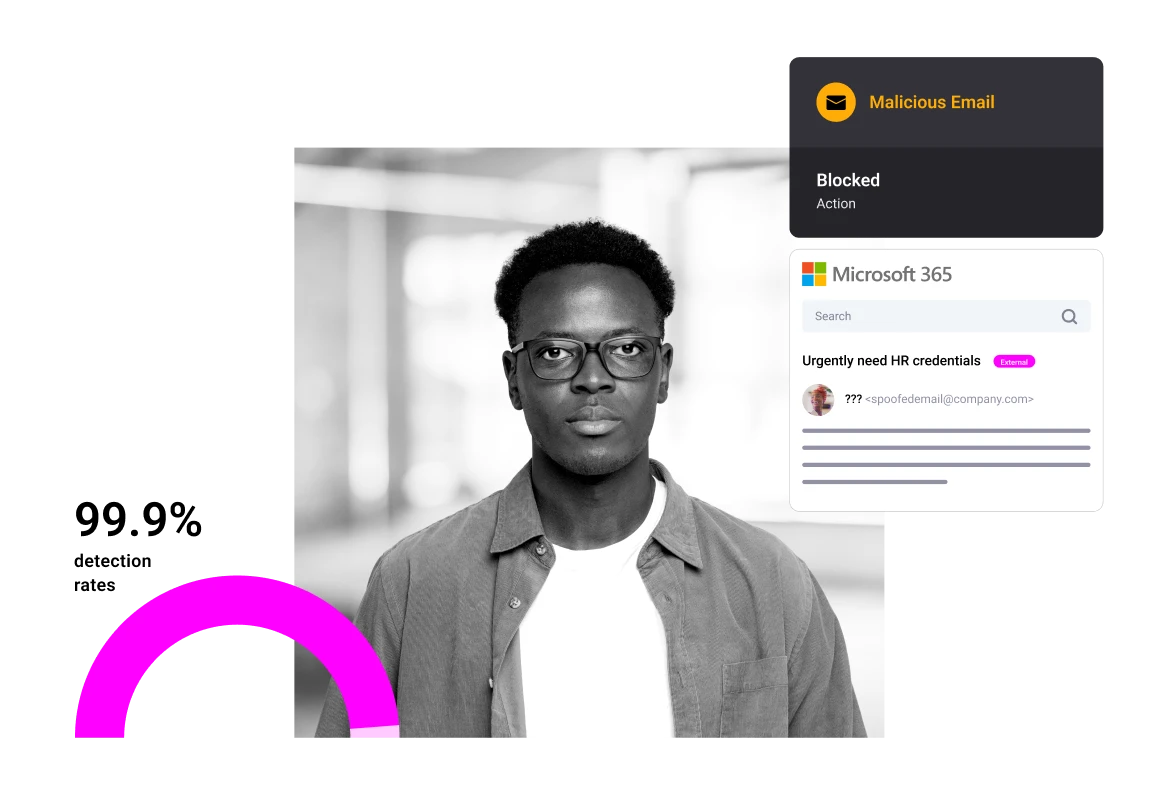
Protection for SMS and Mobile Apps
Stop smishing and business text compromise with zero-hour protection against the broadest range of link based and natural language threats in any mobile application. Available for business, BYOD and home devices.
With on-device machine learning, users will benefit from detection without giving up privacy. Centrally managed for enterprise users, with multiple deployment options, incidents written to CMS, and supports all device types.
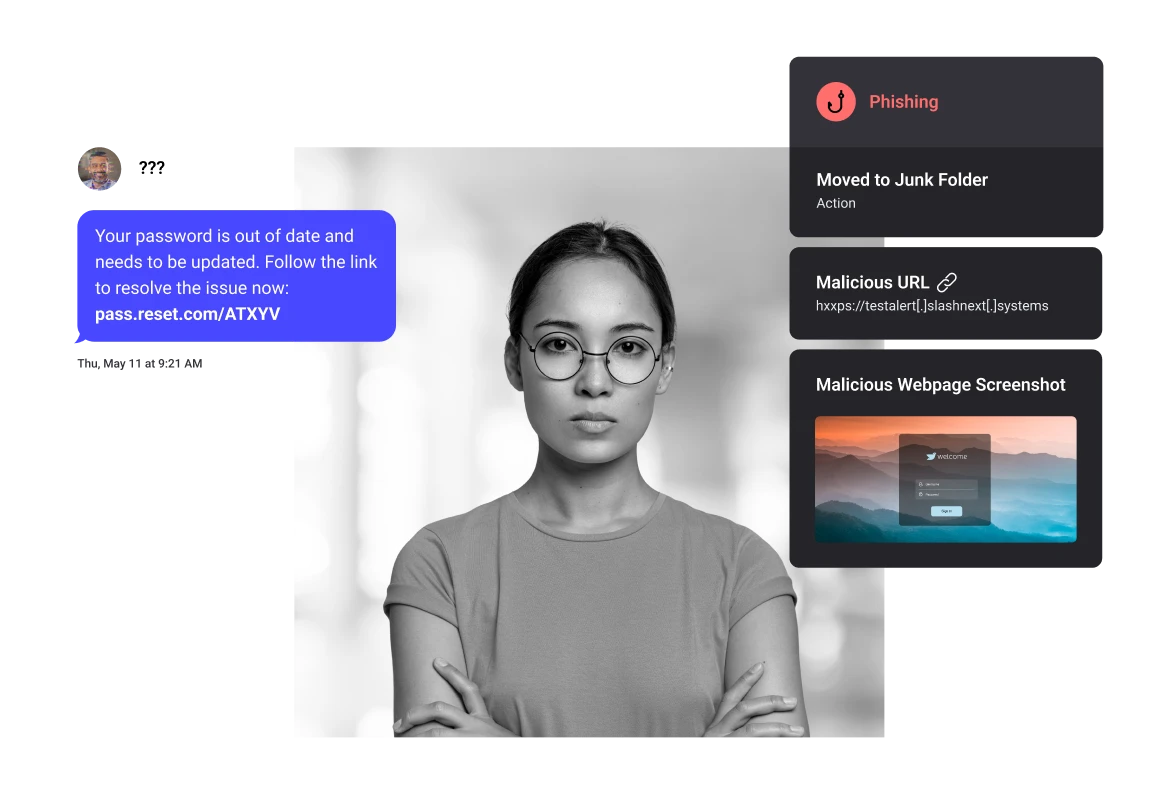
Protection for Slack, Zoom, Teams, Gmail and Other Messaging Apps
Integrated browser extension stop zero-hour link and exploit threat in all web messaging apps, including email, ads, social media, search, collaboration platforms, and more.
By blocking malicious sites in real-time, SlashNext protects users from more zero-hour threats including those that evade multi-layer enterprise defenses.
Cloud Mangement Console
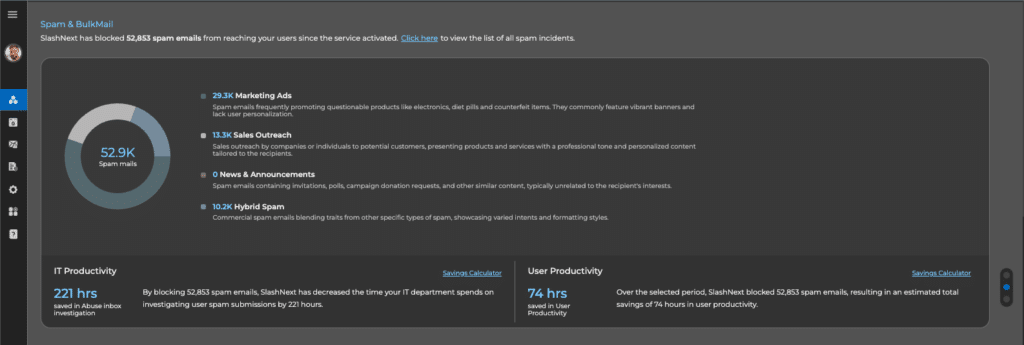
Stop The Attacks That Impact Your Business

Social Engineering, Scams and Fraud
Deception to manipulate users into divulging information for misuse.

Trusted Services Compromise
Uses trusted domains to obfuscate cyber attacks to increase success.
Ransomware, Malware and Exploits
Intended to inject code, take-over browser canvas or download malware.

Malicious Attachments
Malicious HTML, PDF and Office files used to harvest credentials or download malware.

BEC, ATO and Supply Chain Attacks
Targets execs or financial teams to defraud a company for financial gain.

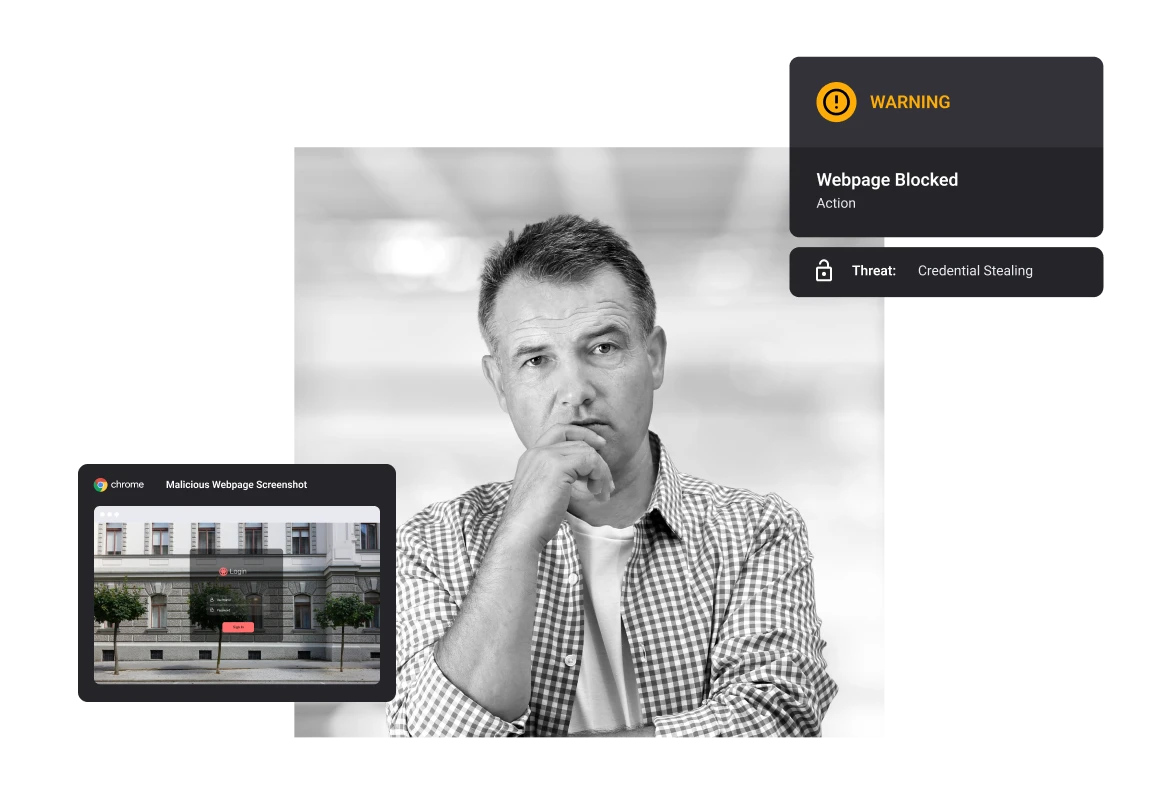
Credential Stealing
Cyber attack designed to steal passwords with the intent of accessing protected data.
Spear Phishing
Personalized targeted attack designed to trick users into a data breach or for financial gain.
QR Code Phishing
Block Quishing and QRL Jacking with computer vision and NLP
SlashNext Delivers Best in Class Results on Day One
5 mins.
To set-up and configure service using the Microsoft Graph API
99.9%
Detection rate with 1 in 1 million false positives
2x more
Blocks two times more than competing supplemental solutions
1 hr.
Incident caught within 1 hr. for incredibly quick time to value
46%
Patient-zero email attacks detected by SEER™ Live Scan
48 hrs.
Detection advantage vs other threat engines

We found a lot of value in their (phishing) protection. Overall a great addition to our cybersecurity protection suite.
CIO, Moffatt & Nichol
Related Resources
FEATURED WHITE PAPER
Microsoft 365 + Integrated Cloud Email Security
Due to the demands of the modern workforce, there has been an exponential shift in the use of native cloud email protection capabilities, like Microsoft 365, in the last 12 months.

FEATURED DATA SHEET
SlashNext
Complete
Complete multi-channel security for email, mobile and web messaging app.

Featured Blog
State of Phishing Report Reveals More Than 255 Million Attacks in 2022
SlashNext analyzed billions of link-based URLs, attachments, and natural language messages in email, mobile and browser channels over six months in 2022 and found more than 255 million attacks…
See SlashNext Complete™
in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.



