
What’s Required: Intercept phishing attempts before they reach the intended targets
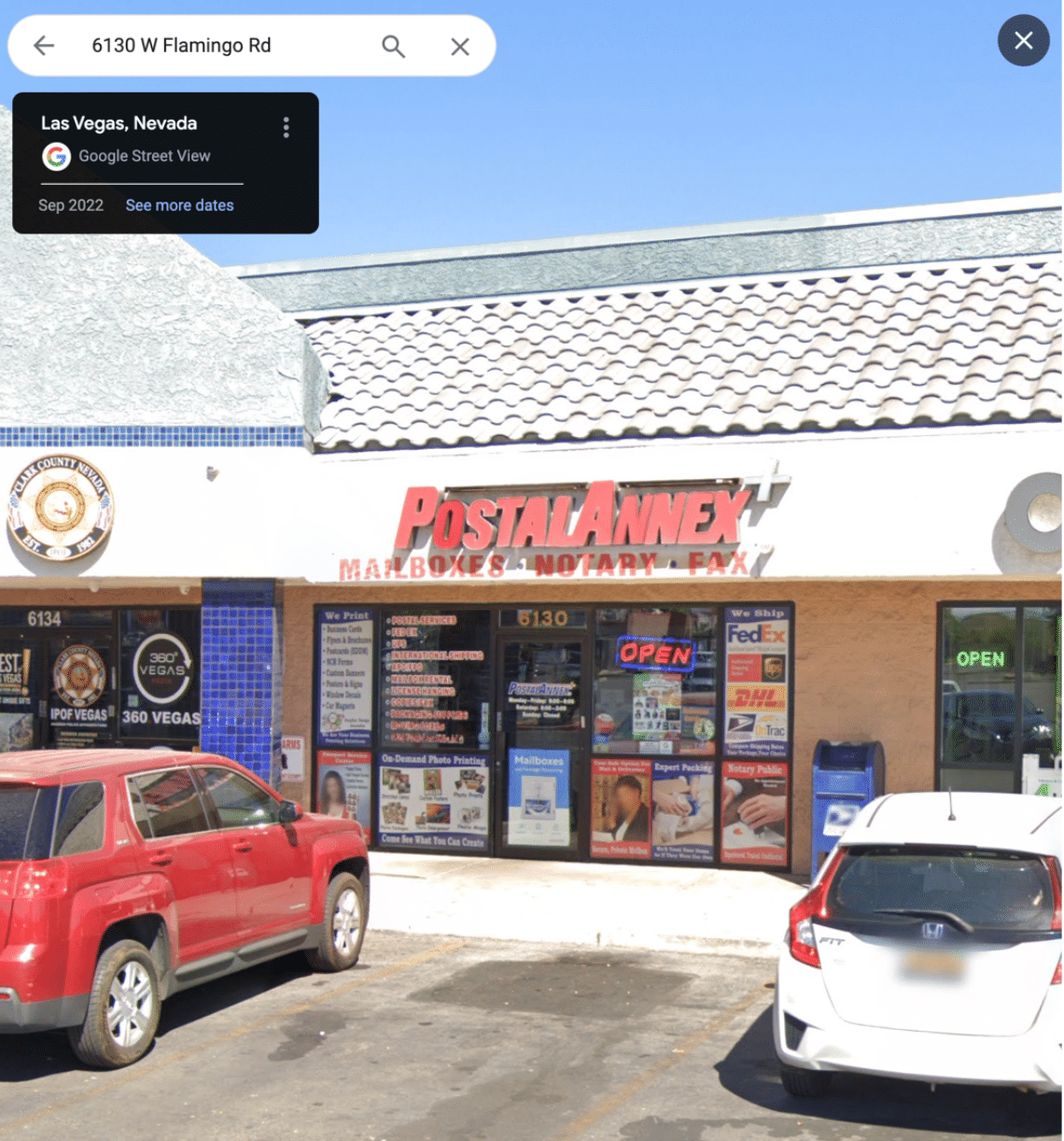
In the vast and intricate web of cybersecurity threats, phishing attacks stand out for their deceptively simple yet alarmingly effective tactics. As we delve into the anatomy of a typical phishing scam, it becomes apparent why these attacks not only persist but thrive in our digital ecosystem. Take a look at this: an unsuspecting user receives a message, purportedly from “Storage iCloud,” claiming their drive is full and urgently requesting payment to resolve the issue. To the untrained eye, this might seem like a legitimate request. However, a closer inspection reveals telltale signs of deception, such as a physical address that, when checked, leads to a run-down strip mall in Las Vegas far removed from the polished corporate offices one might expect.
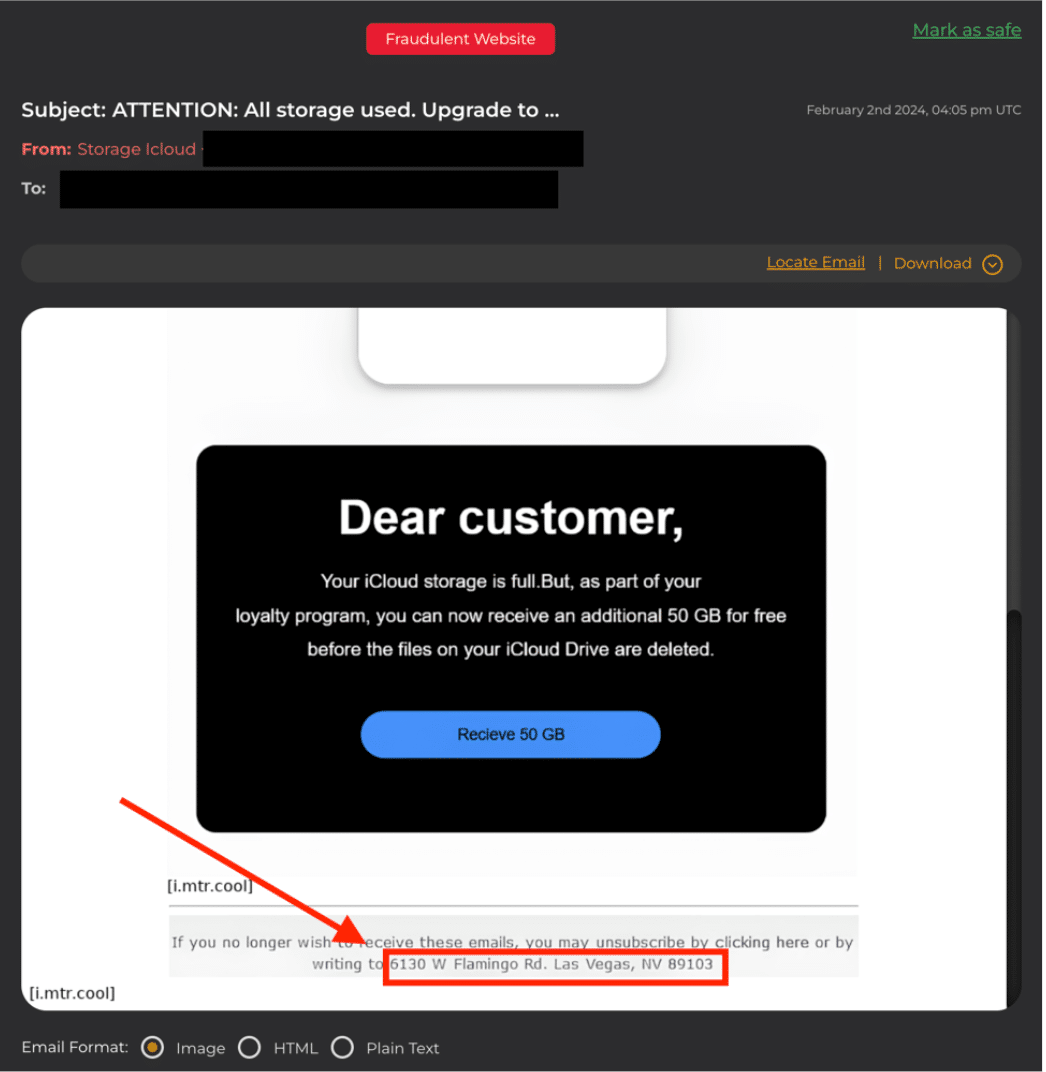
This scenario isn’t just a cautionary tale; it’s a reality that unfolds daily. Somewhere, someone falls victim to phishing, underscoring a harsh truth: we are all susceptible to lapses in judgment, especially when attackers exploit our trust in familiar entities like Apple iCloud and create a sense of urgency.
The mechanics of phishing are straightforward, relying on volume rather than sophistication. Attackers cast a wide net, knowing that even the most transparent scams will ensnare a few. They bank on catching individuals during vulnerable moments, using the guise of authority to create panic and prompt hasty actions. This numbers game highlights a critical vulnerability in our defenses: the human element.
Phishing scams are shockingly easy for attackers, highlighted by one coming from a simple place: 6130 W. Flamingo Rd., Las Vegas NV 89103, where there’s just an old strip mall. This shows that attackers don’t have to put in much work to trick people, using everyday emails to catch victims easily.
Witnessing the fallout from these attacks raises questions about the efficacy of user training in combating phishing. While educating users on the risks and signs of phishing is undeniably valuable, the reality is stark. Achieving a click rate below 10%—indicating the percentage of phishing emails interacted with—is a feat seldom seen. This observation isn’t just anecdotal; it’s a widespread challenge acknowledged by cybersecurity professionals and user awareness training programs alike.
Does this mean we should abandon user training? Absolutely not. Awareness and education are essential components of a comprehensive cybersecurity strategy. However, we must acknowledge their limitations. Training can reduce susceptibility to phishing but cannot eliminate it. Humans are inherently fallible, and attackers are adept at manipulating emotions and trust.
This brings us to the crux of the matter: the need for robust, technological solutions capable of intercepting phishing attempts before they reach their intended targets. Enter tools like SlashNext, designed to address the phishing problem at its core. Unlike traditional defenses, which rely heavily on user discretion, SlashNext offers a proactive approach, employing advanced detection mechanisms to identify and neutralize phishing threats in real time.
The reliance on user discernment in the face of increasingly sophisticated phishing tactics is akin to bringing a knife to a gunfight. As the landscape of cyberthreats evolves, so too must our defenses. Tools like SlashNext represent the next frontier in cybersecurity, offering a beacon of hope in the ongoing battle against phishing. They provide the technological might needed to complement user awareness, forming a dual-layered defense that is both comprehensive and effective.
In conclusion, while user training plays a crucial role in cybersecurity, it is not a panacea. The persistent threat of phishing attacks, characterized by their simplicity and exploitation of human vulnerability, demands a more formidable response. Advanced solutions like SlashNext are not just beneficial; they are necessary. In the digital age, where attackers constantly seek to exploit the weakest link, we must fortify every aspect of our defense, combining human vigilance with technological prowess to safeguard our digital lives.
Discover how SlashNext can extend your protection across email, mobile, and web messaging apps. Request your personalized demo today.


