Protection for Slack, Zoom, Teams, Gmail and Other Messaging Apps
Protect users from the broadest range of zero-hour phishing sites with cloud-powered browser protection that is better than browser isolation. Available for Chrome, Safari, Edge, Firefox, and more.

The Broadest Range of Zero-Hour Phishing Attacks Happen in the Browser

Malware and Exploits
Malicious URLs and exploits routinely evade legacy security solutions, leading to business disruption, financial loss, and customer trust.

Sophisticated Phishing
The average global cost of a data breach is $4 million with losses exceeding $10.3 billion annually.
Data Breach Cost
The average global cost of a data breach is $4 million with losses exceeding $10.3 billion annually.
Stops Zero-Hour Links and Exploits in All Web Apps
SlashNext’s Browser Extension provides real-time detection with extreme accuracy to detect malicious sites hours before the competition. By blocking threats in real-time, SlashNext protects users from more malicious content, including those that evade multi-layer enterprise defenses.
How SlashNext Stops the Widest Range of Attacks from Entering Your Organization
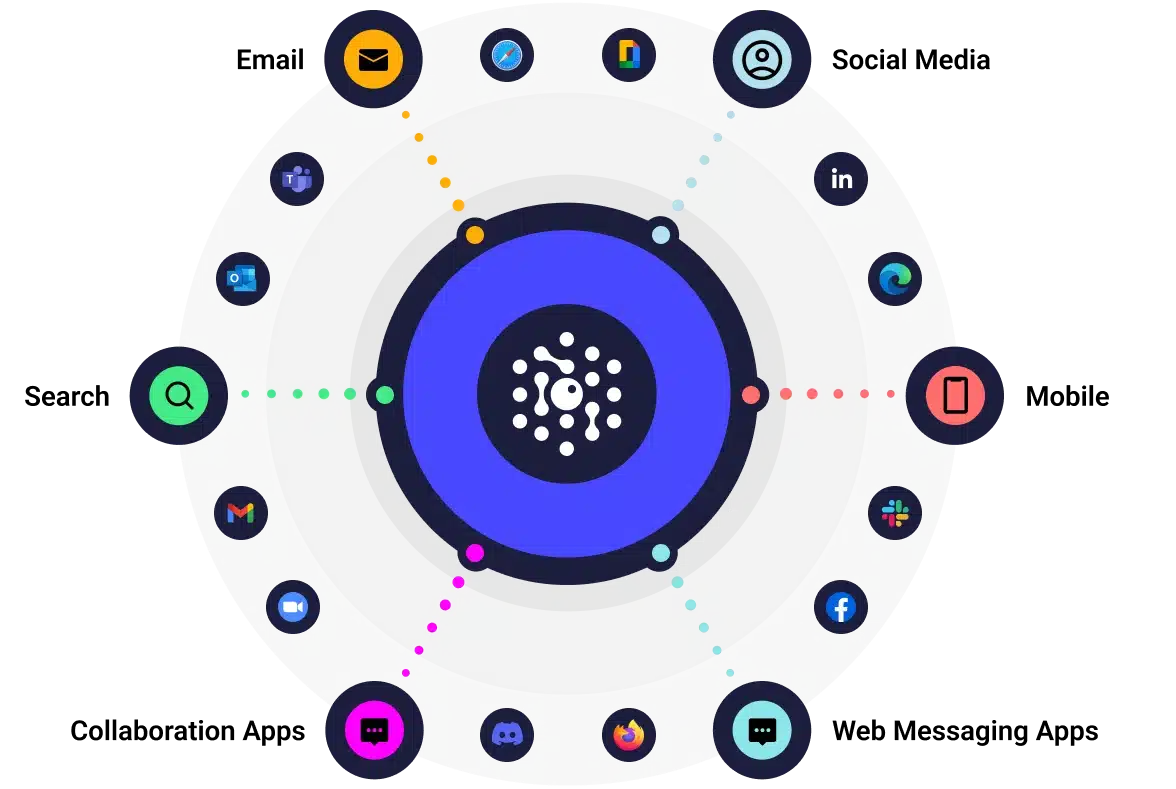
Powerful Multi-Channel Protection
Integrated browser extension stop zero-hour link and exploit threat in all web messaging apps, including email, ads, social media, search, collaboration platforms, and more.
By blocking malicious sites in real-time, SlashNext protects users from more zero-hour threats including those that evade multi-layer enterprise defenses.
Enterprise Level User Experience
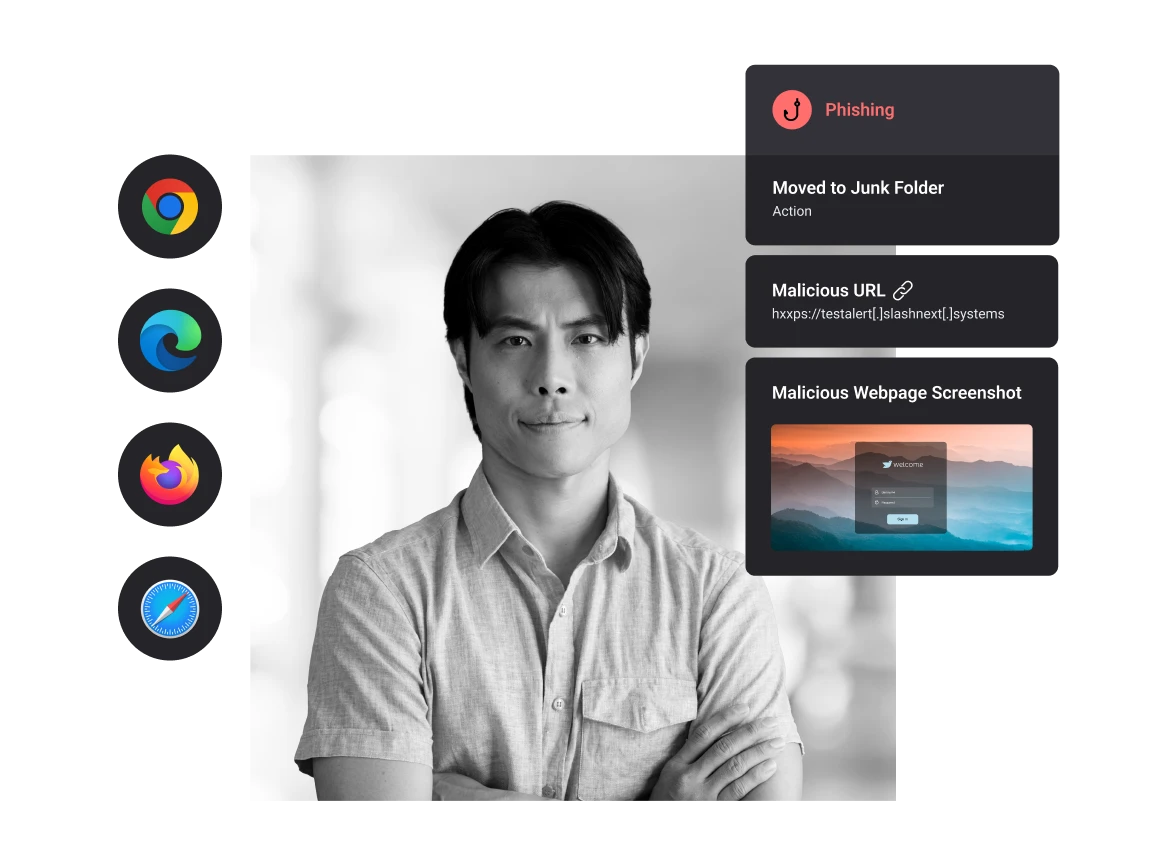
State-of-the-art protection is just the start. SlashNext also provides an enterprise-grade user experience, including:
- Safe preview of the blocked malicious site with helpful threat information to educate users
- With TLS 1.3 and DNS over HTTPS (DoH) SlashNext Browser Security operates within browser memory and blocks URLs pre-encryption.
- Ability for users to submit a report ticket about the incident
- Available for all major browsers: Chrome, Edge, FireFox, and Safari.
- Easily deployed and managed via leading UEM solutions. It also integrates with leading SSO solutions for simpler user provisioning and management.

Fast Deployment and Accessibility
Easily deployed and managed via leading UEM solutions, as well as integration with leading SSO solutions for simpler user provisioning and management.
Available for all major browsers including Chrome, Edge, FireFox, and Safari.
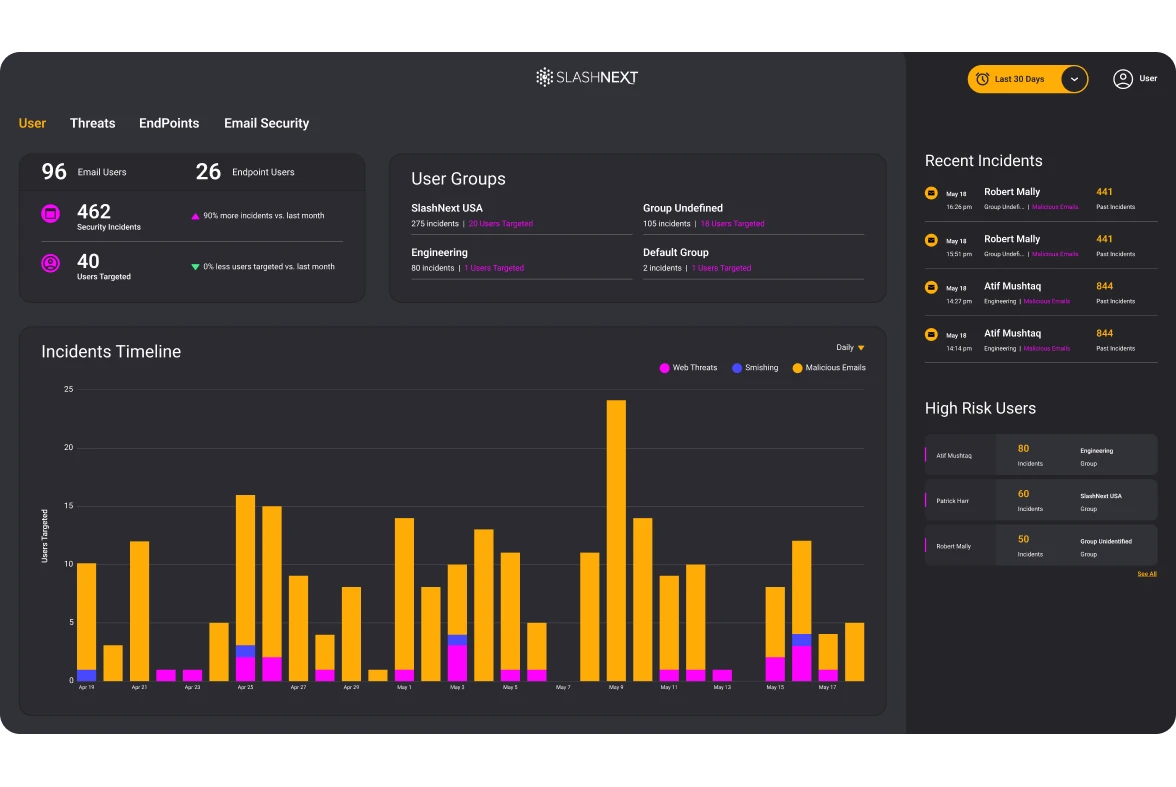
Full Visibility and Reporting
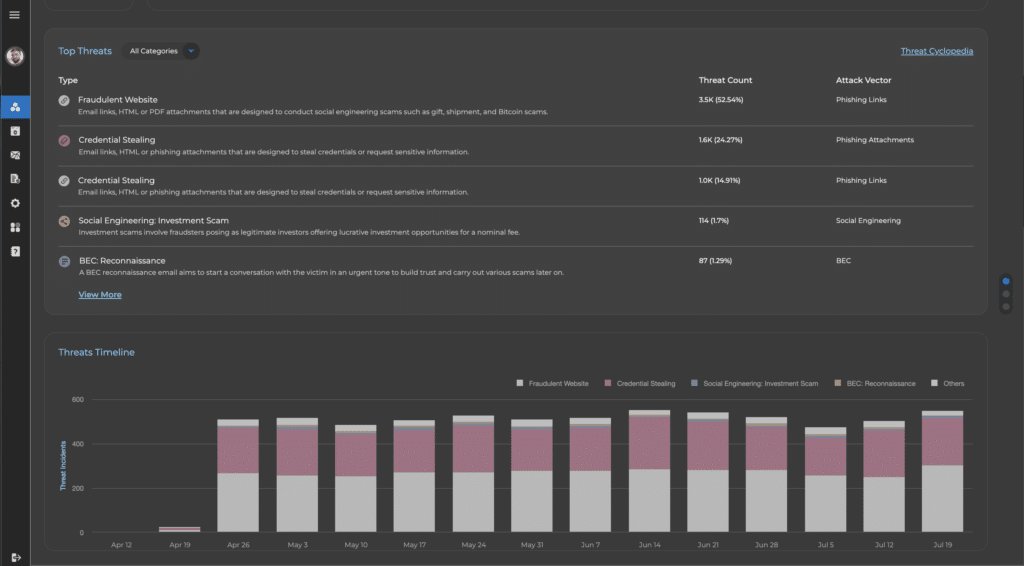
SlashNext’s elegant cloud management console enables simple deployment, management, and advanced reporting across threats, users, and devices.
Advanced reporting and analytics features include filters to view data by threats, endpoints, and users for a full view across the enterprise. Drill-down into high-risk users, timelines, and detailed forensics information. Automate daily or weekly reporting, including incidents and executive summaries.

Engineering Firm Closes Messaging Security Gaps Outside Email


Hackers are getting better at this every day, so we have to get better as well. We can continue to educate, but the statistics, still show that even the best educated companies out there still have about a 4% failure rate of people clicking on stuff.
SlashNext User
SlashNext Delivers Best in Class Results on Day One
5 mins.
Protected in minutes with quick deployment via browser extension
99.9%
Detection rate with 1 in 1 million false positives
2x more
Blocks two times more than competing solutions
>1 hr.
Instant spear phishing protection, on-device ai and url threat intelligence
Zero
Zero-latency, real-time protection
48 hrs.
Detection advantage vs other threat intelligence engines
Related Resources

FEATURED DATA SHEET
Browser Phishing Protection
Anywhere Zero-Hour Protection Against the Broadest Range of Phishing Threats available for all major browsers including, Chrome, Edge, FireFox, and Safari.

Featured Blog
The State of Phishing 2023
FEATURED WHITE PAPER
Microsoft 365 + Integrated Cloud Email Security
Due to the demands of the modern workforce, there has been an exponential shift in the use of native cloud email protection capabilities, like Microsoft 365, in the last 12 months.
See SlashNext Complete™
in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.


