Real-Time Phishing Defense APIs
Powerful AI machine learning APIs designed to protect the brand and reputation of corporate, internet, messaging, hosting and all other cloud services from advance phishing threats worldwide.
( Powered by Project Phantom.)

Detection at Scale with Real-Time Phishing Defense APIs

RTPD Lookup and Live Scan APIs
High volume real-time threat intelligence lookup, plus dynamic live scanning in milliseconds to detect and block zero-hour phishing threats at speed and scale.

RTP Forensics API
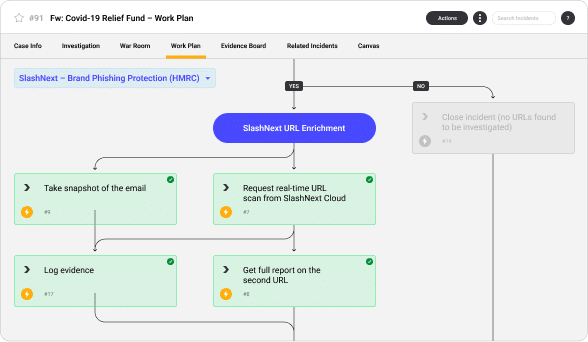
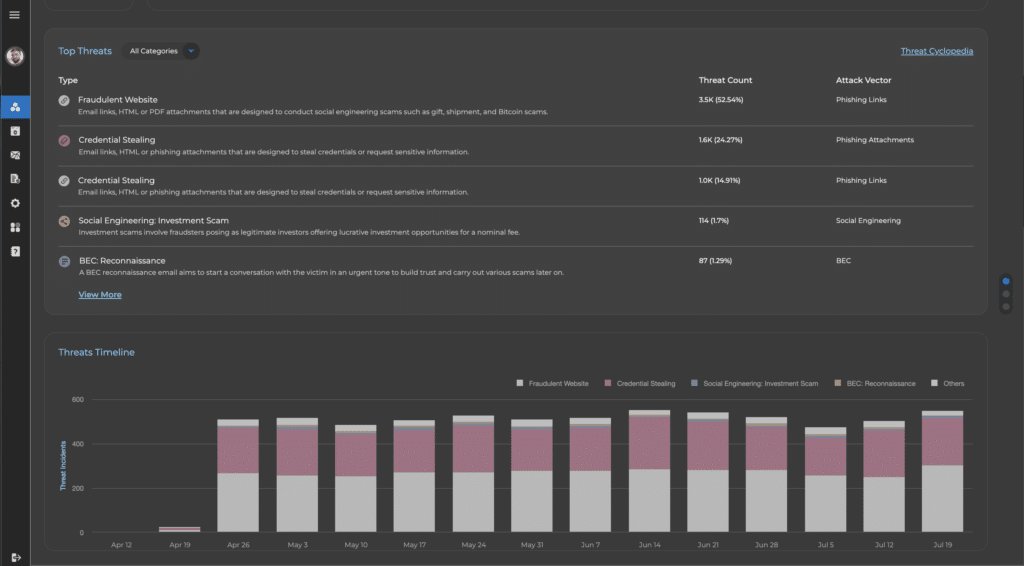
Save Thousands of Hours of Security Analysts Time with Playbooks and Integrations
Brand and Reputation Protection
Stop threat actors from leveraging legitimate SaaS services like internet, messaging, hosting, and all other cloud services by automating the detection and removal from advance phishing threats.
Threat Investigation and Hunting
Save SOC analyst time with real-time phishing forensics to automate threat hunting, to detect unknown threats and receive continuous real-time updates with IoCs on the latest emerging threats.
Abuse Inbox Management
Simplify and expedite abuse inbox management and phishing incident response to dramatically reduce the time associated with researching suspicious URLs.
URL Analysis and Enrichment
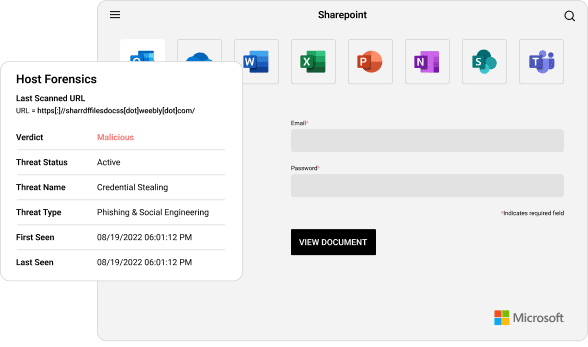
Enriches URLs with a definitive verdict plus forensics data, including screenshots, HTML, and rendered text combined with reporting artifacts. This simplifies phishing IR processes and reporting.
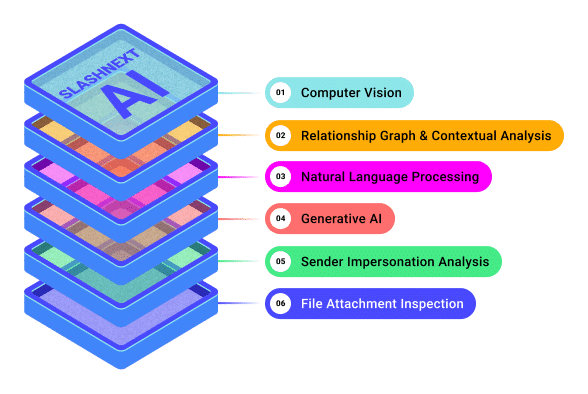

Stop The Attacks That Impact Your Business

Social Engineering, Scams and Fraud
Deception to manipulate users into divulging information for misuse.

Trusted Services Compromise
Uses trusted domains to obfuscate cyber attacks to increase success.
Ransomware, Malware and Exploits
Intended to inject code, take-over browser canvas or download malware.

Malicious Attachments
Malicious HTML, PDF and Office files used to harvest credentials or download malware.

BEC, ATO and Supply Chain Attacks
Targets execs or financial teams to defraud a company for financial gain.

Credential Stealing
Cyber attack designed to steal passwords with the intent of accessing protected data.
Spear Phishing
Personalized targeted attack designed to trick users into a data breach or for financial gain.
Smishing and BTC
Using SMS text messages to trick users into divulging passwords or other PII for fraudulent use.
A Multi-National Media and Publishing Power-House Prevents Threat Actors from compromising their SaaS Platform
Challenged with stopping threat actors who subscribe to their low-cost SaaS services to host phishing URLs. SlashNext APIs can proactively detect these threats prior to publishing and provide the full details of the threat including screen shots and meta data as evidence to take down the malicious pages.
“SlashNext phishing detection API is very useful and easy to use integrated service. It helped us improve our existing phishing detection algorithms with a significant added value.”
Malicious sites identified
Site Takedowns in first 48 hours
Detection rate
Faster detection with live-scan

SlashNext phishing detection API is very useful and easy to use integrated service. It helped us improve our existing phishing detection algorithms with a significant added value.
SlashNext User
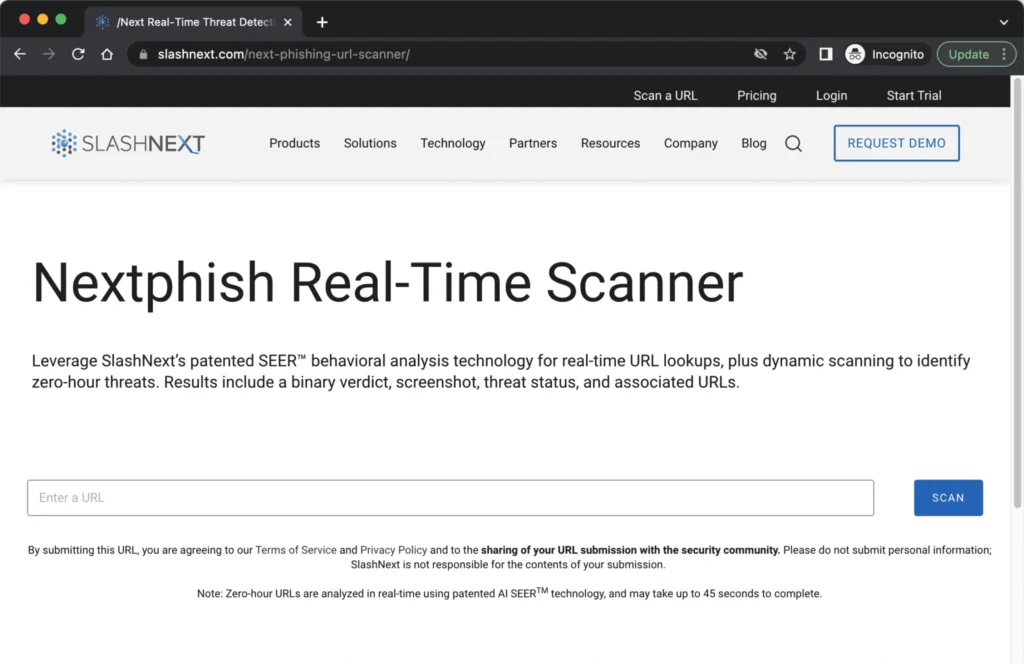
Try Our Enterprise-Level Threat Detection
We have developed NextPhish to allow anyone to access our high-volume real-time threat intelligence lookup, and live scanning to check a suspicious URL.
See SlashNext Complete™
in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.