Pandora hVNC is a remote access trojan (RAT) that has been advertised on cybercrime forums since 2021. Surprisingly, it has received little attention from the cybersecurity community. Despite this, it remains a widely used tool and is favoured by many threat actors. Pandora hVNC enables attackers to gain covert control over a victim’s computer. This article will analyse the features of Pandora hVNC.
Pandora hVNC is a type of malware known as a remote access trojan (RAT). As the name suggests, a RAT allows an attacker to gain unauthorised access to a victim’s computer and control it remotely.
Pandora hVNC was initially advertised in 2021 or possibly earlier. However, it has not received significant attention, likely because of its marketing approach and the terms of service established by the seller in the sales thread – as you can see in the image below, the seller is attempting to present Pandora hVNC as a legitimate remote access tool.

Image: The terms of service that have been published on the official Pandora hVNC sales thread
In lower-tier cybercrime forums, there is a widespread belief that selling software with a disclaimer absolving the author of any criminal damage and claiming it is designed for legitimate purposes, allows the author to avoid prosecution if it is in fact used maliciously.
An example of this is the Netwire RAT which was shutdown in March 2023 by authorities – they also claimed to be a legitimate piece of software.
However, in the case of Pandora hVNC, it is slightly more obvious that this is just a ploy and the tool is designed for malicious use. The author advertises the software on well-known cybercrime forums.
On the first forum where we found the software, it has received over 26,000 views. By examining the sales thread, anyone familiar with the cybercrime landscape can deduce that the software is most likely being used as a remote access trojan, rather than a remote access tool.
The Seller of Pandora hVNC
Throughout the sales thread, the Pandora hVNC seller is seen advising potential or existing customers on the most suitable type of crypter to use with their software.
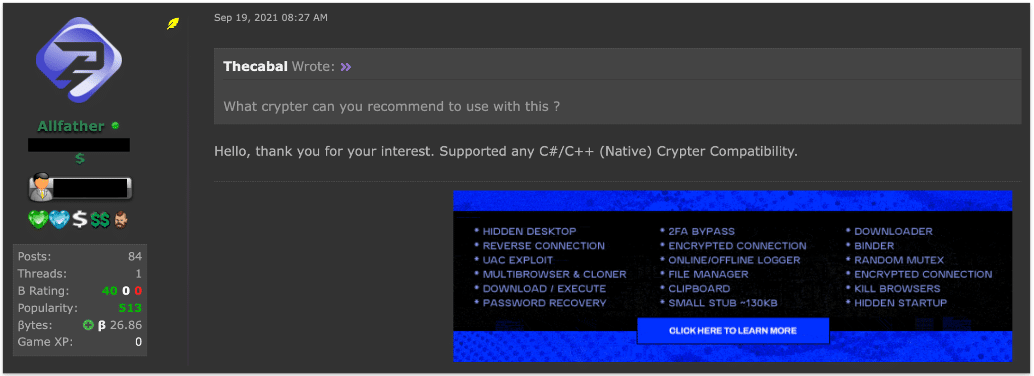
Image: The seller of Pandora hVNC advising what crypters are compatible with the software
A crypter is a type of software that is capable of encrypting, obfuscating, and manipulating malware to make it harder for security programs to detect.
There’s no reason to run a crypter on any software in the context discussed in the sales thread for legitimate purposes. Additionally, throughout the sales thread, users refer to clients infected with this software as ‘victims’.
Image: A user of Pandora hVNC referring to a client as a victim
When you consider the points above, and the fact that the software features a ‘keylogger,’ it’s only logical to conclude that this software was created with malicious intent.
The Pandora hVNC Feature List
Here’s an extensive list of features that come with Pandora hVNC. We’ve added our own descriptions to each feature for easier comprehension. In the official advertisement thread, the seller simply lists the name of each feature.
Scale Resolution: This enables the hacker to adjust the resolution of the victim’s screen to fit their own, facilitating easier control and monitoring.
WebGL Support 100%: Ensures compatibility with modern web technologies, allowing the hacker to interact with complex web applications on the victim’s system.
Hidden Desktop: This allows the attacker to control the victim’s system without any visible signs of intrusion, making detection more difficult.
Reverse Connection: In this method, the victim’s computer initiates the connection to the attacker’s system, which can often bypass firewall restrictions.
Lightweight TCP Server: This feature helps establish a low-latency, reliable connection between the attacker and the victim’s system.
IPV4 / DNS Support: Ensures compatibility with most network configurations.
Access to all applications / Mouse & Keyboard Controls: Allows the attacker to interact seamlessly with the victim’s system as if they were the user.
Encrypted Connection: All communications between the attacker and the victim’s system are encrypted, making detection and analysis by network monitoring tools more difficult.
Browser Profile Cloner Session/ Cookie/ Password/ History: This feature enables the attacker to clone the victim’s browser profile, providing access to sensitive information like saved passwords, browsing history, and cookies.
Process Suspension: Allows the attacker to suspend processes on the victim’s computer, potentially disrupting security software or other applications.
2FA Recovery Bypass (If 2FA App is installed): If the victim uses two-factor authentication (2FA), this feature can potentially bypass it, providing the attacker with access even to accounts protected by 2FA (note that there is some skepticism surrounding this feature though).
CMD/PowerShell Prompt: Provides the attacker with command line access to the victim’s system, allowing them to execute commands directly.
C#/C++ (NET/Native) Crypter Compatibility: Ensures compatibility with commonly used methods for obfuscating malicious code to evade detection by antivirus software.
Reflective Stub Injection (Memory Only, No Disk): This technique loads malicious code directly into memory, bypassing the need for writing to disk and evading many types of antivirus detection.
Quality Adjustment & Image Resize of hVNC: Allows the attacker to adjust the quality of the remote desktop view to account for different network conditions.
Client Information/Note: Provides a way for the attacker to keep track of information about the victim’s system.
hVNC Panel: Offers various controls for the attacker to manage the victim’s system, including monitoring system performance (CPU, RAM, Disk, GPU, Network usage), controlling the screen refresh rate, and more.
Task Manager: Equips the attacker with the ability to manage processes on the victim’s computer, including killing, restarting, and searching for specific processes.
File Manager: Allows the attacker to manage files on the victim’s system, including copying, pasting, deleting, uploading, downloading, renaming, and executing files.
Password Recovery: This feature can extract saved passwords from various web browsers installed on the victim’s system, providing the attacker with access to the victim’s online accounts.
Client PC: Allows the attacker to restart or shut down the victim’s computer.
Download and Execute: This feature allows the attacker to download additional malicious files from a specified URL or disk location and execute them on the victim’s system.
Keylogger: Records the victim’s keystrokes, capturing potentially sensitive information such as passwords and credit card numbers.
The Dangers of Pandora hVNC
It is crucial that we understand the potential harm that can come from the use of Pandora hVNC. This remote access tool allows cybercriminals to secretly take control of victims’ computers, enabling activities like data theft, espionage, and unauthorised access to sensitive systems. That access can then be sold to other cybercriminals to carry out more impactful attacks, like the deployment of ransomware.
In the 2009 GhostNet operation, a vast cyber espionage network targeted the political, economic, and media sectors of over 103 countries. Believed to be associated with China, the attackers delivered RATs through phishing emails that functioned similarly to Pandora hVNC to access victims’ computers. This allowed surveillance of users and access to sensitive files.
As mentioned previously, it is surprising that Pandora hVNC has not received more attention in the cybersecurity world given its capabilities. The most logical explanation seems to be the developer’s disclaimer that it was intended only for legitimate use.
At one point, the seller tried promoting the tool on a large Russian hacking forum. However, some users ridiculed the inclusion of a disclaimer, seeing it as rather silly.
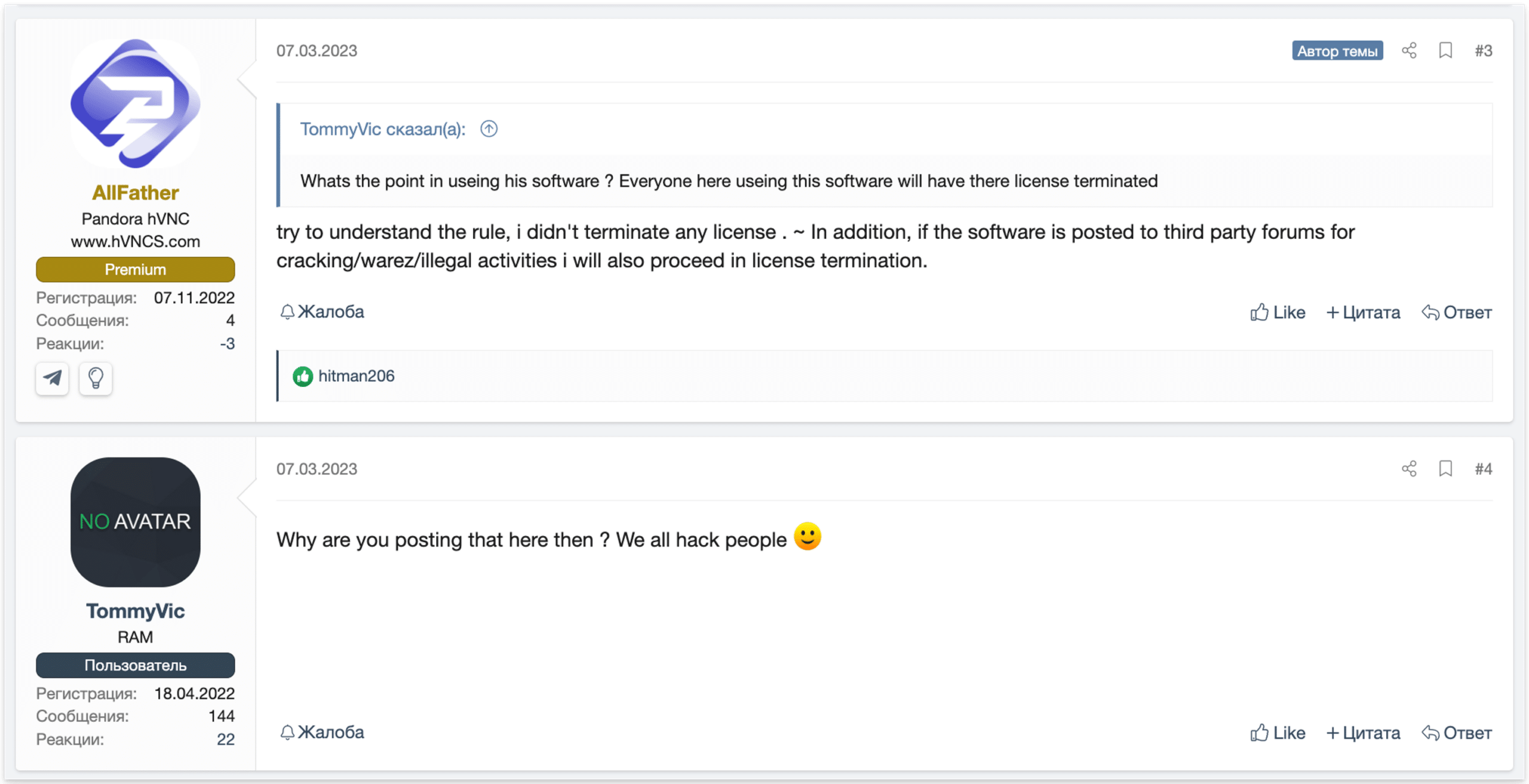
Image: The seller of Pandora hVNC being mocked on a Russian cybercrime forum
The seller responded by stating that they should “try to understand the rule,” clearly implying the disclaimer is included only to protect themselves, not because Pandora hVNC actually prevents misuse. In reality, it has no built-in safeguards to stop someone from infecting thousands of computers. And without specific reports, there is no way for the developer to know who might be misusing the software, even if they wanted to take action.
Our conclusion is that Pandora hVNC is clearly designed for malicious purposes. It has no safety features built in, users can pay anonymously with cryptocurrency, the tool is exclusively promoted on forums associated with cybercrime, and the seller is fine with people referring to infected machines as “victims”.
Indicators of Compromise (IOC)
| Indicator | Type |
| 39ef11e7673738d7dab6b7396044d003 | MD5 Hash |
Your Next Steps With SlashNext
Pandora hVNC, often delivered through phishing, is countered effectively by SlashNext Complete. This platform secures email, mobile, and web communications, especially in Microsoft 365, Zoom, Teams, and Slack.
It employs SlashNext’s Gen AI platform, which is purpose-built to anticipate the vast numbers of malicious links and zero-hour exploits with high accuracy by combining natural language processing, computer vision, and machine learning with relationship graphs and deep contextualization. Click here to schedule a demo or compare it with your current email security for 30 days using our 5-minute setup Observability Mode.