SlashNext Blog
Phishing, social engineering, and modern threats.
Featured Article
Five Ways Spear Phishing Tactics are Evolving in 2025
What type of phishing became very effective around 2010 and still worries security teams today? Spear phishing. Spear phishing remains highly effective and is getting more dangerous by the day. What is spear phishing? What new technologies and methods will attackers use to get around common defenses? How will they become more precise and convincing? […]
Featured Article
10 Ways URL Analysis & Enrichment Can Help Ease Your SOC’s Challenges in 2020
On-demand phishing URL analysis solutions can help ease your SOC teams’ pain and challenges.
Blog Subscription

Five Ways Spear Phishing Tactics are Evolving in 2025
What type of phishing became very effective around 2010 and still worries security teams today? Spear phishing. Spear phishing remains highly effective and is getting more dangerous by the day. What is spear phishing? What new…

Blov HTML Crypter: Phishing Evasion Through Encryption and Obfuscation
Cybercriminals are sharpening their phishing tactics with tools like Blov HTML Crypter — a utility that modifies HTML files to evade detection by security scanners. By employing techniques such as minification, encryption, and …

Government Agency Spoofing: DocuSign Attacks Exploit Government-Vendor Trust
The latest wave of DocuSign attacks has taken a concerning turn, specifically targeting businesses that regularly interact with state, municipal, and licensing authorities. Since November 8 through November 14, we have observed…

GoIssue – The Tool Behind Recent GitHub Phishing Attacks
We recently uncovered GoIssue, a tool marketed on a cybercrime forum that allows attackers to extract email addresses from GitHub profiles and send bulk emails directly to user inboxes. GoIssue signals a dangerous shift in targ…

New Anti-Bot Services on the Dark Web Help Phishing Pages Bypass Google’s Red Page
Novel anti-bot services are being advertised on the dark web, offering cybercriminals advanced tools to bypass Google’s protective ‘Red Page’ warnings in a concerning development for cybersecurity teams. These…

The Hidden Risks of URL Rewriting and the Superior Alternative for Email Security
URL rewriting, a service designed to neutralize malicious URLs by redirecting users to a safe environment, has been a common practice in email security. However, as cyberthreats evolve, it’s becoming clear that this appro…

Project Phantom: Revolutionary Zero-Trust Virtual Stealth Browser URL Analysis that’s Changing th...
In the ever-evolving landscape of cybersecurity, the cat-and-mouse game between defenders and attackers never ends. At SlashNext, we’ve been at the forefront of this battle, constantly innovating to stay ahead of sophisti…

Unmasking the Sophisticated: How AI-Powered Defenses Thwart Advanced Phishing Attacks
Attackers are constantly refining their techniques for advanced phishing attacks to exploit the trust inherent in our digital systems. A recent incident we’ve captured highlights the alarming sophistication of modern phishing a…
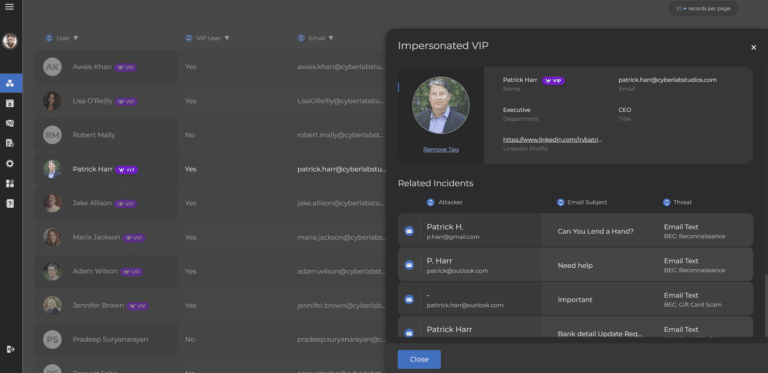
Revamping Email Security: Introducing SlashNext’s Enhanced Administration Portal CMS
In today’s fast-paced digital landscape, ensuring robust email security while maintaining operational efficiency is paramount. At SlashNext, we are dedicated to providing cutting-edge solutions to keep your organization secure …
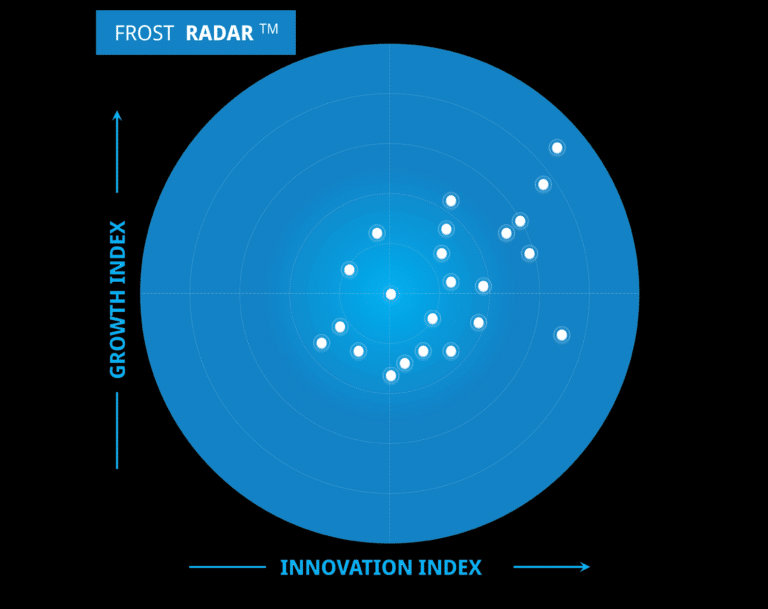
Thawing Your Email Security Strategy with Frost’s 2024 Radar Report: A Dynamic Cyber Threat Lands...
In today’s digital age, email remains the primary conduit for business communication, making it a prime target for cybercriminals. The Frost Radar Research Report on Email Security for 2024 underscores the critical import…

CISA Issues Warning: CrowdStrike Outage May Lead to Phishing and Malware Attacks
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding the recent CrowdStrike outage, warning that malicious actors are actively exploiting the situation to conduct phishing and other c…

New FishXProxy Phishing Kit Lowers Barriers for Cybercriminals
Imagine receiving an email that looks perfectly legitimate, down to the last detail. This is the deceptive power of new FishXProxy Phishing Kit, a new phishing toolkit emerging from the cybercrime underground. With its array of…
It’s Time to Get Started with SlashNext
Learn how to leverage the industry’s best zero-hour phishing protection in your environment.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.


