Automate Online Brand Protection
Simplify and expedite online brand protection by automating the takedown of malicious brand content in less time.
The Challenge
Attempts to fraudulently use or impersonate a brand is an extensive and severe problem for brands. Most brands have abuse inboxes for the public to report suspicious communications. This is a complex and manual operation for global brands that require brand protection teams to sort through thousands of malicious and benign emails daily, gather forensics evidence, and send take-down requests to the domain or other organizations hosting the malicious content.
The SlashNext Solution
Fully automate the process of reviewing emails sent by customers and the public to online brand abuse inboxes. Detect brand impersonators and malicious URLs using deep inspection of website content and packages everything required to request a take-down (IOCs, forensics, and screenshots) into an email sent to the abuse department to simply forward to the domain registrar.
SlashNext solves these problems by providing accurate phishing URL analysis on-demand and at scale. SOC and IR teams can now leverage an automated phishing URL analysis service that provides accurate, definitive results and enrichment to speed execution of phishing IR playbooks, analysis, and reporting. Together with pre-built integration apps for leading SOAR platforms, SlashNext dramatically reduces the time, effort, and costs involved in phishing IR.
Rapid Identification
Real-time identification of genuine phishing emails.
Reduce False Results
Reduce work and risk associated with false negatives and false positives.
Improve Productivity
Free up your IR team from doing costly manual research.
Save Time and Money
Dramatically reduce the time and costs associated with researching suspicious URLs.
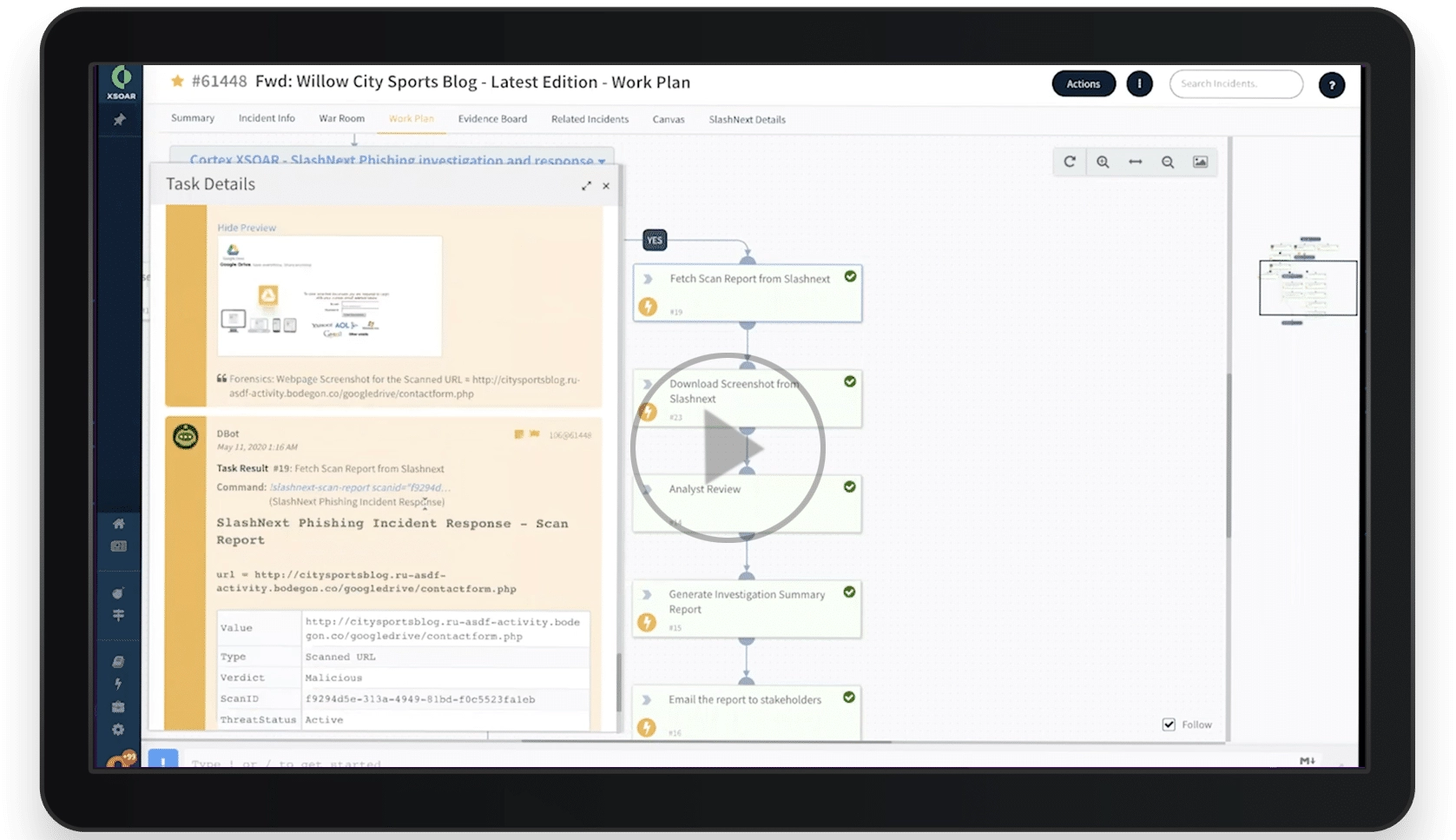
How it Works
Here’s an example phishing IR playbook for abuse inbox management. Pre-built integrations with leading SOAR platforms provide quick and easy operationalization of SlashNext Phishing URL Analysis & Enrichment.

Extremely Accurate Playbook
SlashNext’s threat detection technology that uses mature machine learning (computer vision, NLP, and OCR) and virtual browsers to dynamically inspect page and server behavior with 99.07% accuracy. This speeds-up the process of taking down malicious sites targeting your organization right now and in the past. With this playbook, teams will save hundreds of hours spent per week managing corporate brand abuse inboxes.
Brand Protection Playbook Includes:
- Extract URL from the reported email and take snapshot of the email
- Request real-time scan through SlashNext SEER Cloud (to be analyzed by a virtual browser)
- Download URL Scan Report including website screenshot, HTML and rendered text and log evidence
- Perform a deep inspection of the HTML to find If Phishing URL is targeting the Brand
- Gather forensic analysis says and get domain Whois information
- Prepare complete evidence to be shared with hosting providers and domains registrars (includes URLs, phishing email and website screenshots) and dispatch a take-down email to concerned abuse department
SlashNext Stops Human Hacking Across All Digital Channels
Best
Detection
99% detection rate and 1 in 1 million false positives.
Guaranteed User Privacy
No personal data transmitted.
URL
Enrichment
With forensics, including screenshots, HTML, and rendered text.
Zero-Touch, Immediate Time to Value
Deploy in minutes. Automated updates.
See SlashNext Complete™ for Email, Mobile and Browser in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.


