Back in the 1930s, March Madness was used to describe the excitement and frenzy surrounding an Illinois high school basketball tournament. Over the years, the term has become associated with the frenetic NCAA (National Collegiate Athletic Association) Men’s Basketball Tournament, which starts this week throughout the country.
The highly anticipated Madness features 68 college teams fighting for a championship in a single-elimination tournament with a sole winner crowned at the end of the three-week tournament. It’s intense, exciting, upsetting, and unpredictable for its 18 million fans.
As always, there will be plenty of surprises and upsets. Many brackets will be busted early in the tournament, much to fans’ chagrin. A downsi>de to March Madness, which is also unpredictable, unexpected, and extremely upsetting, is the ever-increasing number of phishing attacks associated with the event. Having a bracket disappointment is nothing compared to falling prey to a phishing scam that turns into an organization’s data breach, which is what happens often.
In VMblog.com this week, it was noted that what makes March Madness most interesting is that “it’s the only major sporting event in the US that traditionally falls during our business day, and those who take part in viewing and playing in their ‘office pools’ are susceptible to a variety of security threats, especially those dreading phishing lures.”
Again, emotions run high during the March Madness tournament and hackers are quick to take advantage of the predictability of fans falling prey to malicious content that leads to data breaches. With money on the line for many employees participating in office pools and brackets, hackers serve fake sporting-themed websites, free streaming of games, private VPNs, contests, and browser extensions that claim to keep track of scores and stats of the games.
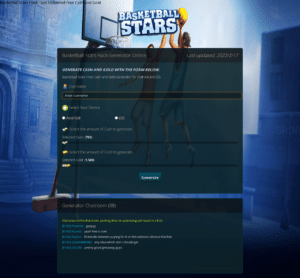
Many threat actors use social engineering tactics through business email compromise (BEC) attacks by sending emails (or SMS texts) to an employee, hoping they will click on a link that may take them to a malicious site such as the one in the image below, and eventually exploit their actions for credential stealing and ultimately a breach. These sites look legitimate, which is why cybercriminals are so successful during big events like March Madness, and with 82 percent of breaches involving an end-user, it’s important to be vigilant.
There are many common March Madness social engineering techniques used for phishing attacks and data breaches including:
- Fake Bracket Scams: Cybercriminals create fake March Madness brackets or contests to trick people into giving away personal information or downloading malware.
- Ticket Scams: Scammers create fake ticket offers for March Madness games or events, asking for payment in advance, but not delivering the promised tickets.
- Charity Scams: Scammers set up fake charity organizations related to March Madness, asking for donations from unsuspecting people.
- Betting Scams: Cybercriminals create fake betting sites for March Madness, tricking people into depositing money and not allowing them to withdraw their winnings.
The sophistication of these phishing threats is becoming more difficult to detect, especially for users. March Madness-themed phishing sites are popping up to steal credentials for future corporate-based attacks or to commit credit card fraud.
We’re catching many websites from prolific cyber-gangs. The end game for these cybercriminals is credit-card fraud and other malicious activities. They use realistic-looking pages and social engineering techniques hoping to attract victims getting caught up in the excitement and gambling that goes along with March Madness.
So, what can you do to help stop your employees from getting caught up in a phishing scam and wreaking havoc on your network? Here are several items to address.
It’s important to educate your employees about the risks of engaging with content from unknown sources, but keep in mind that threats are so sophisticated that you can’t rely on identifying threats with training. Training doesn’t help. These are advanced threats that cannot be found through training. They are on legitimate sites or from familiar users who have had a compromised account.
Be proactive in securing BYOD. With the increased use of BYOD and dual-purpose devices, it’s important to avoid giving away login credentials or accidentally adding malicious browser extensions that can be used to breach corporate assets.
Protect your organization by encouraging users to exercise extreme caution when taking part in brackets and office contests. Most importantly, implement the right security tools, including real-time mobile and browser security solutions.
When completing a bracket, make sure employees know that they should only supply the basics of personal data. There is no need to supply anything more than a name and email address. If any personally identifiable information (PII) or financial data is asked, it should send up an immediate red flag.
Use security defenses that use real-time detection. Many of the phishing sites today stay live for hours (not days) – just enough time to wreak havoc on your network, but not enough time for traditional network security tools to do their jobs.
Use a product like SlashNext, which offers the first Generative HumanAI™ solution to detect and prevent threats before they become a breach. Our patented technology uses generative AI, relationship graph, contextual analysis, natural language processing, and computer vision to detect zero-hour threats, including those on legitimate and compromised sites.
HumanAI™ detects the most evasive zero-hour threats in real time with LiveScan™ to protect cloud email as well as all other messaging channels with 99.9% accuracy. Your organization benefits from threat detection for complete protection over cloud email, mobile, and web messaging apps to stop attacks that include smishing, credential theft, ransomware exploits, and more.
Don’t let the phishing madness get to you and your organization! And good luck on your March Madness bracket!
See a Demo or Test Your Email Security via Observability Mode
To see a personalized demo and learn how our product stops zero-hour business email compromise (BEC), supply chain attacks, executive impersonation, malware, exploits, financial fraud, and more, click to schedule a demo or easily test the efficacy of your current email security with no impact to your existing email infrastructure using our 5-min, easy setup Threat Observability Mode!