
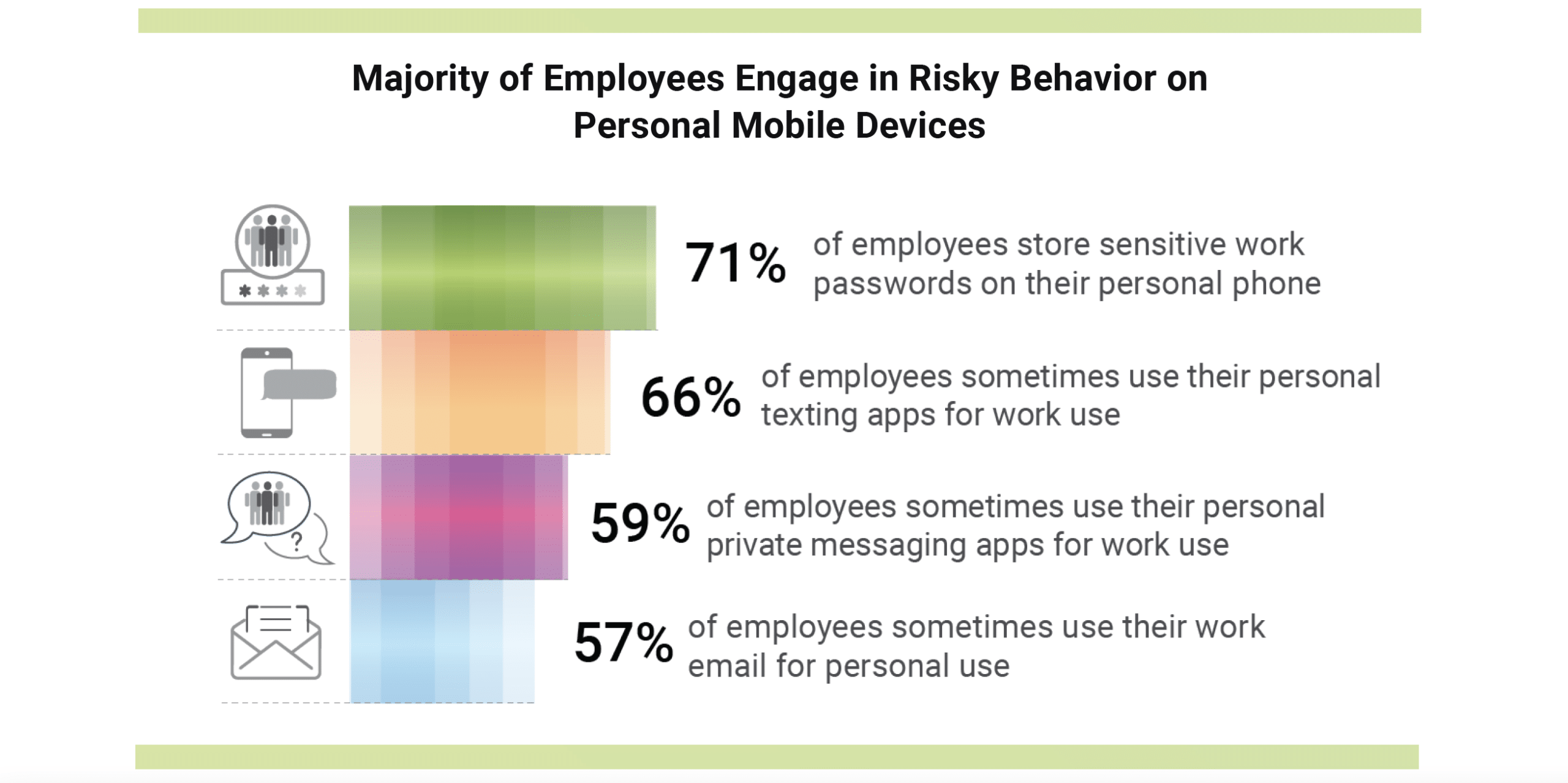
The rising trend of employees using personal devices for work has cybercriminals directing focus towards mobile devices for launching attacks. The lack of security protection and accessibility of sensitive information on these devices have made them enticing targets for hackers. The utilization of personal devices for work introduces security vulnerabilities since employees may not prioritize device protection as they would with a company-issued device. Mobile device users often rely on factory security settings instead of enhanced security software compared to desktop computers, and mobile operating systems are frequently not updated, leaving devices vulnerable to exploitation. The surge in mobile device usage for online banking, shopping, and other activities has also expanded the pool of potential victims, further enticing cyber criminals seeking to access sensitive information. Moreover, users are engaging in risky behavior with 71% of employees storing sensitive work passwords on their personal phones. Considering these circumstances, it is imperative for both employees and employers to take proactive measures in safeguarding mobile devices and the valuable information they store.
Employers confronted with employees using personal mobile devices for work encounter a range of additional obstacles. One such challenge lies in the enforcement of company policies and procedures on these personal devices, as well as the assurance that these devices are regularly updated and maintained in adherence to security best practices. There are legal and compliance concerns regarding the storage of sensitive data on personal devices, particularly in the event of device loss or theft. In addition, issues may arise concerning data ownership and access, particularly when employees depart the company or transition to different roles within the organization. In light of these complexities, it is increasingly crucial for employers to establish a comprehensive strategy that effectively manages the use of personal devices in the workplace while ensuring the security and privacy of sensitive data.
Balancing the need for data security with respect for employee privacy can be a challenging task. Securing corporate data and maintaining employee privacy are valid and reflect the complex nature of the modern workplace. 85% of employers require work-related apps to be installed on personal devices of employees. Employees, therefore, are required to install work-related apps on personal devices, and this has become a common practice. It allows employees to use their personal devices for work purposes, which can enhance productivity and convenience. However, it can also pose security risks and potentially infringe on employee privacy.
Employers need to implement appropriate security measures to protect corporate data while respecting employee privacy. 90% of IT leaders say protecting employees’ personal devices is a top priority, but only 63% say they definitely have the tools to adequately do it: . The IT leaders’ concern for protecting employees’ personal devices is understandable. Personal devices may not have the same level of security as company-owned devices. Implementing effective security measures on personal devices can be challenging because of the diverse range of operating systems, device models, and user preferences. IT leaders need to invest in robust security solutions that can adequately protect corporate data while minimizing potential privacy concerns.
With the expansion of today’s threat landscape to mobile, security awareness training, is not enough to keep employees and corporate data safe. To protect employees and corporate data in today’s evolving threat landscape, security plans must include BYOD mobile devices policies. Employers should implement strong AI phishing controls that cover various phishing attacks while respecting employees’ privacy.
For more information on the Mobile BYOD threat landscape and protection solutions, read The Mobile BYOD Report, available at this link: /report-the-mobile-byod-security-report/


