
Phishing attacks have moved beyond simply sending emails with malicious links to incorporate more modern social engineering techniques, including the alarming trend of mixing in smishing (SMS phishing) and vishing (voice phishing). These techniques are a growing threat beyond email security and enhance cybercriminals’ capabilities to achieve their objectives using this new range of communication techniques. This article describes phishing, smishing, and vishing in detail and provides an example attack chain.
1) Phishing and Smishing – The Foundation
Phishing and vishing attacks often begin with cybercriminals using pre-existing databases of stolen or leaked information to target victims. These databases, commonly available on the dark web or through underground marketplaces, provide attackers with verified email addresses and phone numbers.
By using this information, attackers can launch spear-phishing campaigns with precision, creating highly convincing, personalized attack messages. This approach is often used in business email compromise (BEC) attacks, where fraudsters use tactics like email spoofing to impersonate legitimate contacts or executives.
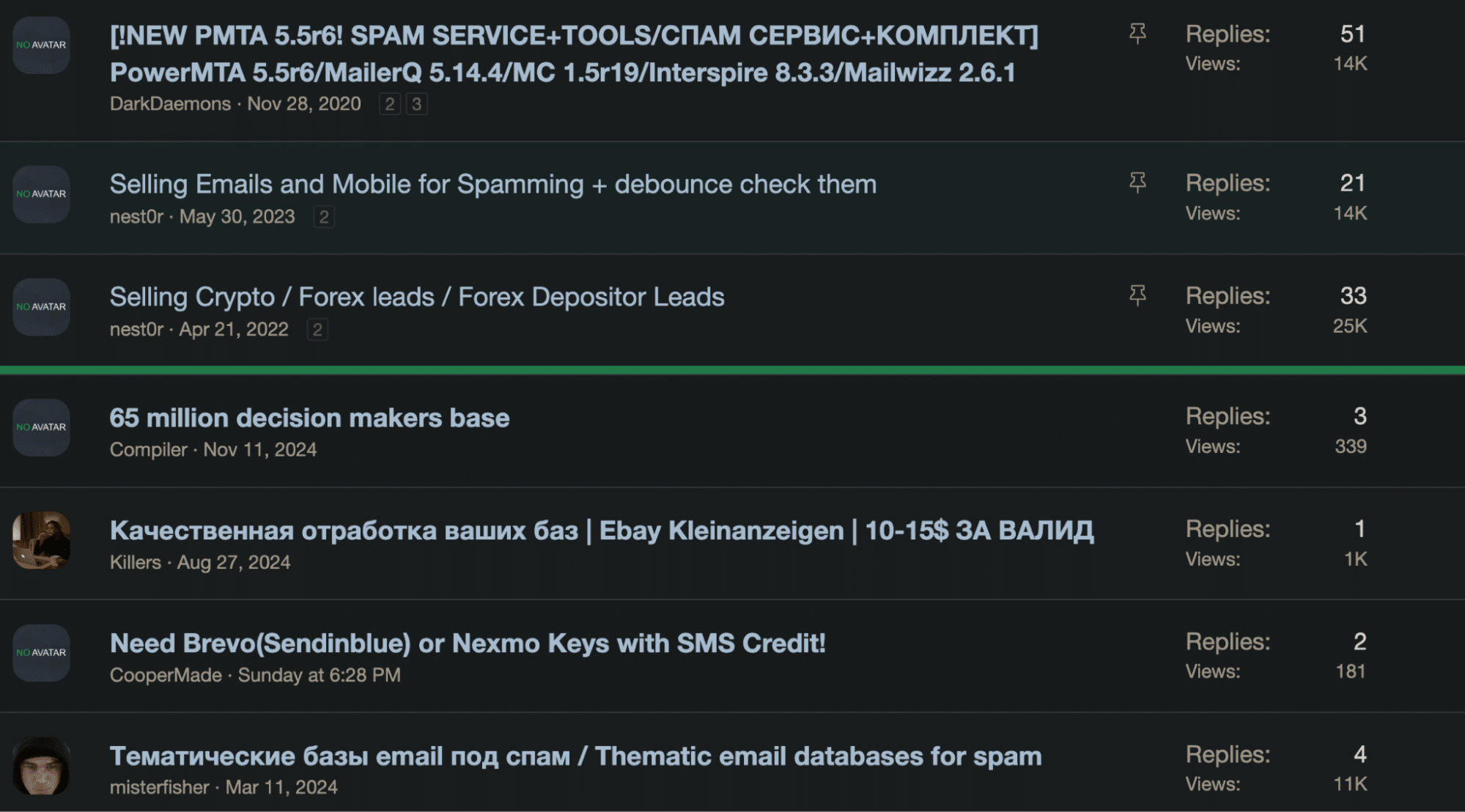
Smishing (SMS phishing) starts off with a similar tactic but utilizes text messages to target victims. With concise and urgent messages, attackers prompt individuals to act quickly, often by telling them to click a link to “resolve” fabricated issues like unauthorized transactions. The phone numbers from leaks make this process efficient and allow attackers to scale their operations across multiple communication channels.
2) Mapping the Services – Setting Up the Trap
With a target’s personal information and contact details in hand, cybercriminals usually map out the services the specific individual likely uses. This involves identifying the banks, online services, and applications that are part of the victim’s daily routine. They may gather this information from past data breaches or the target’s digital footprint.
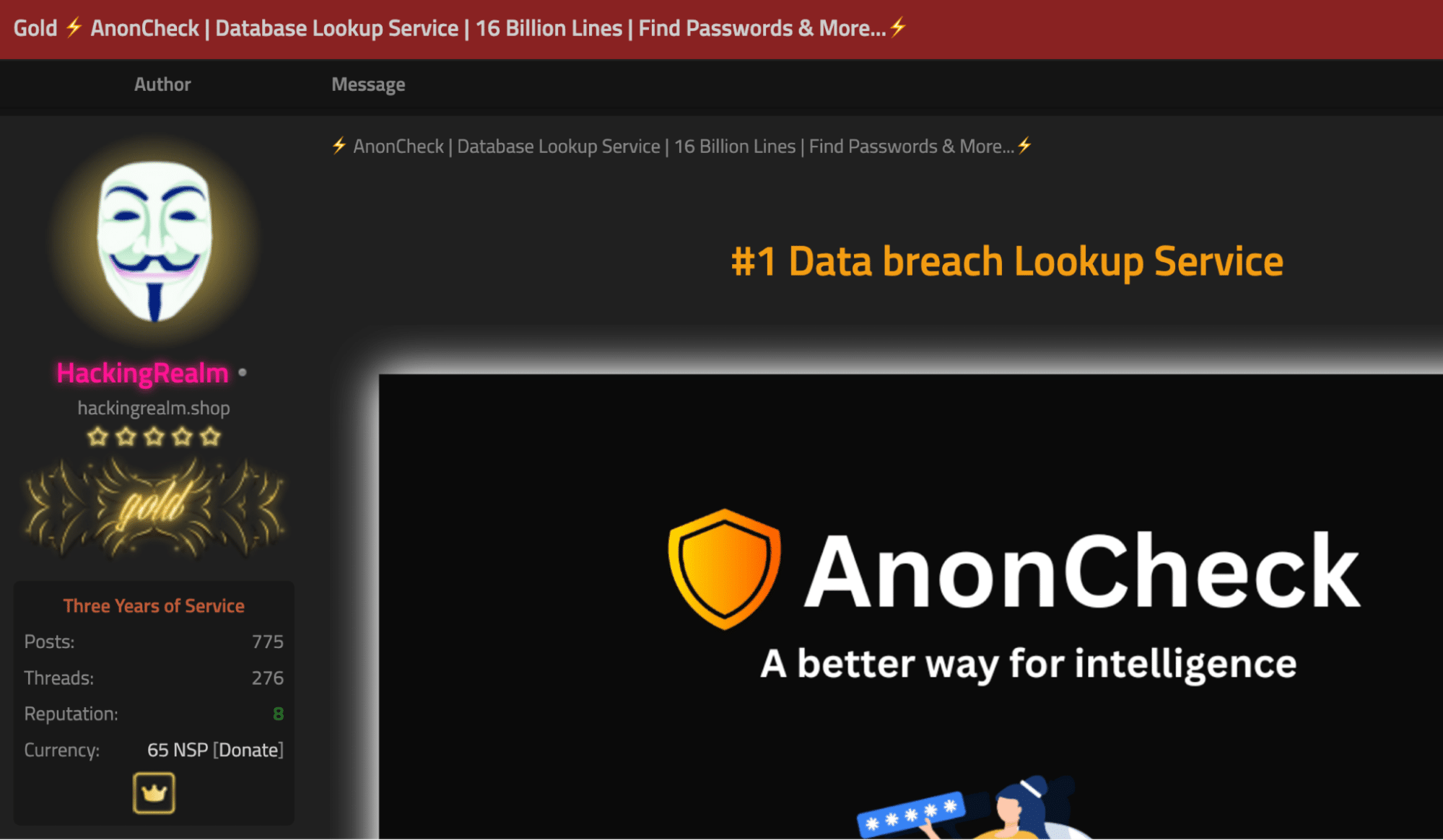
Knowing which services the victim uses is useful for the attackers. This knowledge helps them create convincing scripts for use in spear phishing emails, SMS (for smishing), or phone calls (for vishing). Attackers are able to use relevant, specific industry jargon during vishing calls, making their impersonation even more believable and increasing their chances of success. This is similar to the research that is done today when crafting phishing emails for a BEC attack.
3) Vishing Bots – Automating Social Engineering
In the context of vishing attacks, cybercriminals frequently rely on vishing bots to automate their operations. These bots use pre-configured scripts to impersonate trusted entities like banks, telecom providers, or customer support representatives. This level of impersonation adds credibility to the attack, increasing the chance of success. The impersonation can be so convincing that victims often divulge sensitive information like one-time-passwords (OTPs) and account passwords, facilitating account takeovers.
In general, the bots follow specific workflows based on the victims’ responses, making the attack more efficient.
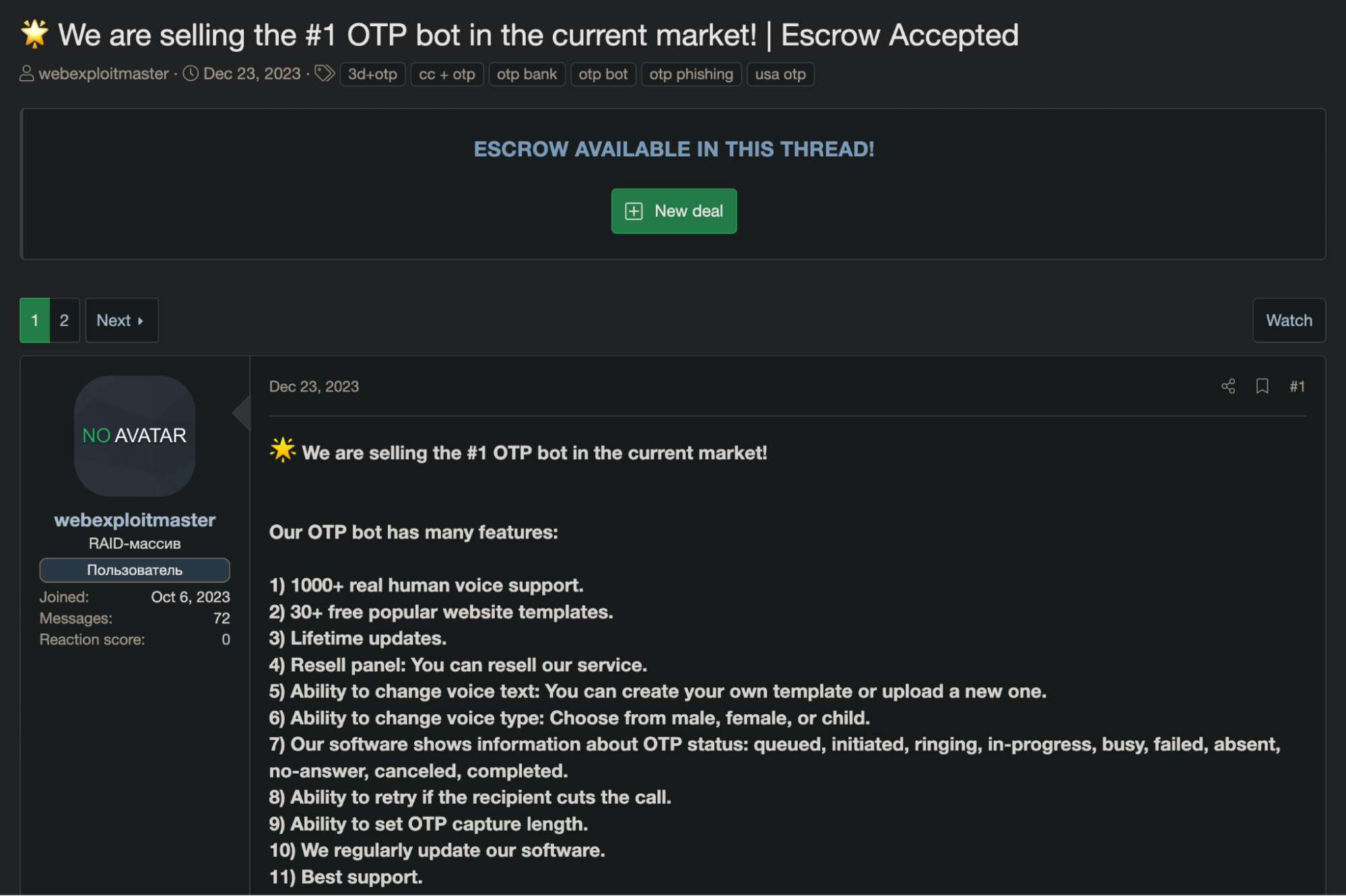
For example, some bots can pretend to be validating a recent transaction or providing technical support, all with the intention of duping the target into disclosing OTPs or other sensitive information (e.g. passwords).
4) Voice-Cloning Tools – Improving Credibility
Attackers increasingly use open-source technology, like voice-cloning tools from voice.ai, to increase the success of vishing attacks. The impersonation is extremely convincing because these tools can change the attacker’s voice to sound like a particular gender or match a particular accent.
Due to the realistic nature of this, victims are under additional psychological pressure because they think they are interacting with a real customer support agent. Gaining sensitive information, like OTPs or personal credentials, is much more likely with this credibility.
5) Capturing Credentials and Account Takeover
The final phase of the attack chain is credential capture, OTP capture, and account takeover. The victim will give their credentials, OTPs, or both if they are successfully tricked into believing they are communicating with a trustworthy organization.
Attackers can get past security measures, take over the victim’s accounts, and possibly carry out transactions, steal data, or even initiate additional attacks within the company once they have both the credentials and the OTP.

Attackers then use this access to achieve various malicious objectives, such as unauthorized fund transfers, identity theft, or exfiltration of sensitive data. In some cases, these compromised accounts are sold on cybercrime forums.
Protect Against Social Engineering Attacks
Our integrated security solutions protect against social engineering threats on all email, mobile, and browser platforms. Protect your organization from phishing, smishing, and vishing attacks in real time with our purpose-built platform and prevent cybercriminals from exploiting weaknesses in your security defenses. Begin protecting your digital surroundings immediately.
Learn more by browsing https://slashnext.com and scheduling a demo.


