Human hacking is a modern way to think about phishing in its entirety, which is anything malicious that reaches a user to steal credentials, data, or financial information. By focusing on phishing as an email problem or a spam problem is giving hackers the upper hand. Today, only protecting email and leaving other digital communication channels unprotected from phishing enables hackers to target your high-value users with increased success. The shift to remote work requires a shift in focus to multi-channel phishing protection. Hackers are capitalizing on digital channels that aid the productivity of remote workers like SMS/Text, Slack, LinkedIn, Zoom, Microsoft Teams, Google Meet, and WhatsApp. These channels are less protected and provide an easy way to trick users, steal credentials, and ultimately exfiltrate data from an organization.
These platforms have seen a spike in usage since the surge in remote work. SlashNext Threat Labs see new sites impersonating these common platforms and reports a 270% increase in social engineering and a 51% increase in phishing overall to date in 2021.
Over 95% of breaches start with credential-stealing, according to Gartner. With 71% of companies using cloud or hybrid cloud collaboration tools, it’s fertile ground for credential stealing. If users are reusing the same password on multiple work accounts like Zoom, Microsoft 365, and LinkedIn, it is easy to gain credentials to one and then use it to gain access to other platforms that share the same credentials.
Attacks Leveraging Zoom
In this example, a site impersonates Zoom asking users to enter their email address and password or sign in with other sources such as Google, Facebook, or corporate-issued single sign-on services.
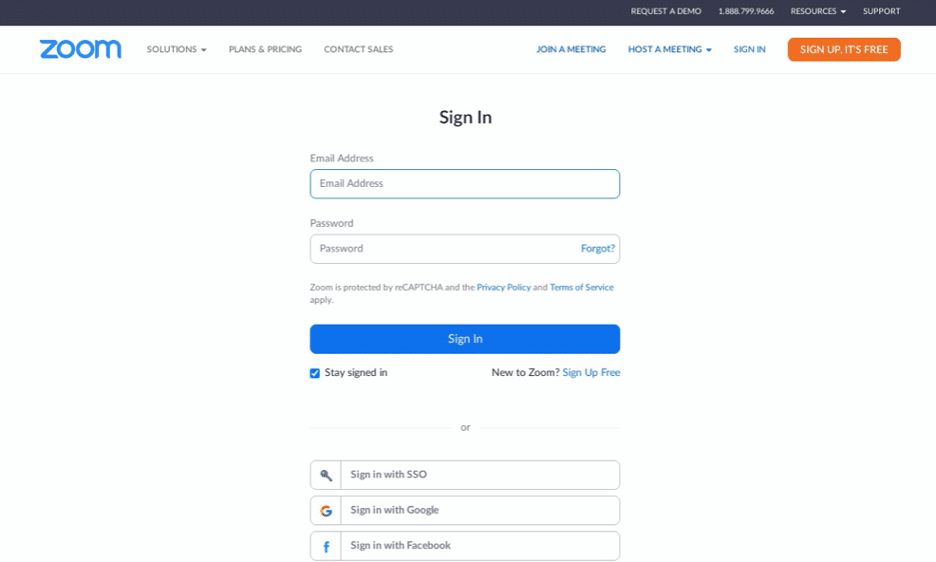
URL: (hxxp://zoomuserin(.)000webhostapp(.)com/)
SlashNext Threat Labs reports a growing trend of malicious URLs that appear identical to a meeting invite. This attack is used to harvest Microsoft 365 or Google Workspace credentials. In the example below, a malicious URL that looks very similar to a Zoom URL for a scheduled meeting takes the user to a landing page asking them to enter their Microsoft 365 credentials.
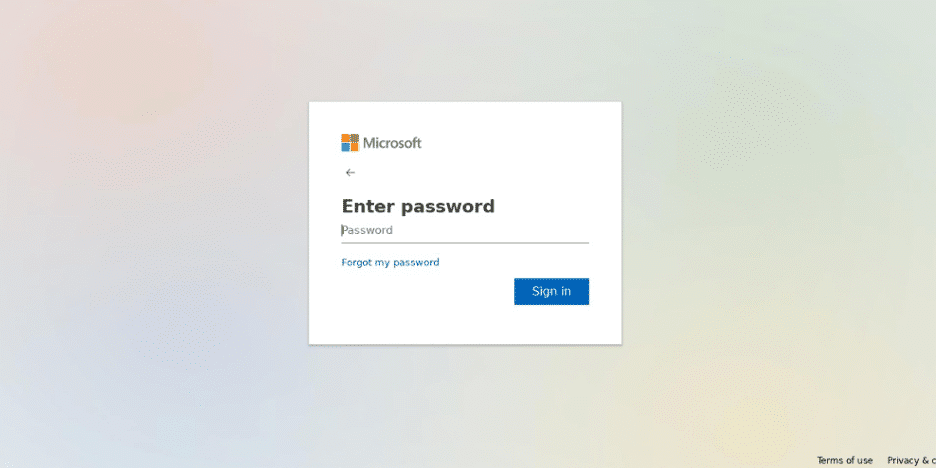
url: (hxxps://zoomorg6839(.)z13(.)web(.)core(.)windows(.)net/)
Attacks Leveraging LinkedIn
With the recent LinkedIn breach, one billion profiles were compromised. Attackers have used this information to automate targeted attacks to trick users into sharing more sensitive information, as seen in a recent spear-phishing attack with fake Linkedin log-in pages. This spear-phishing attack is most dangerous because it’s hosted on legitimate cloud infrastructure, in this case, Weebly, and will bypass most phishing detection tools.

As users adjust to remote working, the threat landscape evolves, and anti-phishing services need to protect users from phishing everywhere. The only way to know if you have a phishing problem outside of email is to assess the phishing attack surface. Here are a few questions to get started:
- Where are your employees protected from phishing?
- What phishing attacks are you missing on mobile, browsers, collaboration apps, gaming, or search?
- Are your users protected from zero-hour threats in real-time?
- Are they protected when accessing URLs on their browser or their mobile device?
- Do they have on-app or extension protection from zero-hour phishing threats?
Read the full Human Hacking Report at /the-human-hacking-report/


