SEER™ Threat Detection Technology
Patented behavioral phishing detection and machine learning to detect unknown threats with unmatched accuracy.
Detect More Evasive Threats
SlashNext’s patented SEER™ technology brings cloud-scale resources to real-time, multi-vector, multi-payload phishing threat detection. The SEER approach sees through more evasion tactics and detects previously unknown, zero-hour threats missed by URL inspection and domain reputation analysis methods.
SEER technology addresses:
- Phishing and social engineering payloads beyond fake login pages
- Shortened links
- Multiple URL redirects / forwards
- Other types of URL obfuscation
- Multi-stage attacks requiring user interaction, even captchas
- Use of compromised websites and legitimate hosting infrastructure
Stop The Email Attacks That Impact Your Business
Credential Stealing
The act of attaining passwords with the intent of accessing protected data.
Spear Phishing
Targeted attack to gain access to an individual’s account or impersonate a specific individual
SMiShing
Using text messages to trick users into divulging passwords or other PII for fraudulent use.
Social Engineering
Using deception to manipulate users into divulging confidential information for fraudulent use.
BEC, ATO and Supply Chain Attacks
Targets executives or financial teams to defraud a company for financial gain.
Trusted Services Compromise
Commonly used to launch phishing attacks or hack other trusted domains.
Rogueware and
HTML Attachments
Bank and Payment Fraud
Social engineering tactics to obtain money, assets or other property held by an organization.
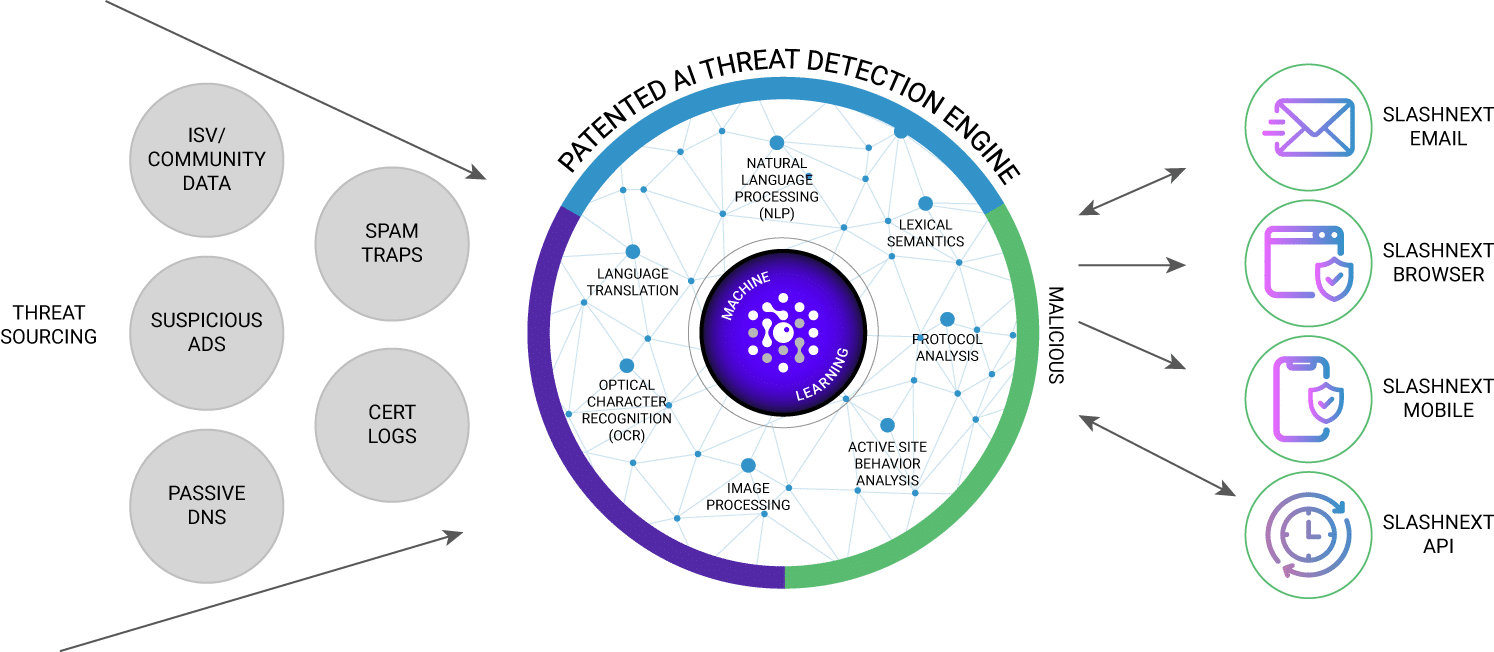
Global Cloud and In-Channel Detection with SEER™
SEER (Session Emulation and Environment Reconnaissance) uses a unique combination of techniques to see through evasion tactics and accurately detect phishing pages, even those on compromised websites and legitimate infrastructure. A broad intelligence gathering network and more powerful detection technology result in over 10K new detections daily, with thousands not available anywhere else.
The SlashNext Advantage is Your Advantage
Preemptive
Global, proactive threat hunting provides advance visibility, detection, and protection from emerging threats
Real-Time
Real-time, automated detection provides more effective protection from zero-hour threats
Extreme Accuracy
Near-zero false positives results in immediately actionable, block-ready threat intelligence
Overcomes Evasion Tactics
Detects threats missed by URL inspection and domain reputation analysis methods
Multi-Vector, Multi-Payload
Covers more types of phishing and social engineering payloads across all phishing attack vectors, not just email
Deployment Flexibility
Deploy to mobile, endpoints, and existing tools and infrastructure
Global, Multi-Vector Threat Sourcing
SlashNext SEER™ technology leverages a global, multi-vector threat intelligence network to proactively source suspicious URLs.
This network includes:
- Global hardware sensors inspecting billions of daily Internet transactions in real-time
- Spam traps
- Suspicious ad networks
- Passive DNS sensors
- Real-time certificate transparency logs

Deployment Flexibility
SlashNext SEER technology powers all SlashNext anti-phishing products, providing a new layer of real-time, multi-vector, multi-payload phishing protection across mobile devices, desktops, and network controls.
Integrations with leading TIP, SIEM, SOAR, DNS, NGFW, and MDM/EMM products enable rapid integration and deployment with existing tools and infrastructure. SlashNext technology can also be accessed on-demand for large-scale, automated phishing URL analysis, phishing IR, and threat hunting.
Extreme Accuracy
Patented SEER technology uses virtual browsers in a purpose-built cloud to perform dynamic, run-time analysis of suspicious web pages. Together with mature machine learning algorithms, SEER delivers binary verdicts—not threat scores—with 99.07% precision.
This uniquely effective approach uses:
- Virtual browsers to dynamically load webpage contents and analyze site behavior
- Natural Language Processing (NLP) and computer vision techniques to understand the textual and visual context of a rendered webpage
- Dynamic site behavioral analysis (fill out forms, analyze behavior, follow re-directs, etc.)
- Mature machine learning algorithms deliver accurate, binary verdicts rather than threat scores
Our Latest SlashNext Blog Posts

Five Ways Spear Phishing Tactics are Evolving in 2025
What type of phishing became very effective around 2010 and still worries security teams today? Spear phishing. Spear phishing remains highly effective and is getting

Blov HTML Crypter: Phishing Evasion Through Encryption and Obfuscation
Cybercriminals are sharpening their phishing tactics with tools like Blov HTML Crypter — a utility that modifies HTML files to evade detection by security scanners.

Government Agency Spoofing: DocuSign Attacks Exploit Government-Vendor Trust
The latest wave of DocuSign attacks has taken a concerning turn, specifically targeting businesses that regularly interact with state, municipal, and licensing authorities. Since November
Experience SlashNext Protection in Action
Request a free trial to see how SlashNext detects zero-hour threats in real-time and stop the attacks that impact your business.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.


