Social Engineering Scams
The Oxford dictionary defines Social Engineering as the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes.
The scheme could targets victims by using any combination of phishing techniques in a complex fraud and it could even involve an impersonator showing up in person with the goal of gaining physical access to a system or building. The purpose of Social Engineering is to psychologically manipulate targets into disclosing sensitive information or taking inappropriate actions. Many times, victims have no idea they did something wrong until the fraud is exposed.

Cybercriminals’ motives are the same with social engineering scams as with tech support scams. The goal is to motivate a user to complete a form or install something to access information or money. One example is an iPhone giveaway, which starts asking a series of questions on the first page. When the user is 20% done, there is a new questionnaire and then another questionnaire, until they have collected all the user’s confidential information and now the user is just 10% away from getting an iPhone. There’s nothing inherently wrong with these ads because they are legitimate rewards. There is no way to distinguish between legitimate and malicious ads because they are intermingled within the very fabric of internet advertising. One out of 10 ads are malicious, but they are precisely the same as legitimate ones, there are no files or malware to detect.
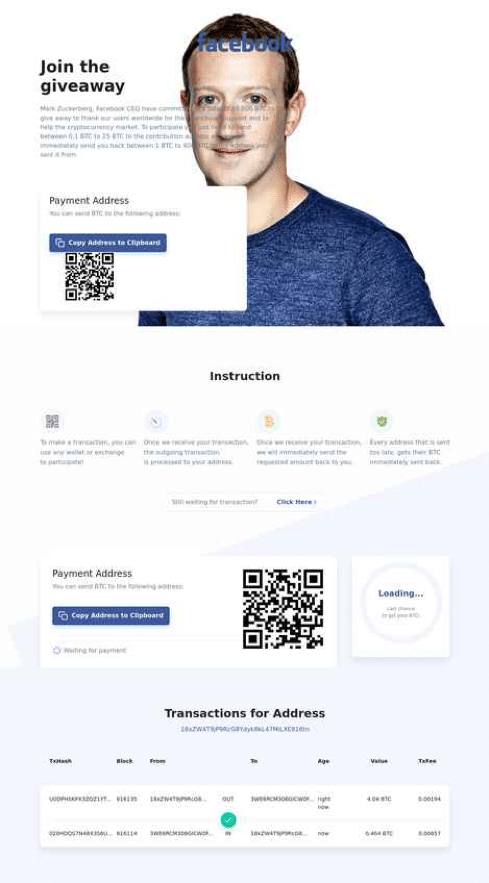
One of the most famous social engineering scams was the Twitter breach involving Bitcoin transfer scams. As part Twitter breach accounts of various celebrities were compromised to perform Bitcoin scams. The celebrity accounts promises to give away bitcoins, but only if the victim initiate a smaller transfer first. Since these celebrities have hundreds of thousands of followers and the request was on trusted service like Twitter on the celebrities real accounts, it was easy to social engineer a large group of people in a short period of time and an easy way for cybercriminals to make money. You can read more about it here.
Bitcoin transfer scams are not a new concept. SlashNext’s Threat Lab sees dozens of Bitcoin phishing sites each day that use celebrity photos and names to conduct similar cryptocurrency scams. Cybercriminals prefer stealing cryptocurrency because it can be used for nefarious purposes on the Darkweb, leaving no trail behind.
Example: Screen shots of iBitcoin frauds that are part of social engineering scams.
SlashNext Blog | Social Engineering Scams

Today, while man-in-the-middle (MiTM) attacks are still a big concern, the security endpoint has changed to the browser, creating a MiTB phishing threat that poses real danger.

In recent years phishing has become the number one threat action over malware. Recent workforce changes spurred by the pandemic has led to an exponential increase in phishing attacks.

Just how prevalent are these phishing callbacks and C2 infections? In every client install we perform – 100 percent! – we see C2 infections and callbacks. Are you compromised?
In 2020 phishing exploded as the world faced a 100-year pandemic and many people moved to remote working and learning, which changed the phishing threat landscape forever.
It’s Time to Get Started with SlashNext
Learn how to leverage the industry’s best zero-hour phishing protection and IR solutions in your environment.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.



