SMishing
Smishing is a malicious text from a messaging service which is a mash-up of SMS and phishing (Smishing). A smishing threat is a form of phishing that utilizes your mobile device as an attack vector. Often the initiation is in the form of a text message disguised as a communication from a bank or other potentially trusted brand than encourages a click-through to a phishing site where credentials are targeted.
As mobile devices become more prevalent for work communication, smishing threats will likely increase, as will their sophistication. These attacks are initiated in the form of a text message disguised as a communication from a trusted brand such as banks, retail, payment services, or even a trusted person. Frequently uses a disguised link, people tend to respond to text messages much quicker and with less thought than email, and their screens can hide important clues about the web pages they visit, making SMiShing a very effective, and thus dangerous, attack vector.
People also trust a message from their messaging app on their phone then email, because it’s hard to imagine a hacker has their phone number. According to Gartner, 98% of people read text messages and 45% are of people responded, as opposed to only 6% of people respond to emails.
Further complicating matters is that phishing protections on iOS and Android devices is almost non-existent, putting users and organization at increased risk of SMiShing attacks. With SlashNext, however, malicious SMS/text messages are accurately identified and quarantined, protecting users from taking the bait. Our native iOS and Android apps provide heavyweight mobile protection yet feature lightweight memory consumption and negligible battery usage.
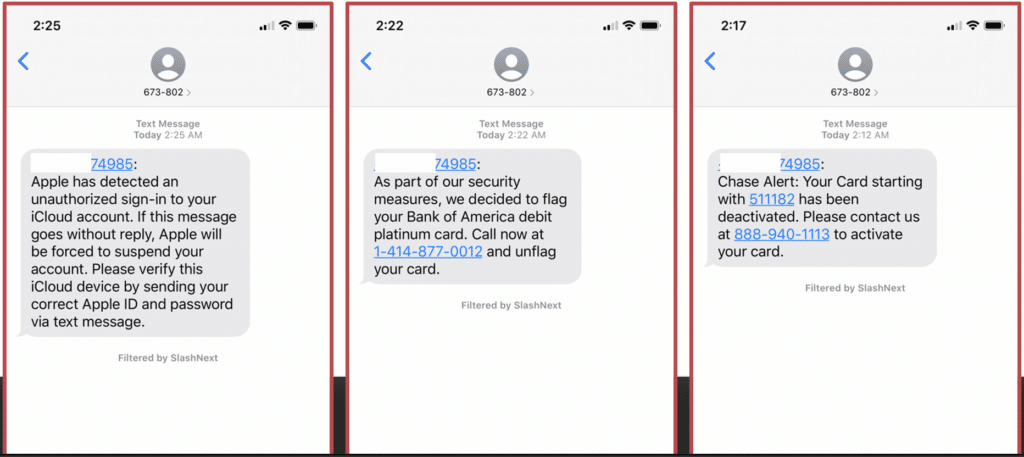
Example: Screenshots of SMishing attacks.
SlashNext Blog | SMishing

Today, while man-in-the-middle (MiTM) attacks are still a big concern, the security endpoint has changed to the browser, creating a MiTB phishing threat that poses real danger.

In recent years phishing has become the number one threat action over malware. Recent workforce changes spurred by the pandemic has led to an exponential increase in phishing attacks.

Just how prevalent are these phishing callbacks and C2 infections? In every client install we perform – 100 percent! – we see C2 infections and callbacks. Are you compromised?
In 2020 phishing exploded as the world faced a 100-year pandemic and many people moved to remote working and learning, which changed the phishing threat landscape forever.
Experience SlashNext Protection in Action
Request a free trial to see how SlashNext detects zero-hour threats in real-time and stop the attacks that impact your business.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.



