Rogue and Malicious Software, Apps, and Extensions
There is a lot at stake with all types of phishing, but malicious browser extensions can be particularly sophisticated. Google runs security checks on Chrome extensions before they are available in the store, but cybercriminals know this, and by design, these browser extensions have legitimate functionalities. They are capable of updating or downloading JavaScript on the fly and once installed; the malicious script is downloaded from the web. Using a runtime code, once the browser is closed, it goes away, but when you launch the browser, it’s active, because the code is living inside the browser memory with JavaScript. JavaScript is the most common thing you can find inside a browser, so there’s no way you can distinguish the malicious JavaScript that is scraping data from JavaScript that’s being rendered by a legitimate page.
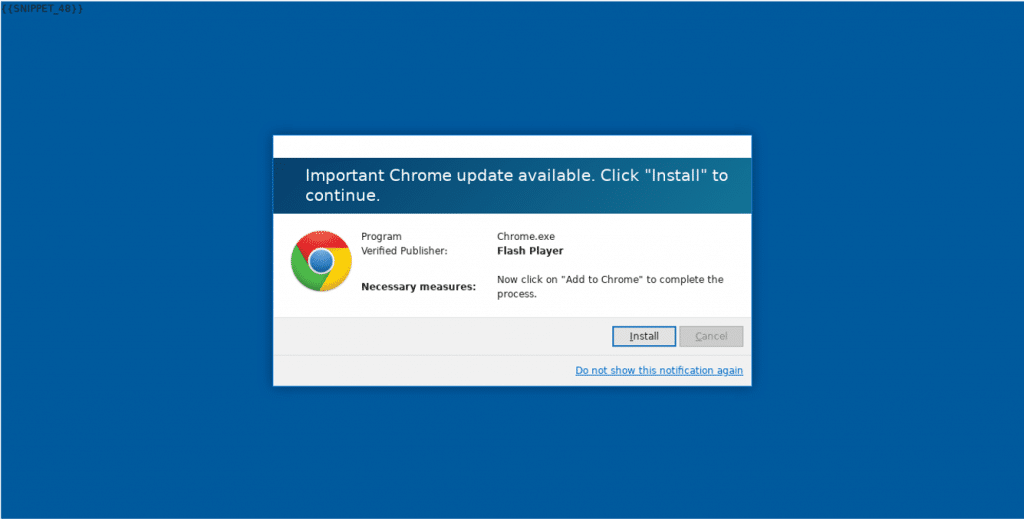

Now we see more phishing attempts that can bypass two-factor authentication (2FA) or multi-factor authentication, with Man-in-the- Browser attacks. Many with 2FA believe they’re protected from phishing because the birth of 2FA grew from the knowledge that anti-phishing defense systems were no longer working. Users think it’s ok to use extensions that make their life easier, like logging into email faster or using a PDF Converter. These extensions have legitimate functionality, but they have a side business, and that’s the reason why they are free. Their exact functionality is the Man-in-the-Middle that is scraping and selling their data.
At SlashNext, we see malicious browser extensions that merely wait for the 2FA to complete. A browser extension offers bad actors the perfect workaround for organizations that rely heavily on 2FA. By design, once a browser extension is installed, it has access to the complete canvas of the browser. Once logged in, they hijack the session and capture whatever is being rendered on the computer screen. These extensions have the full power to do whatever the user is doing and seeing whatever is within that browser window. For example, a user logs into a Service Now Management Portal, once 2FA is complete, the browser extension starts collecting data—leaving the organization’s cloud infrastructure wholly open and vulnerable. With cybercriminals waiting for the user to log in legitimately before they start exfiltrating data from the browser, 2FA or multi-factor authentication ceases to be a viable security option to protect organizations.
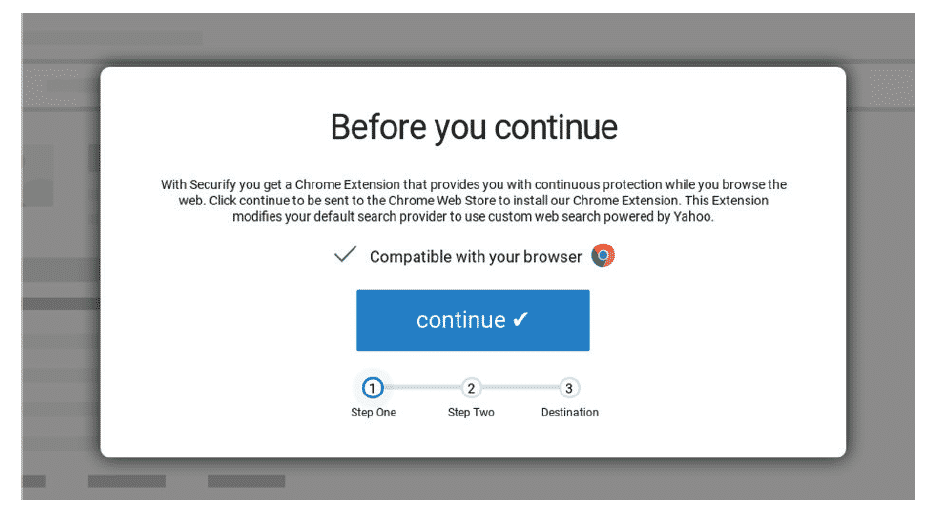
Example: Screen shots of malicious browser extension.
SlashNext Blog | Rogue Apps and Extensions

Today, while man-in-the-middle (MiTM) attacks are still a big concern, the security endpoint has changed to the browser, creating a MiTB phishing threat that poses real danger.

In recent years phishing has become the number one threat action over malware. Recent workforce changes spurred by the pandemic has led to an exponential increase in phishing attacks.

Just how prevalent are these phishing callbacks and C2 infections? In every client install we perform – 100 percent! – we see C2 infections and callbacks. Are you compromised?
In 2020 phishing exploded as the world faced a 100-year pandemic and many people moved to remote working and learning, which changed the phishing threat landscape forever.
Experience SlashNext Protection in Action
Request a free trial to see how SlashNext detects zero-hour threats in real-time and stop the attacks that impact your business.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.



