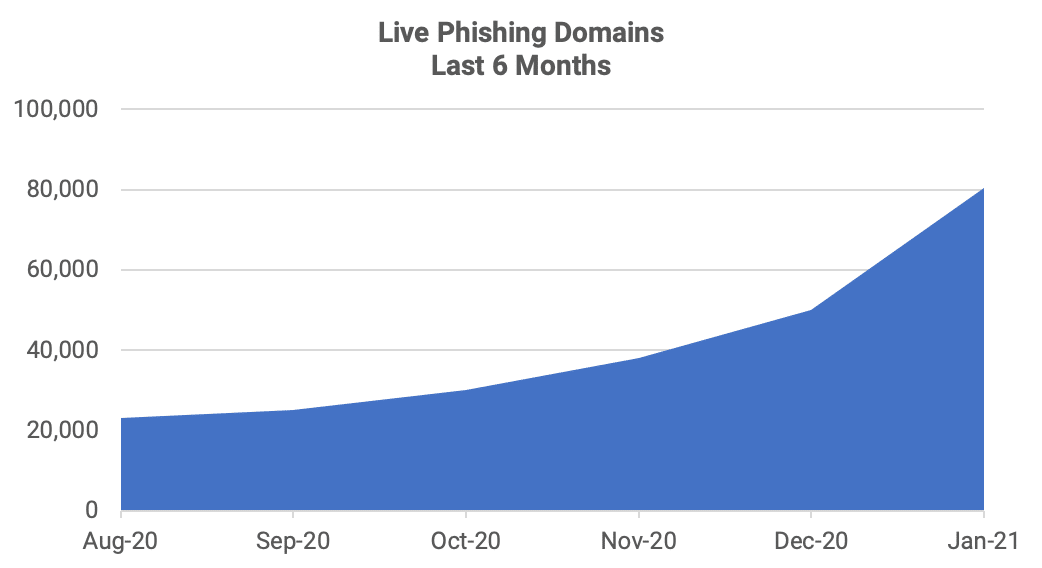
In 2020 phishing exploded as the world faced a 100-year pandemic and many people moved to remote working and learning, which changed the phishing threat landscape forever. Our recent report, The State of Phishing, SlashNext Threat Labs, reports on the latest statistics and trends in phishing. In the last 12 months, cybercriminals launched thousands of new phishing pages every hour to harvest personal information, steal corporate data, and commit credit card fraud with no sign of slowing down. Phishing increased 42% in 2020, over 2019. By mid-2020, SlashNext Threat Labs saw the number of daily phishing threats top 25,000 a day, a 30% increase over 2019 figures. By fall, the number had grown to 35,000/day and grew to 50,000/day by December and continues to rise in 2021.
The change in the phishing threat landscape is attributed to the increased use by cybercriminals of automation and AI. The low cost of computing and the availability of behavioral information from the public and the dark web make targeting effective by simulating trusted sources and launching attacks through new communication channels. These sophisticated tools offer cost-efficient and easy ways to run short-lived but highly effective phishing campaigns. By leveraging legitimate infrastructure, cyber criminals increase the likelihood of compromising a target and increase their success.
One example of the latest spear-phishing attacks on legitimate infrastructure found by SlashNext Threat Labs in late January 2021 was a 2FA attack. The spoofed Chase Bank 2FA authentication page was hosted on legitimate infrastructure on Doster.com, a web hosting offering for small businesses with additional business services.
We are now seeing more phishing attempts that can bypass two-factor authentication (2FA) or multi-factor authentication. Many with Two Factor Authentication (2FA) believe they’re protected because the birth of 2FA grew from knowing that current security defense solutions were no longer working. Rogue browser extensions can deliver these types of attacks by using Man-in-the-Middle tactics. These browser extensions offer cybercriminals the perfect workaround for organizations that rely heavily on 2FA. By design, once a browser extension is installed, it can access the browser’s complete canvas. Once logged in, the session is hijacked to capture whatever is on the computer screen. These extensions have the full power to do whatever the user is doing and seeing whatever is happening within that browser window.
To learn more about the State of Phishing in 2021, get the full report, and learn more about SlashNext’s comprehensive phishing protection service, request a demo.


