Hackers no longer rely solely on email when trying to infiltrate your organization. Social media, including LinkedIn, have become the new preferred method of attack for these criminals.
This year, Google’s Threat Analysis Group (TAG) discovered a largescale cyberattack that originated out of North Korea. The cyberattack utilized fake blogs, fake email accounts, and even multiple different fake profiles on social media platforms like LinkedIn. The hackers create elaborate fake profiles to trick their victims. Once they identify a target, they will begin to add the potential victim’s friends and colleagues. Then they “like” and comment on the content that the victim’s friends share to create the illusion of being a real person. Once they have built up a log of activity and connections, they will then send a connection request to the target. The activity logs and mutual connections create a false sense of security for the victim, which makes them more likely to participate in the phishing attack.
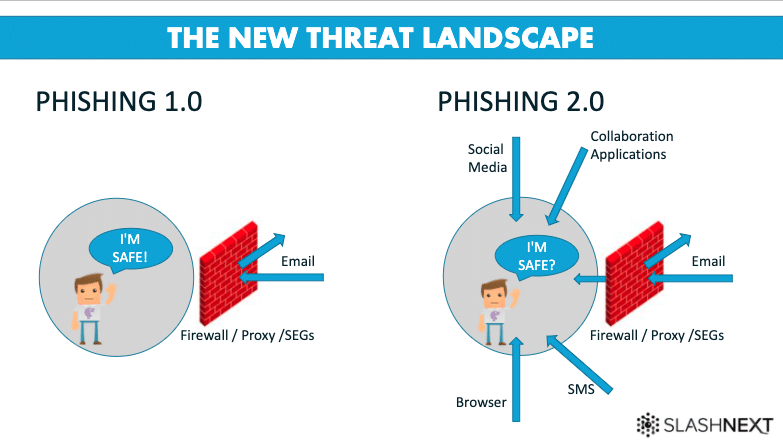
The New Phishing Threat Landscape
The phishing paradigm has shifted, and this new level of sophistication, speed, and attention to detail are what we call Phishing 2.0. Users are now being exploiting through mobile, email, and web. These hackers are going after the human attack surface with new kinds of phishing, and social engineering schemes to deliver a greater variety of phishing payloads. These phishing attacks use multiple tactics and speed to evade traditional defenses that rely on domain reputation and blacklists. While credential-stealing remains popular, there are new multi-vector phishing attacks that leverage web, SMS, social, search, and collaboration tools. Phishing is now just as prominent in SMS, social media, ads, search engines, browser extensions, and chat apps. The payloads include rogue browsers, scareware, fake virus alerts, banking fraud, and more. HTML phishing can be delivered straight into browsers and apps, bypassing infrastructure (SEG, NGAV, AEP) and evading URL inspection & domain reputation analysis methods. In doing so, they can bypass traditional defenses with more than an 80% success rate.
These new types of attacks that come from an employee’s personal line of communication, such as SMS or LinkedIn, cannot be stopped unless you interact with the threat at the point of click on a device. These attacks cannot be stopped through an email API nor in a web proxy/SASE solution. This is because a user’s personal traffic typically does not flow through those solutions in a remote working scenario.
SlashNext Stops Phishing
Only SlashNext can stop Human Hacking across all your digital communication channels. That includes these new types of phishing attacks on a mobile device or the user’s web browser. Our Phishing Protection is powered by our SEER (Session Emulation and Environment Reconnaissance)™ threat detection technology and real-time phishing threat intelligence. Our AI phishing defense cloud, which performs dynamic, run-time analysis on billions of URLs daily through virtual browsers, machine learning, and NLP (Natural Language Processing), provides users and IT Security teams with a new level of protection from phishing and social engineering attacks. Whether it’s fake login pages aiming to steal user credentials or other social engineering attacks designed to deceive users, we can block these sites and protect users from being phished on any browser, any device, and any OS. /technology/


