Our team has been investigating the latest services and infrastructure available to cybercriminals for orchestrating SMS phishing campaigns. After analysing cybercrime forums, it is clear that SMS gateways are currently a highly popular method, thanks in no small part to the minimal cost. With these SMS gateways, cybercriminals can send hundreds of thousands of SMS phishing messages for as little as €0.004 each. In our recent State of Phishing Report, we found a 1,265% increase in malicious phishing messages across all mediums, and 39% of mobile-based attacks were SMS phishing. No doubt, the widespread availability of these services is contributing to that increase.
SMS Message Gateways
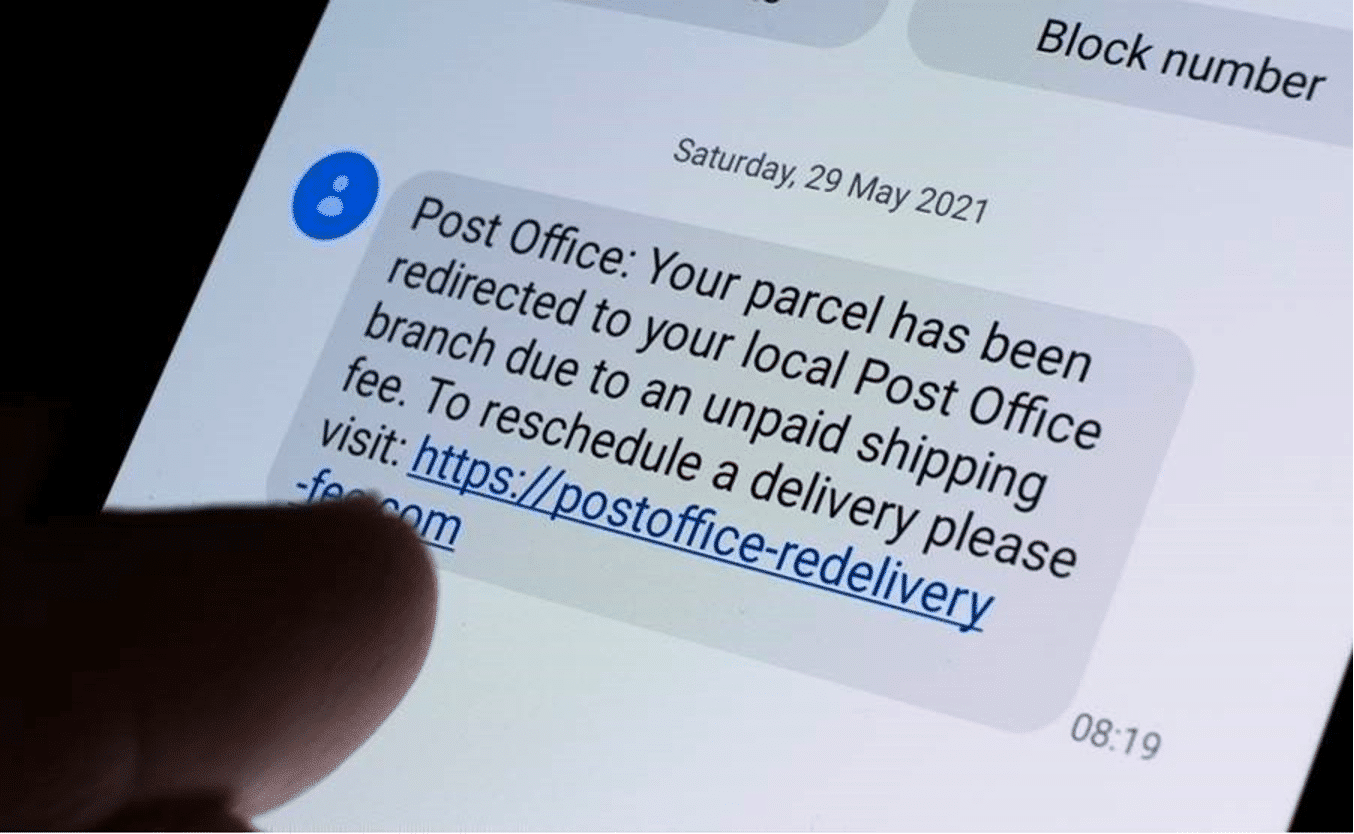
Today’s smartphone users are vulnerable to SMS phishing attacks. An examination of cybercrime forums reveals that cybercriminals have easy access to SMS gateways capable of sending large volumes of text messages. This enables mass SMS spamming, which allows phishing attacks and scams to reach people’s phones quickly and repeatedly.
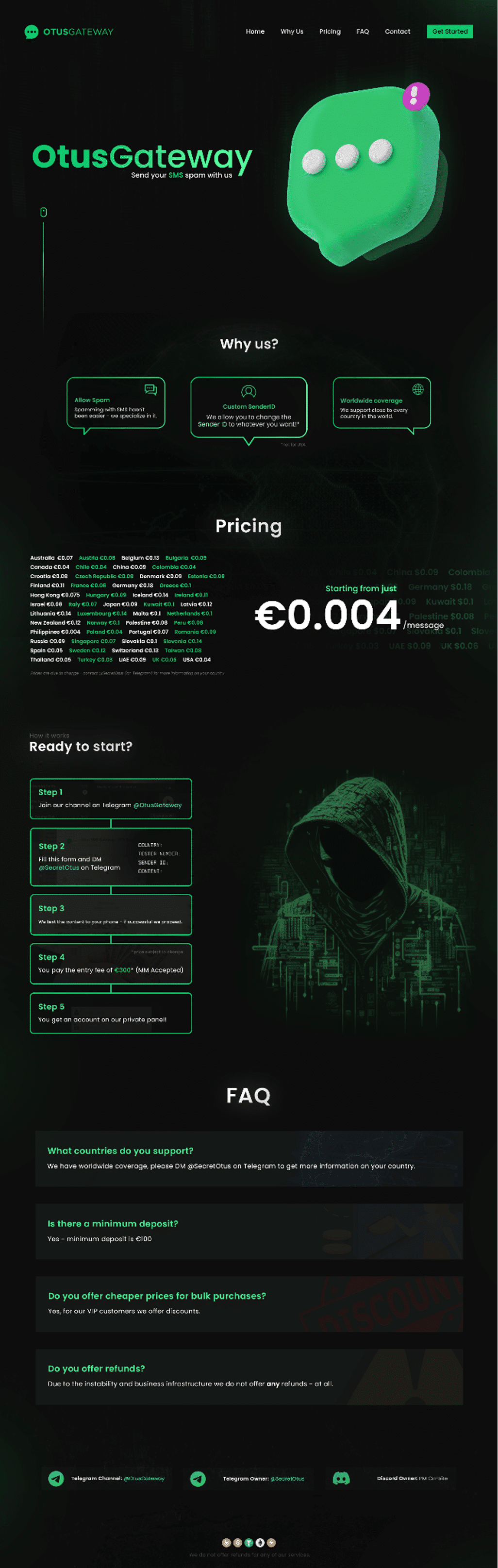
Image: A prominent SMS phishing gateway that’s being advertised on networks
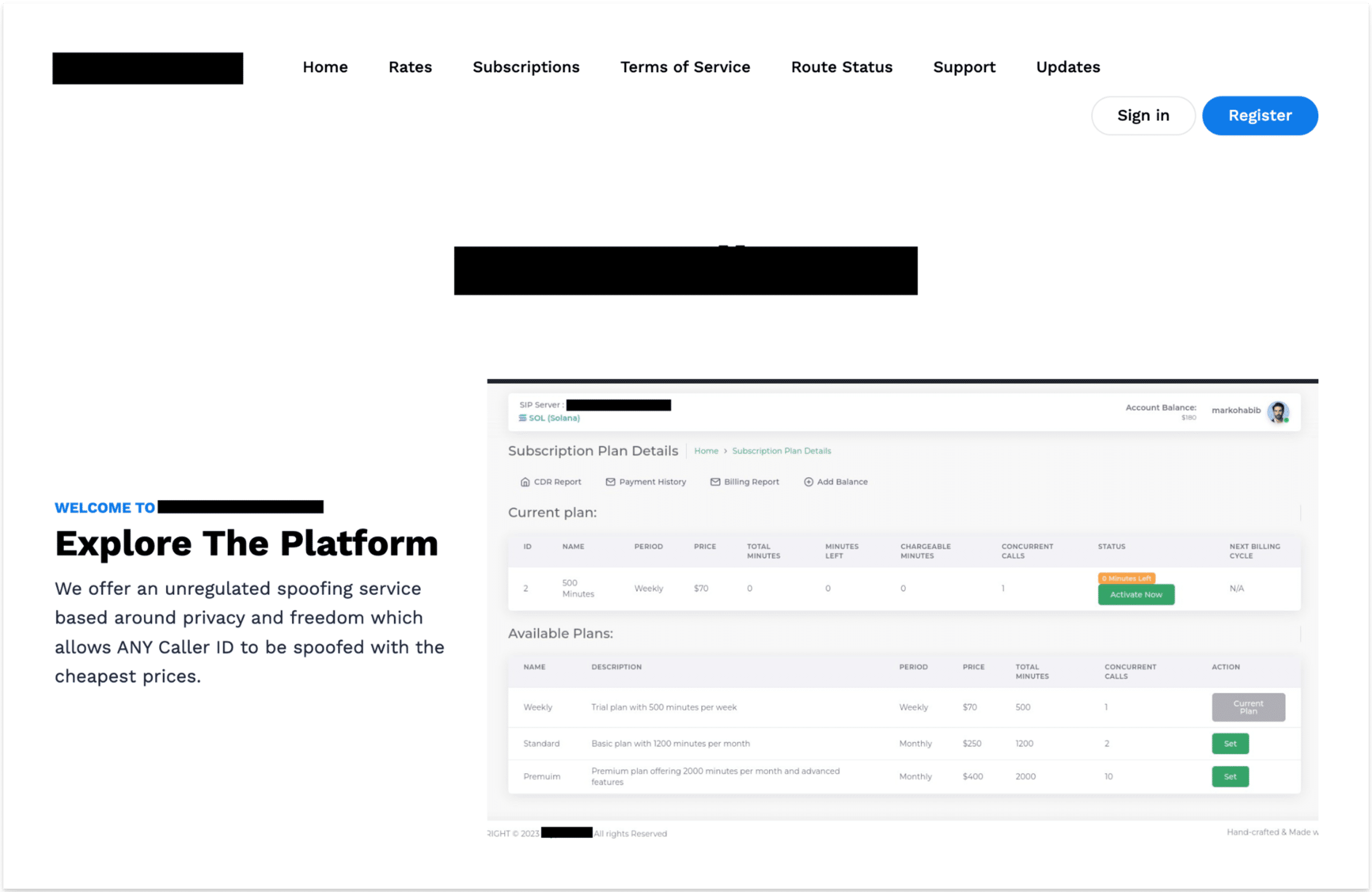
These gateways allow anyone to sign up for a small fee and send an unlimited number of SMS phishing messages to any phone number they want. In effect, these gateways provide an HTTP interface that is linked to a session initiation protocol (SIP) trunk, which is a virtual phone connection that allows a business to make multiple voice calls over a single internet connection.
Image: An example of one of the SMS messaging gateways
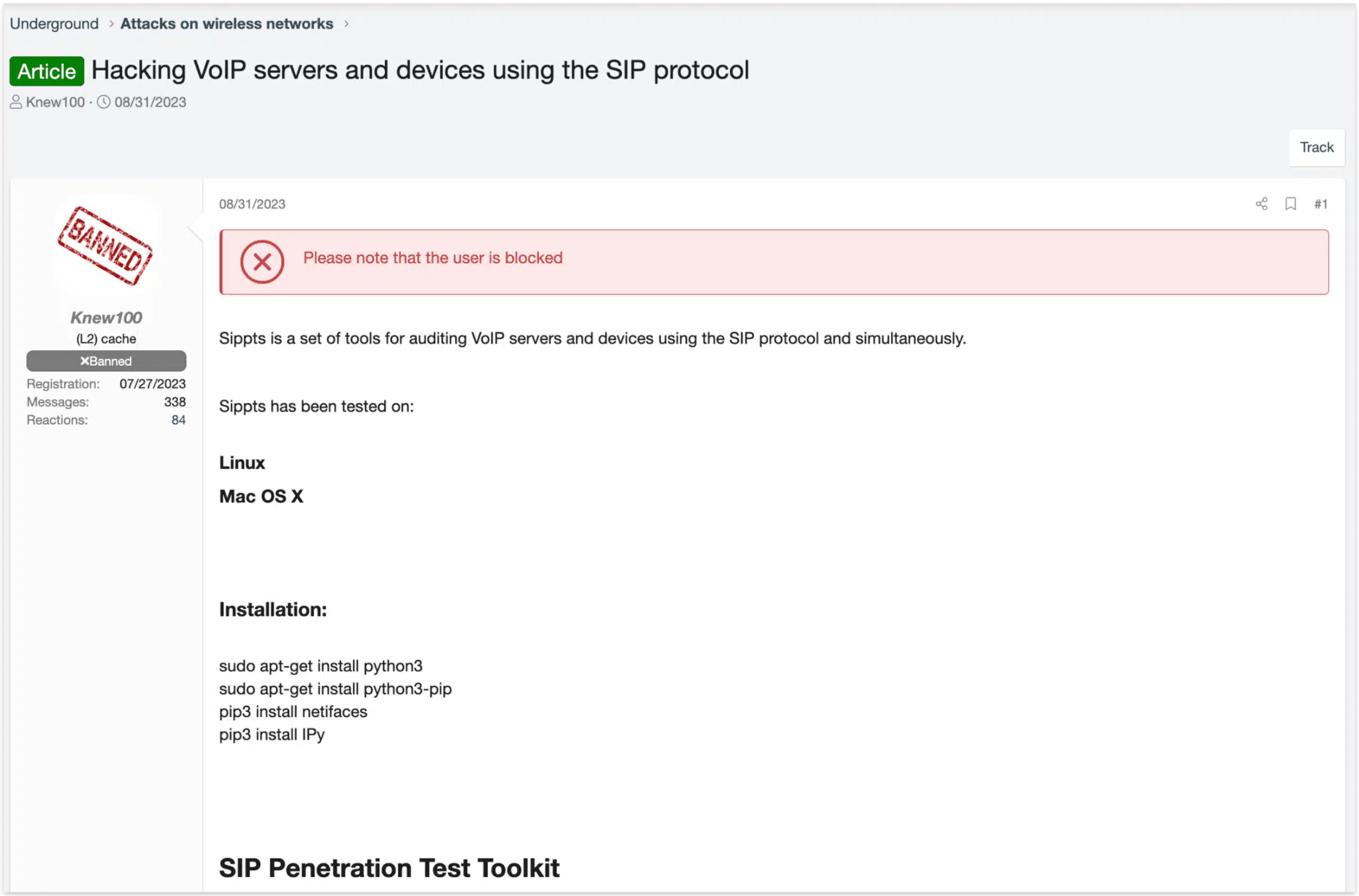
To remain anonymous, the individuals operating these services simply purchase access to SIP trunks from providers who accept cryptocurrency. Alternatively, they compromise them. According to our research, millions of SIP-enabled devices are directly connected to the internet and accept incoming traffic from all IP addresses. In fact, there are threads on cybercrime forums and networks that share information about auditing SIP itself. It would not be unreasonable to assume that many SIP trunks have been compromised.
Image: A user on a cybercrime forum sharing a guide on how to audit the SIP protocol
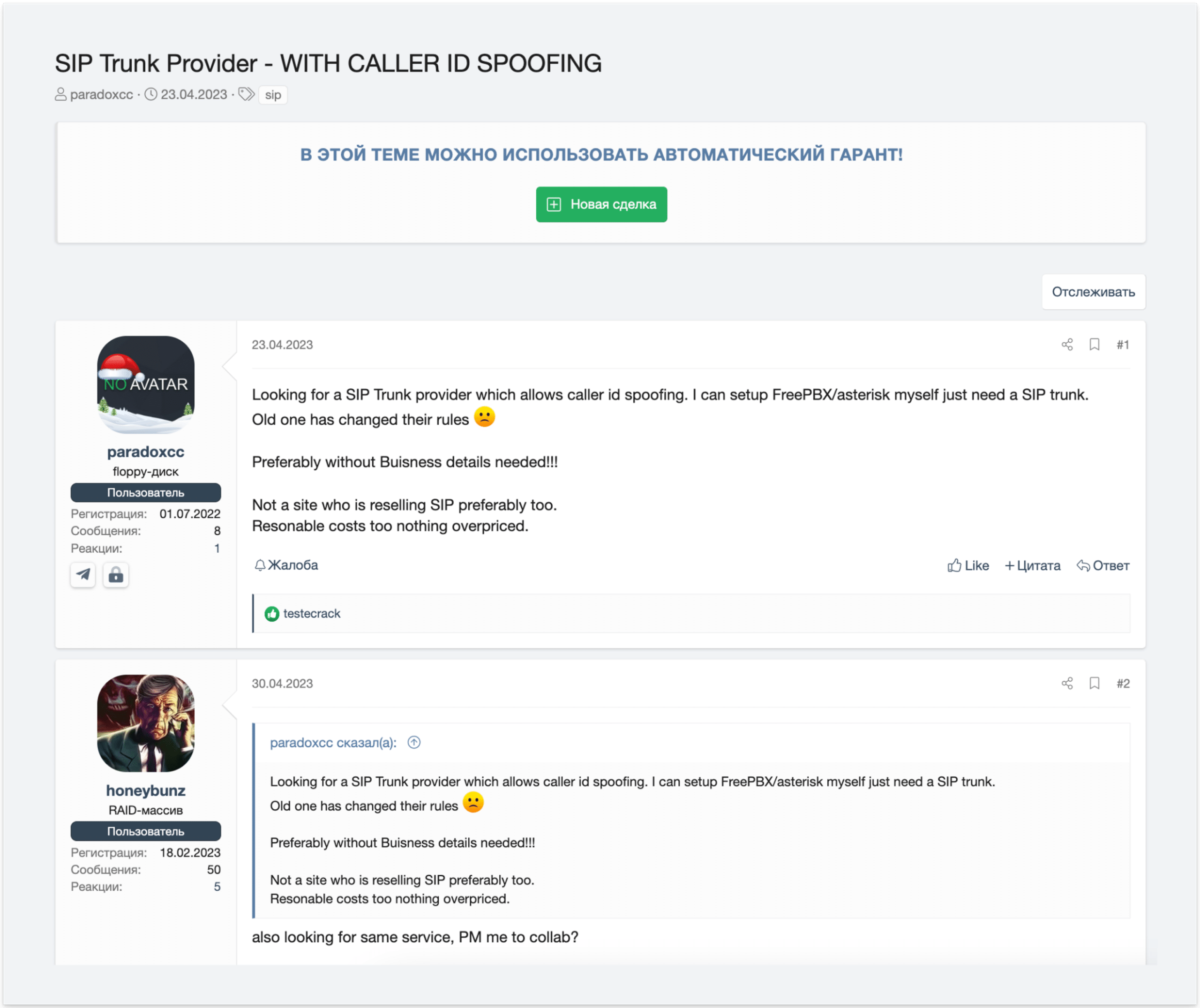
During our research, we also discovered that many users are attempting to purchase direct access to SIP trunks from other cybercriminals rather than going through one of these accessible gateways.
Image: A user on a cybercrime forum looking for direct access to a SIP trunk with caller ID spoofing
This is most likely because many gateway providers require a minimum deposit that is higher than what criminals would have to pay if they ran their campaigns directly on their own infrastructure.
One-Time Password Bots
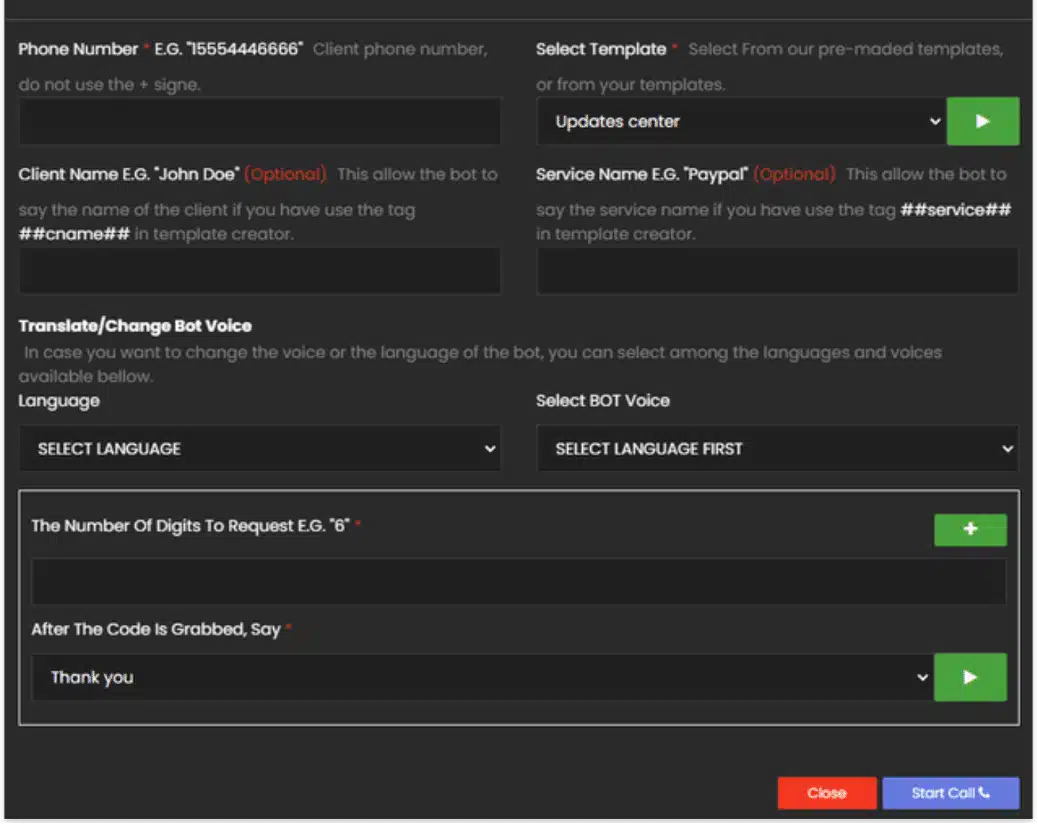
Another intriguing feature we’ve noticed with these gateways is integrated one-time password (OTP) bots. To provide two-factor authentication, many online services use one-time passwords sent via SMS text messages.
To circumvent this security measure, cybercriminals use automated OTP software bots that intercept SMS messages and extract one-time codes. Typically, OTP bots are sold as standalone software.
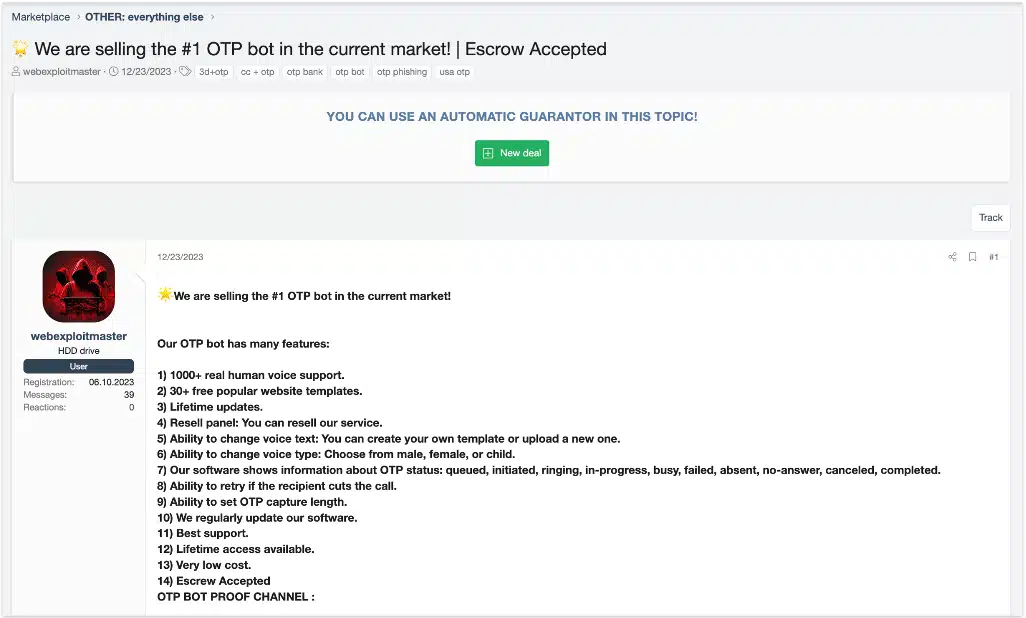
However, some SMS gateways directly integrate them, making it easier for criminals to bypass two-factor authentication when conducting phishing campaigns and account takeover attacks.
Image: A user on a cybercrime forum offering a OTP bot for sale
By creating an account on one of these gateways, attackers gain access to a diverse set of tools for SMS and voice-based attacks. Here’s an example of what the attacker would see when launching an OTP session attack:
Image: An example of a OTP attack interface
After the victim enters the one-time password, the code is sent to the cybercriminal who started the attack via the same panel:
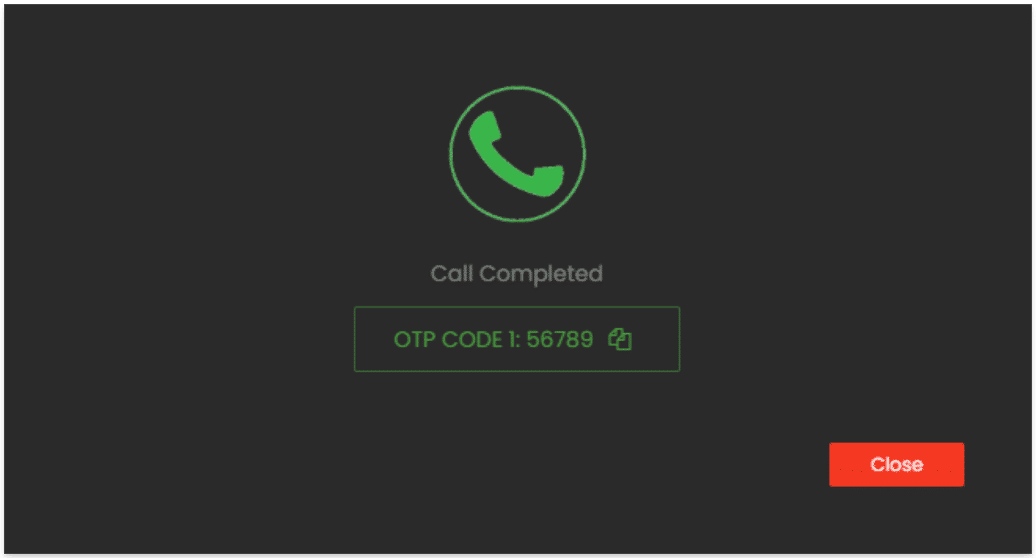
Image: An example OTP code that was stolen
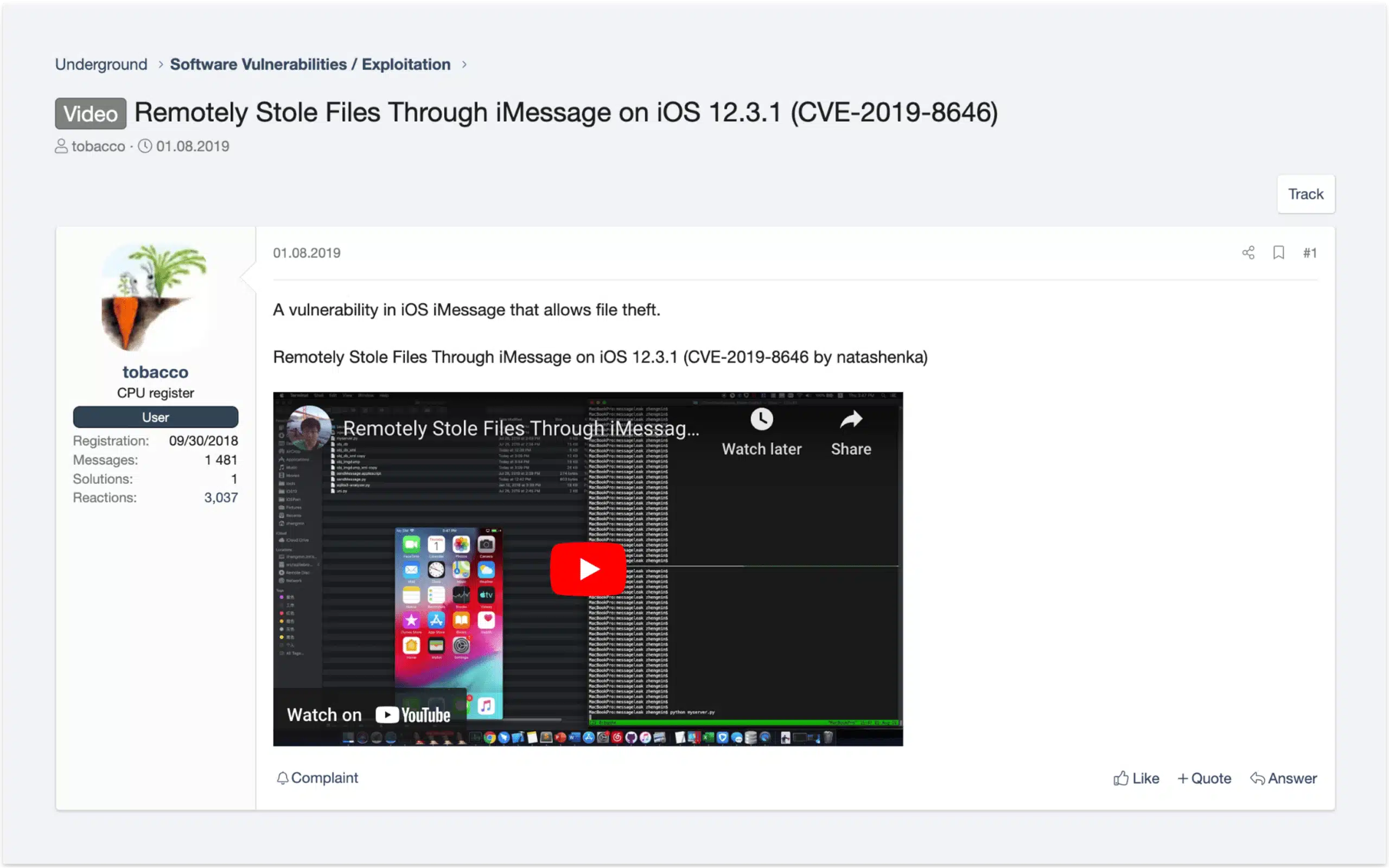
Zero Days And iMessage
Although there are ongoing discussions about exploiting iOS and iMessage, many of these conversations appear to be centred on sharing proof-of-concepts for vulnerabilities that target outdated versions of this software. The use of low-cost gateways appears to be the most popular method for orchestrating an SMS phishing campaign today.
Image: A user on a cybercrime forum sharing a POC for CVE-2019-8646
Cybercriminals simply require a large amount of data containing telephone numbers, which is trivial to obtain, whether they hack it themselves or buy it from someone on one of these networks, and then create an account on one of the multiple gateways available.
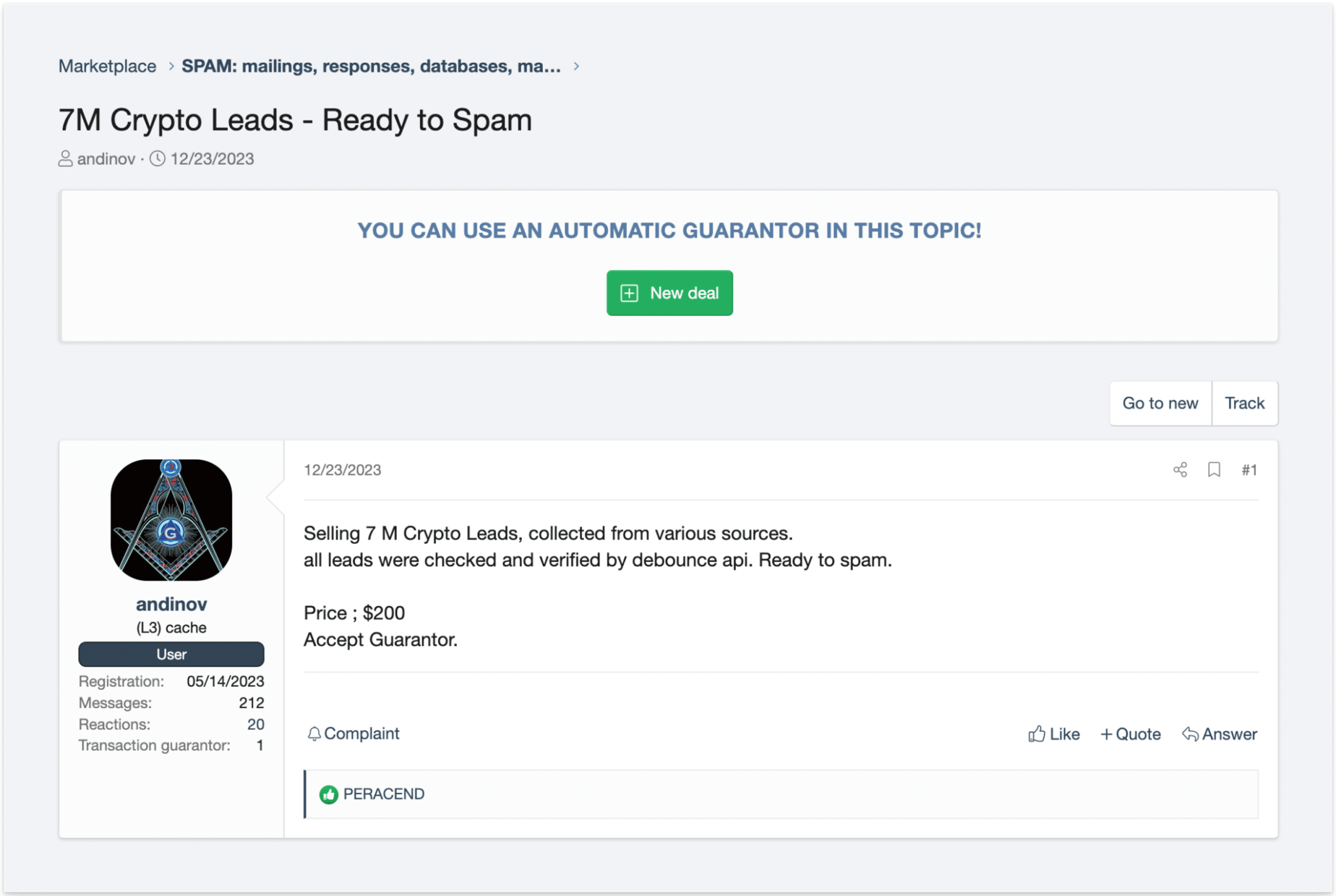
They can then effectively plan large-scale SMS phishing campaigns. This method, as described above, is far more common than the widespread exploitation of zero-day vulnerabilities in relevant software, because of its lower entry barrier and efficacy.
Protection With SlashNext Mobile Security
To prevent SMS phishing attacks, we offer a mobile security solution. Our platform is designed to safeguard against a variety of mobile phishing threats, including SMS-based scams. We provide real-time threat detection, ensuring a secure mobile experience.
Features include safe preview, detailed threat information, support ticket submission, and automated notifications, all while maintaining minimal resource usage. This protection is ideal for business and personal use, ensuring your mobile devices are secure against sophisticated phishing attacks. For more details, please visit our mobile security page.