
Security researchers here at SlashNext recently uncovered a promotional image on a cybercrime network showcasing a service called “SessionShark O365 2FA/MFA.” SessionShark is a phishing-as-a-service toolkit built to bypass Microsoft Office 365 multi-factor authentication (MFA) protections.
While the offering is clearly intended for threat actors, its creators attempt to frame it as “for educational purposes.” In this blog post, we break down the key messaging and features of SessionShark – from its MFA-bypassing capabilities to its stealth techniques and commercial pricing – and explore the implications for defenders.
A Phishing Kit Built to Defeat 2FA/MFA
At its core, SessionShark is an adversary-in-the-middle (AiTM) phishing kit that can steal valid user session tokens to defeat two-factor authentication on Office 365 accounts. The ad explicitly claims the service can “intercept sensitive data, including login credentials and session cookies,” enabling an attacker to hijack authenticated sessions.
By capturing a victim’s session cookie (the token that proves they passed MFA), attackers can bypass MFA controls and access the account without needing the one-time passcode This technique has been observed in other recent phishing kits (for example, Tycoon 2FA), and it effectively renders MFA useless if the initial credential phishing succeeds.
“Advanced” Antibot and Stealth Features
The creators of SessionShark advertise a range of anti-detection and stealth capabilities intended to maximize the success of their phishing campaigns. The promotional image calls out several features designed to thwart security scanners and researchers.

1. Advanced Antibot Technology
The kit includes techniques to avoid detection by bots and automated security scanners. The ad mentions implementing “human verification techniques to prevent redirection to warning pages or flagging by security systems.” In practice, this likely means the phishing page will present a CAPTCHA or other challenge to ensure the visitor is a real human before showing the fake login – a common trick to block web-crawling scanners from seeing the phishing content. By filtering out automated traffic (from security bots or sandboxes), SessionShark helps ensure that the phishing site isn’t automatically reported or blocked.
2. Cloudflare Compatibility
SessionShark is built to integrate with Cloudflare’s services, “tailored [for] VPS IP protections while maintaining stealth and functionality,” according to the ad. This suggests the phishing kit can be deployed behind Cloudflare, leveraging Cloudflare’s network to mask the kit’s actual hosting server and fend off takedowns or IP-based blocking. Many threat actors use Cloudflare proxying to hide their infrastructure; SessionShark makes this a supported configuration out-of-the-box, lowering the technical bar for attackers.
3. Enhanced Stealth Capabilities
Beyond antibot measures, SessionShark touts “evad[ing] detection by major threat intelligence feeds and anti-phishing systems.” The developers have added custom scripts and HTTP headers to minimize visibility to security scanners. This likely means the kit might block known threat intel crawlers, use evasive HTML/JS code (to prevent signature-based detection), or dynamically change content. Such stealth features imply that the kit was tested against security solutions to reduce chances of being flagged, demonstrating the growing sophistication of criminal phishing tools.
4. Realistic Office 365 Pages
A successful credential theft still depends on tricking the victim. SessionShark claims to “mimic the Office 365 login interface with high fidelity” and even “dynamically adapts to various conditions for increased believability.” In other words, the phishing pages look just like real Microsoft login screens, and may even handle different login workflows or error messages seamlessly. By making the user experience convincing and contextually appropriate, the kit helps attackers harvest credentials even from wary users.
5. Comprehensive Logging
SessionShark includes a logging panel for operators and, notably, Telegram bot integration. The ad describes “Instant Session Capturing” with all logs sent to a Telegram bot in real time. Integration with Telegram means a threat actor can get an alert with the victim’s email, password, and session cookie on their phone, as soon as someone falls for the phish. This kind of convenient exfiltration is rather common in phishing kits – some widely used kits like Tycoon 2FA (as previously mentioned) are also sold through Telegram channels and deliver live results to Telegram. For defenders, this means once a victim submits credentials, the attacker may take over the account within seconds, long before traditional incident response can react.
Criminal Marketing: “Educational” Spin to Subscriptions
One of the most interesting aspects of SessionShark is how it is marketed, mirroring legitimate software sales tactics. The language attempts to legitimize the tool by framing it as an “ethical hacking” or educational product, while in the same breath advertising features clearly meant for illicit abuse.
This duplicitous marketing strategy is common in underground forums – it provides a thin veneer of deniability (to avoid forum bans or legal issues) but fools no one about the true purpose. Phrases like “for educational purposes” or “ethical hacking perspective” in the ad copy are a wink and nod to buyers that this is a hacking tool, not a classroom demo.
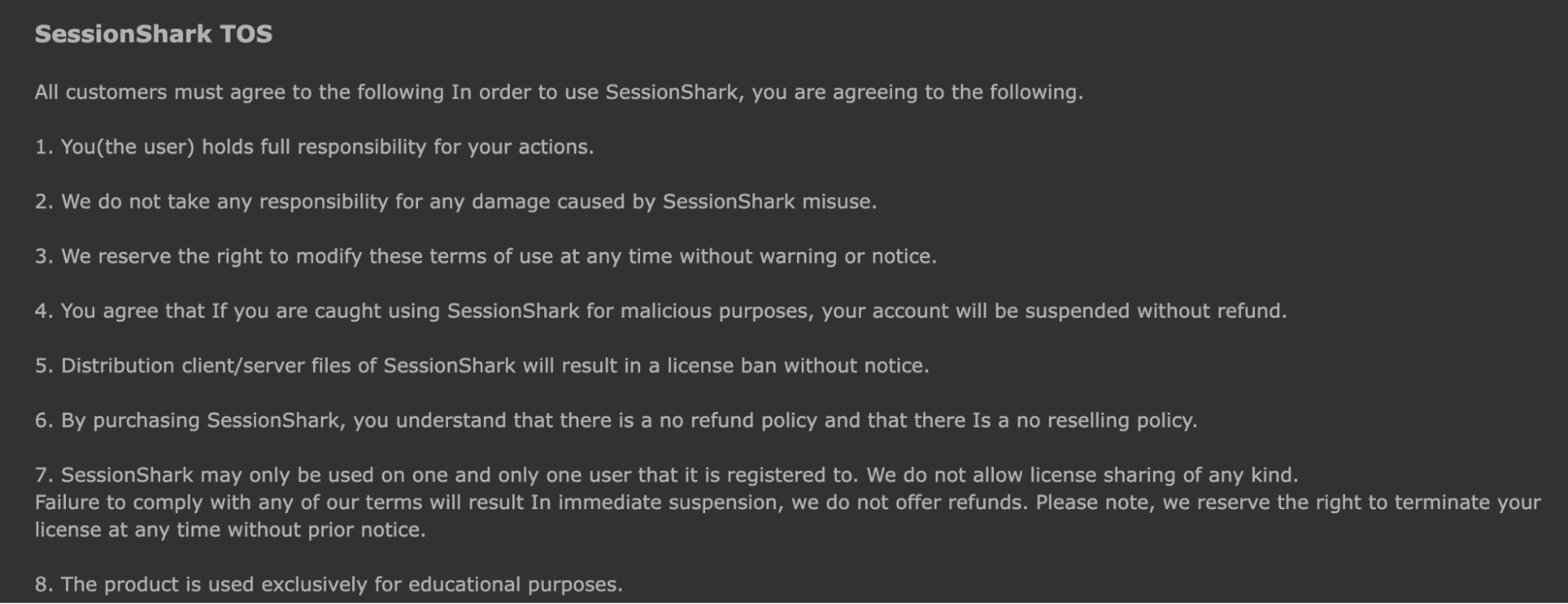
This phishing-kit-as-a-service approach indicates a broader trend in the cybercrime ecosystem: threat actors package and sell their tools with user experience and scalability in mind. Just as ransomware shifted to a RaaS model, phishing kits are now often subscription-based, ensuring the developers get a steady revenue stream and a growing user base.
For buyers, the appeal is getting a turnkey solution with updates and support. In the case of SessionShark, having a Telegram support channel means criminals can get help setting up or troubleshooting the kit – essentially, customer service for a hacking product.
Get Proactive Protection with SlashNext
SessionShark is yet another example of how cybercriminals innovate and commercialize their tactics, eroding the security benefits of MFA through clever phishing schemes. It highlights the importance of staying ahead of threat actor techniques. The good news is that as attackers up their game, so can defenders.
SlashNext is at the forefront of this battle – our AI-driven phishing defense solutions are designed to detect and block credential phishing kits and infrastructure, including sophisticated MFA-bypass attacks, before they can ensnare your users.
By leveraging broad threat telemetry and detection algorithms, SlashNext catches these threats, protecting your organization even when attackers deploy advanced tools like SessionShark that slip past traditional security.
When it comes to stopping emerging phishing-as-a-service threats, you need a solution you can trust. Contact SlashNext to learn how our technology provides 360° phishing defense – so you can stay one step ahead of even the most advanced phishing kits.


