
Imagine receiving an email that looks perfectly legitimate, down to the last detail. This is the deceptive power of new FishXProxy Phishing Kit, a new phishing toolkit emerging from the cybercrime underground. With its array of advanced features, FishXProxy dismantles the technical barriers traditionally associated with phishing campaigns, making it alarmingly simple for attackers to deceive and exploit unsuspecting victims. If you’d like to protect yourself from this kind of attack, make sure to register here.
FishXProxy advertises itself as “The Ultimate Powerful Phishing Toolkit” aimed at cybercriminals and scammers. While the developers claim it is for “educational purposes only,” the feature set and marketing clearly indicate it is designed for malicious use.
FishXProxy equips cybercriminals with a formidable arsenal for multi-layered email phishing attacks. Campaigns begin with uniquely generated links or dynamic attachments, bypassing initial scrutiny. Victims then face advanced antibot systems using Cloudflare’s CAPTCHA, filtering out security tools. A clever redirection system obscures true destinations, while page expiration settings hinder analysis and aid campaign management. Even if one attack fails, cross-project tracking allows attackers to persistently target victims across multiple campaigns. This sophisticated approach presents a significant challenge to traditional security measures.
The kit provides an end-to-end solution for creating and managing phishing sites, with a focus on evading detection and maximizing the success rate of credential theft attempts.
Advanced Antibot System
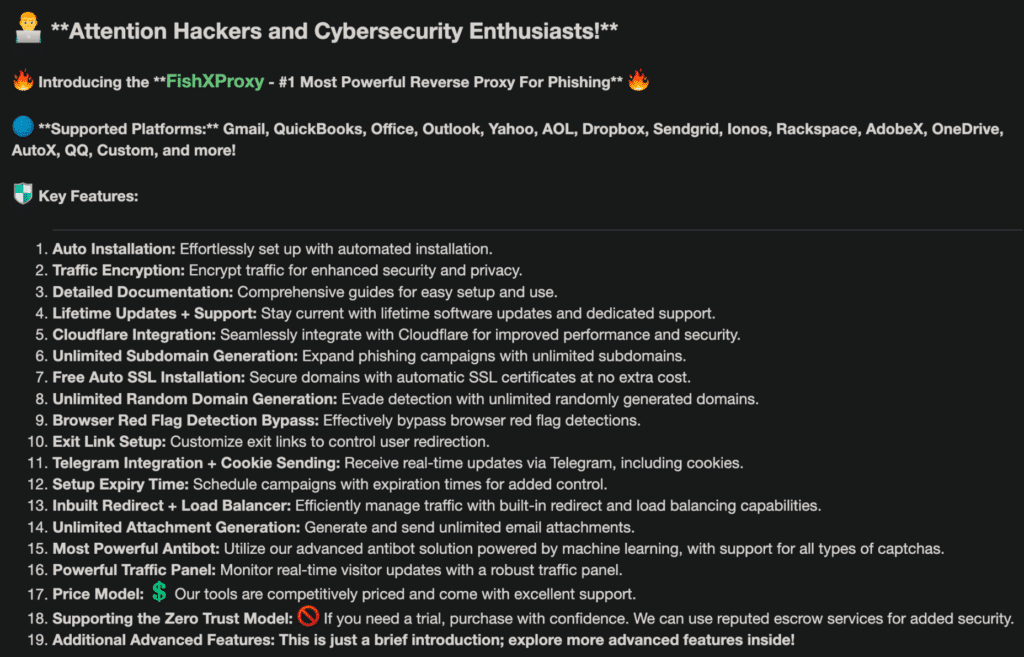
At the core of FishXProxy’s evasion capabilities is its multi-layered antibot system. This is designed to prevent automated scanners, security researchers, and potential victims from detecting the phishing nature of sites created with the kit. The antibot system offers several configuration options:
- Lite Challenge – This presents users with a simple challenge before allowing access to the phishing page. It’s described as fast, efficient and useful for small or targeted campaigns.
- Cloudflare Turnstile – Leverages Cloudflare’s CAPTCHA alternative to challenge visitors. This option requires using the kit’s built-in redirect functionality.
- IP/CAPTCHA Antibot – Described as providing “full protection”, this option first checks the visitor’s IP and behavior patterns. If flagged as suspicious, the user is presented with a CAPTCHA to solve.
- Off – For situations where the attacker wants to disable antibot protections entirely.
The IP/CAPTCHA option appears to be the most favorable, combining IP reputation checks, behavior analysis, and CAPTCHA challenges. By forcing suspicious visitors to solve a CAPTCHA, it aims to ensure “100% real traffic” reaches the phishing page.
Cloudflare Integration
FishXProxy heavily leverages Cloudflare integration, exploiting the CDN provider’s free tier, solid performance, and relatively lax internal policing to restrict phishing operations.
Several key features leverage Cloudflare’s infrastructure:
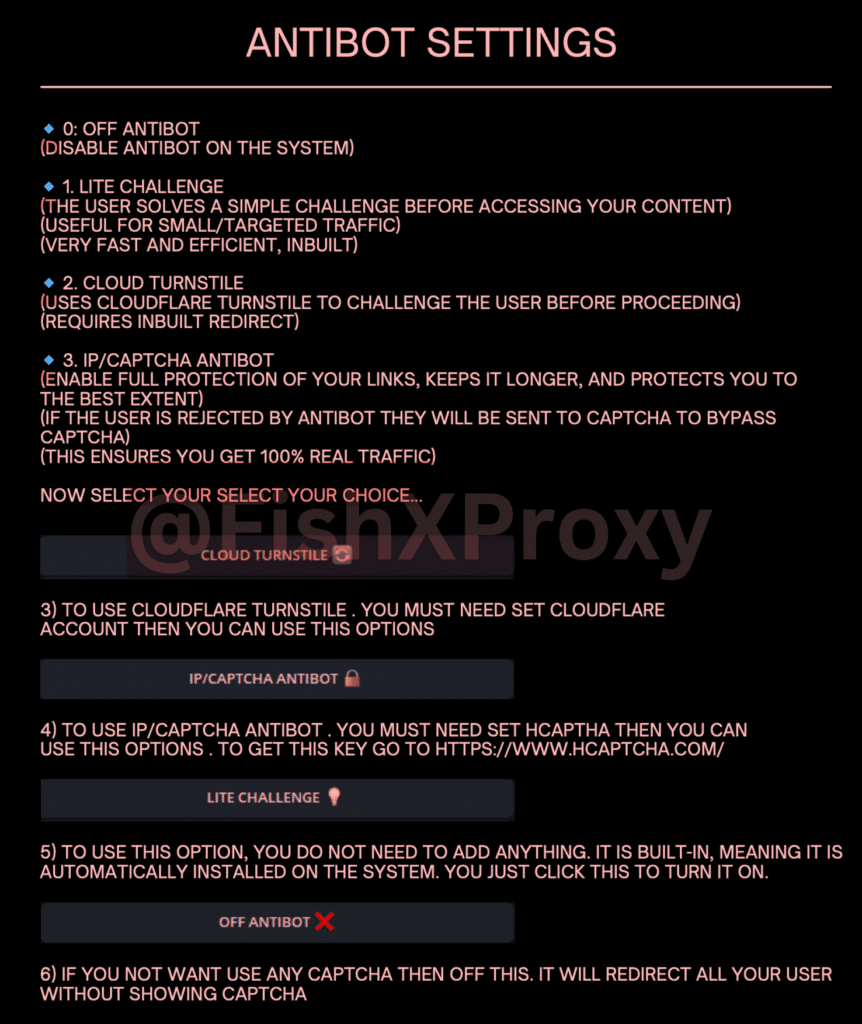
- Cloudflare Workers – The kit can deploy phishing logic to Cloudflare’s edge network using Workers. This distributed approach makes it harder to take down phishing infrastructure and improves performance.
- Cloudflare Turnstile – As mentioned, the antibot system can use Cloudflare’s CAPTCHA alternative to challenge visitors.
- SSL Certificates – The kit automates the process of obtaining SSL certificates through Cloudflare, giving phishing sites the well-known “padlock” icon in browser address bars.
- DNS Management – Phishing domains can be easily added and managed through Cloudflare’s DNS, simplifying infrastructure setup.
This deep integration with Cloudflare provides phishing operators with enterprise-grade infrastructure typically associated with legitimate web operations. It clearly raises the bar for detection and takedown efforts.
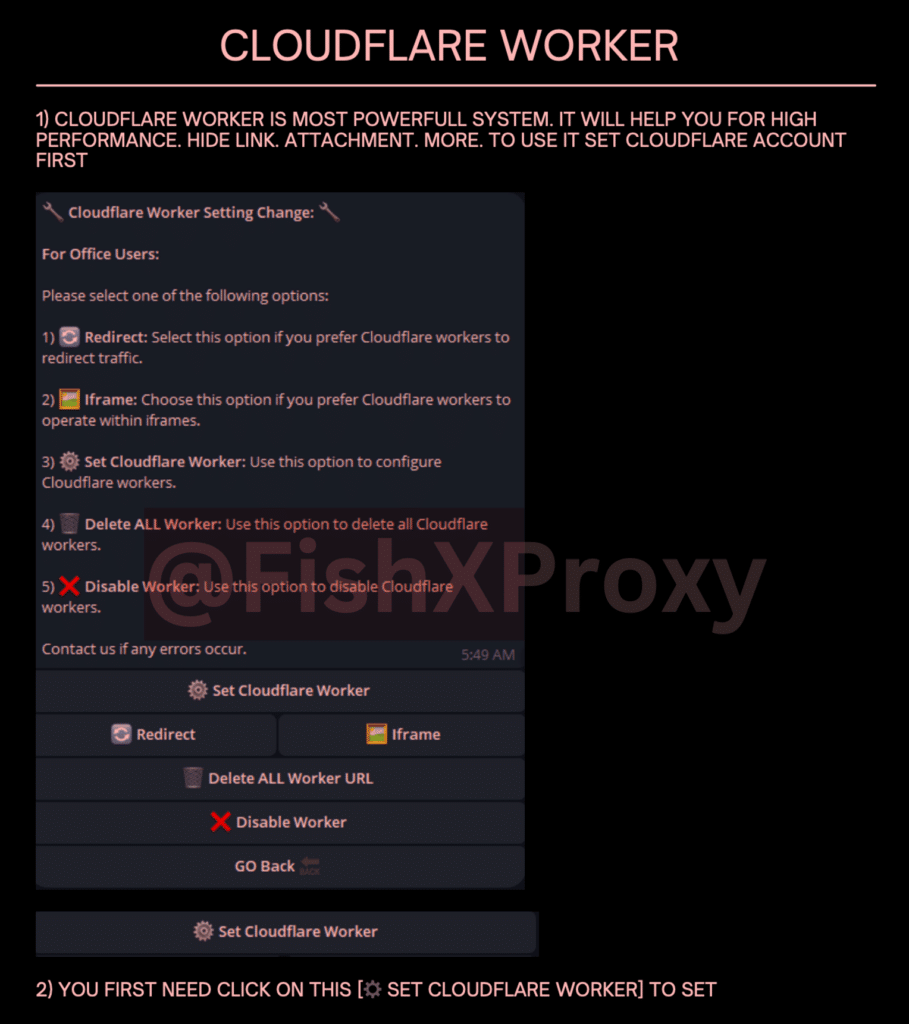
Inbuilt Redirector
FishXProxy includes a built-in redirection system that serves as both an obfuscation technique and a traffic management tool. This “inbuilt redirect + load balancer” feature allows attackers to:
- Hide the true destination of links by passing traffic through intermediary URLs
- Distribute incoming traffic across multiple phishing pages or servers
- Implement more complex traffic flows to evade detection
The redirector likely works in conjunction with the Cloudflare Workers functionality, allowing flexible and distributed control over how visitors reach the final phishing page. This makes it much harder for automated systems or manual analysis to trace the full path and identify malicious infrastructure.
Page Expiration Settings
An interesting feature of FishXProxy is the ability to set expiration times for phishing pages. This “Pages Expire Times” function allows attackers to automatically restrict access to phishing content after a specified duration.
The kit pitches this as a security feature, describing it as a way to “show unwanted guests the exit door if they overstay their welcome.” In practice, it serves several purposes for phishing operators:
- Limiting exposure – By expiring pages after a short time, the window for detection and analysis is reduced.
- Creating urgency – Short expiration times can pressure victims into acting quickly without scrutinizing the site.
- Campaign management – Attackers can automatically cycle through different phishing pages or tactics.
- Cleanup – Expired pages can be automatically removed, destroying evidence.
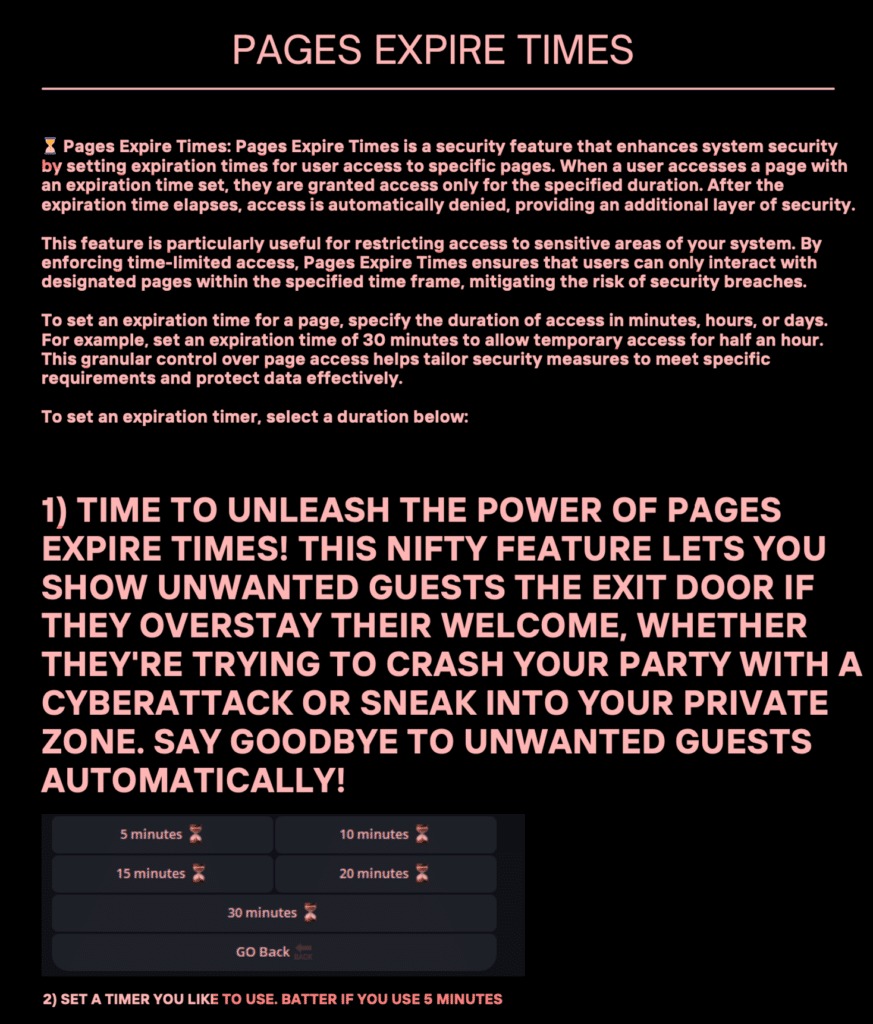
The documentation suggests setting expiration times in minutes, hours, or days, with a recommendation to use short 5-minute windows for optimal security.
Cross-Project User Tracking
FishXProxy implements a cookie-based tracking system that allows attackers to identify and track users across different phishing projects or campaigns. This “Cookies Prefix” feature lets operators specify how tracking cookies will be named in victims’ browsers.
By using consistent cookie naming across different phishing sites, attackers can:
- Identify repeat visitors
- Tailor phishing content based on previous interactions
- Avoid targeting the same user multiple times
- Build more comprehensive profiles of potential victims

The ability to track users across projects demonstrates the kit’s sophistication and potential for conducting prolonged, multi-stage phishing operations. This toolset can develop attacks that can easily evade first-gen security systems. If you are interested in protecting your organization against these attacks (in addition to learning more about them), make sure to register here
Offline HTML Smuggling Attachments
While not directly related to antibot functionality, FishXProxy’s attachment generation capabilities are worth noting. The kit can create malicious file attachments using HTML smuggling techniques.
HTML smuggling hides malicious payloads within seemingly benign HTML files. When opened, these files use JavaScript to assemble and execute the malicious code client-side, potentially bypassing email filters and other security controls.
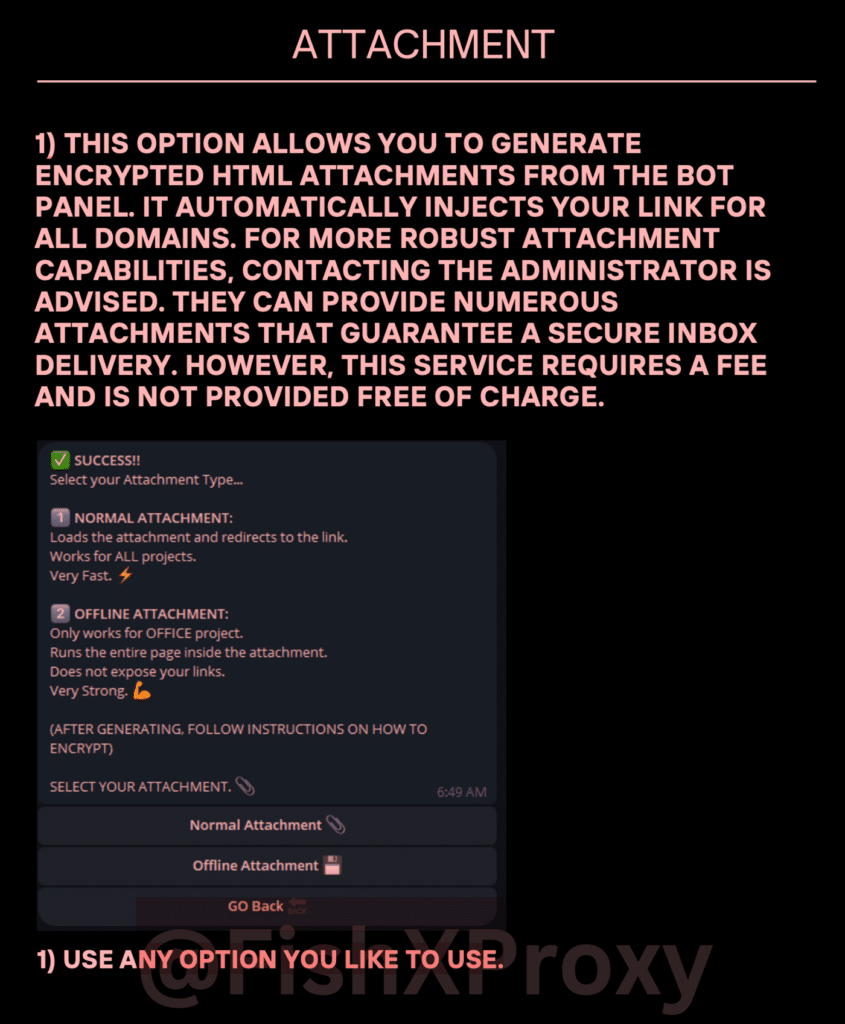
By automating the creation of these attachments, FishXProxy makes it trivial for attackers to supplement their phishing sites with malware delivery mechanisms. This expands the potential impact beyond simple credential theft to include malware infection and further system compromise.
Lowering the Bar for Cybercriminals
Perhaps the most concerning aspect of FishXProxy is how it lowers the technical barriers for conducting phishing campaigns. Features that would typically require significant expertise to implement are now available out-of-the-box:
- Automated installation and setup
- Built-in traffic encryption
- Free and automated SSL certificate provisioning
- Unlimited subdomain and random domain generation
- Browser security bypass techniques
- Real-time monitoring and notifications via Telegram
- Comprehensive traffic analysis tools
The kit even offers “lifetime updates + support,” treating phishing operations as a long-term, supported service rather than a one-off attack.
By providing these capabilities in an easy-to-use package, FishXProxy enables less technically skilled individuals to conduct advanced phishing operations. This has the potential to significantly increase the volume and sophistication of phishing attacks in the wild.
To combat phishing toolkits like FishXProxy, companies should invest in advanced, multi-layered security solutions that offer real-time threat detection across email, web, and mobile channels. Organizations should also prioritize employee education on the latest phishing tactics and implement strong authentication measures to protect against credential theft attempts.
Your Next Steps With SlashNext
To combat the growing threat of phishing kits like FishXProxy, SlashNext offers a comprehensive solution. SlashNext Complete™ is an integrated cloud messaging security platform that detects threats in real-time across email, mobile, and web messaging apps with 99.9% accuracy.
SlashNext protects organizations from data theft and financial fraud breaches by providing integrated cloud messaging security for email, browser, and mobile. Their approach helps defend against the latest phishing tactics, including those leveraging advanced techniques.



