Imagine sipping your morning coffee, scrolling through your inbox, when a seemingly innocent ProtonMail message catches your eye. But this isn’t your typical email—it’s a credential-harvesting attempt targeting specific cloud services.
Today, cybercriminals are not just focusing on well-known platforms like DocuSign and Microsoft. They’re expanding their reach, exploiting a variety of cloud apps such as Gravatar by impersonating brands like ProtonMail, telecom giants like AT&T & Comcast Infinity, and regional Canadian ISPs like Kojeko and Eastlink.
How are these seemingly unrelated services becoming gateways for cyber threats, and what can you do to protect yourself?

The Expanding Battlefield: Beyond the Usual Suspects
Credential harvesting has long been associated with major platforms, but the landscape is rapidly changing. Attackers are now leveraging a diverse array of cloud applications to steal login information. Gravatar, a service that manages avatars across the web, might seem harmless, but it’s become a prime target for cybercriminals. By exploiting Gravatar’s “Profiles as a Service,” attackers create convincing fake profiles that mimic legitimate services, tricking users into divulging their credentials.
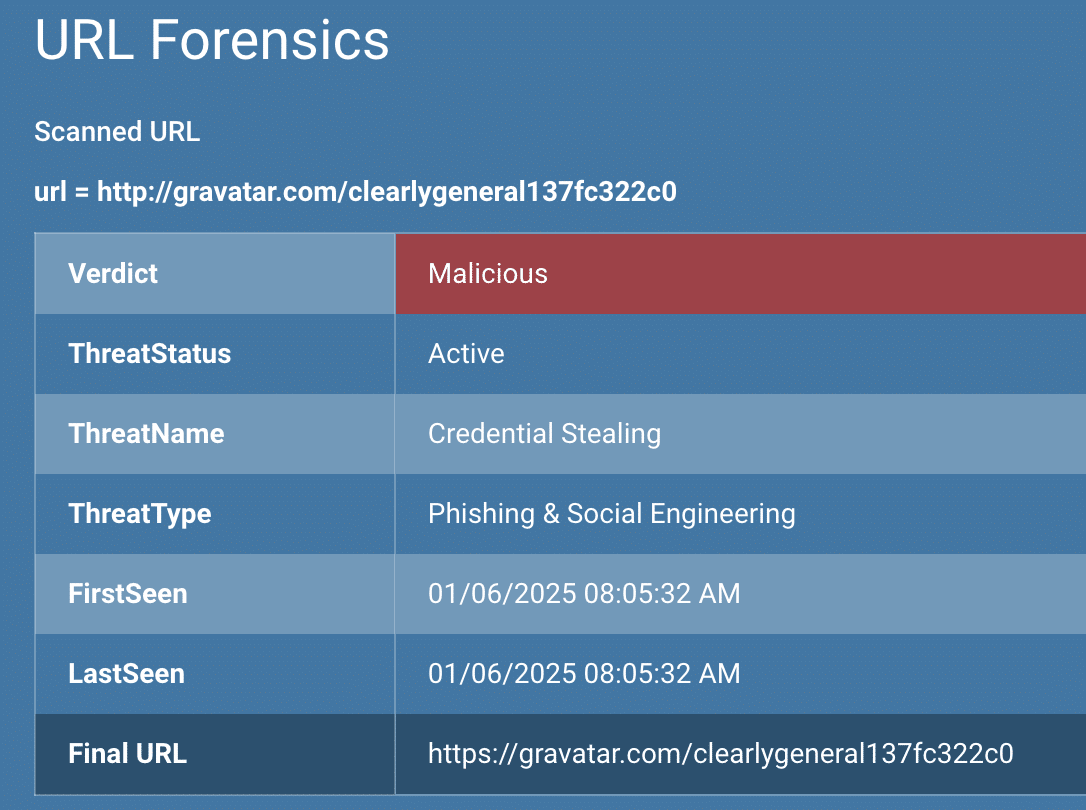
Why Cloud Apps?
You might ask, why are attackers using these large logos and launching attacks through these smaller, more specific cloud apps? The answer lies in these companies widespread use and users’ trust in them. At the same time services like Gravatar are not often known or blocked in most environments and won’t set off any alarm bells, making them attractive targets.
Telecoms Under Attack: The AT&T, Comcast Xfinity, and Canadian ISPs Case
Telecommunications companies like AT&T, Comcast Xfinity, and Canadian ISPs Kojeko and Eastlink are being leveraged for credential harvesting attacks because users trust these brands. These companies hold vast amounts of user data, making them lucrative targets as well if accounts can be exploited. By compromising their ISP cloud-based profiles, attackers can gain access to sensitive customer information, potentially leading to larger scale data breaches and further exploitation.

Telecom services are the backbone of our digital communication, and their compromise can have far-reaching consequences for users. Attackers targeting AT&T and similar providers aim to exploit the trust and extensive data these companies manage, increasing the potential impact of their malicious activities.
The Mechanics of Modern Credential Harvesting
- Initial Contact: Attackers send phishing emails that appear to come from trusted services or companies.
- Deceptive Links: These emails contain links directing users to fake credential-harvesting pages designed to steal login information.
- Impersonation: The fake profiles mimic legitimate services, making it difficult for users to recognize the deceit.
- Data Theft: Once users enter their information, attackers gain access to their accounts, leading to potential data breaches and further exploitation.
Unique Customized Impersonations
What sets modern credential harvesting apart is using unique, customized impersonations. Instead of generic phishing attempts, attackers tailor their fake profiles to resemble the legitimate services they’re mimicking closely through services that are not often known or protected (e.g. Gravatar). Whether a ProtonMail interface, a telecom login page like AT&T’s, or a Comcast Xfinity portal, these impersonations are designed to be as convincing as possible, increasing the likelihood of users falling for the scam.

Protecting Yourself from Credential Harvesting
Understanding the tactics used in credential harvesting is the first step in safeguarding your information. Here are practical steps to protect yourself:
- Verify URLs: Always check the URL of the page you’re visiting. Ensure it matches the official website of the service you’re using.
- Be Cautious with Emails: If you receive unexpected emails requesting personal information, verify the sender’s legitimacy before clicking any links.
- Use Strong, Unique Passwords: Implementing strong, unique passwords for each of your accounts can prevent attackers from accessing multiple services if one password is compromised.
- Enable Two-Factor Authentication (2FA): Adding an extra layer of security makes it harder for attackers to gain access, even if they have your password.
- Stay Informed: Keep up with the latest cybersecurity trends and threats to recognize and respond to potential attacks promptly.
Conclusion: Stay Vigilant, Stay Secure
Staying informed and vigilant is your best defense for these threats. From Gravatar and ProtonMail to telecom giants like AT&T and Comcast Xfinity, along with more regional targets like Canadian ISPs like Kojeko and Eastlink, cloud services play a crucial role in our online interactions. However, if not properly secured, they can also become tools for cybercriminals. By understanding the tactics used in credential harvesting and adopting robust security measures, you can protect yourself and your valuable information from falling into the wrong hands.
How do you stay safe from threats? Stop the phishing email before it gets to your users by using SlashNext’s Email+ Protection and add an extra layer of protect with SlashNext’s Browser Phishing Protection. It works inside your browser, spotting zero-hour phishing sites before they get you. It’s cloud-powered, fast, and works on all major browsers. With SlashNext, you get real-time defense that stops attacks cold.


