Cyberattacks are becoming increasingly common and sophisticated. One particular concern is the rising misuse of popular platforms like Airbnb. This blog post highlights how cybercriminals exploit Airbnb for fraudulent activities.
Cybercriminals Target Travelers
Cybercriminals are constantly developing new ways to exploit popular online platforms for malicious purposes. With over 7 million global listings in 100,000 active cities, Airbnb has become a favorite target for these criminals.
While the platform offers affordable and comfortable accommodations for travelers, its popularity has also made it vulnerable to cybercriminals, fraudulent hosts, fake accounts, and other scams. This blog post will explore how cybercriminals exploit Airbnb and its users.
Inside The World of Stealers
In order to understand how cybercriminals exploit Airbnb, it’s crucial to comprehend the methods they use to gain unauthorized access to accounts. Cybercriminals often employ malicious software known as “stealers” to obtain information such as usernames and passwords. These stealers, which are a type of malware, infiltrate devices and transmit stolen data (also known as logs) to attackers. Typically, the logs are sent to a server, but in some cases, they can be delivered through e-mail and secure chat programs like Telegram.
Stealers can be deployed through a variety of different techniques, including social engineering, exploiting software vulnerabilities, malvertising, and more.
Additionally, there’s an underground market where cybercriminals can buy and sell device access (also known as bots, installs, or infections) in large quantities.
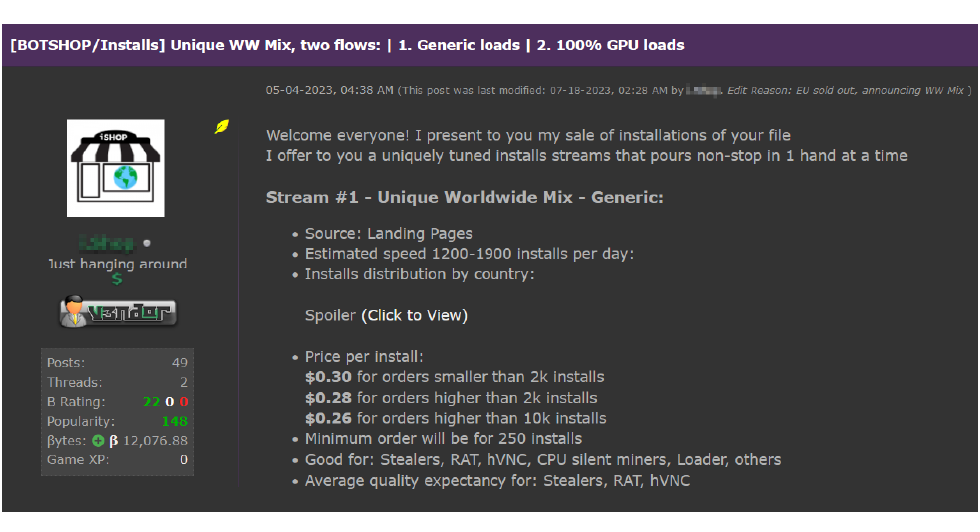
Photo: A screenshot of a cybercriminal offering bots for sale on a forum
Cybercriminals who are willing to invest money can approach a bot seller or shop and start deploying their stealer on thousands, or even tens of thousands of devices, right away.
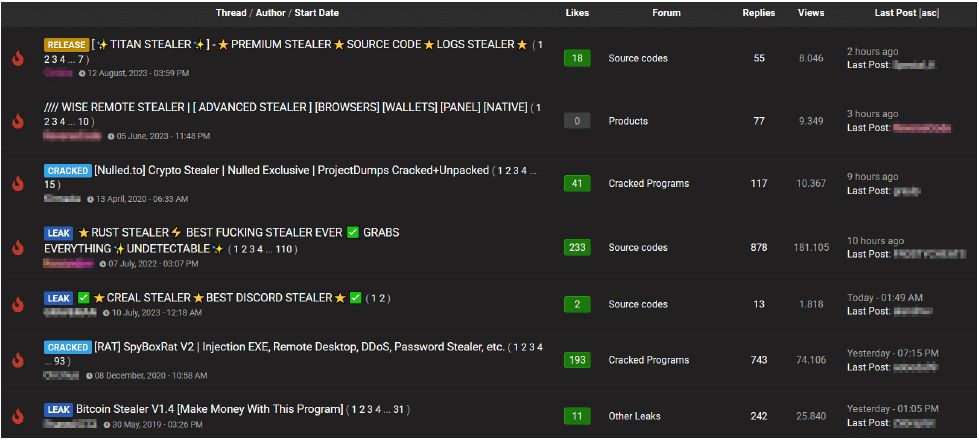
Photo: A screenshot of the different stealers available on a prominent cybercrime forum
Stealers can compromise most browsers, and they primarily target web-application account information. The logs usually follow a particular format, which includes multiple columns with rows of data that encompass various pieces of information, such as names, credit or debit card details, and more. In addition to capturing login credentials, stealers can also exfiltrate cookies.
The Importance of Cookies
Cookies are small data files stored on a user’s device that contain information about their browsing activity and preferences on a particular website. Cybercriminals often steal, buy, and sell Airbnb account cookies on various online forums. By doing so, they can gain temporary access to Airbnb accounts without needing the relevant usernames and passwords.
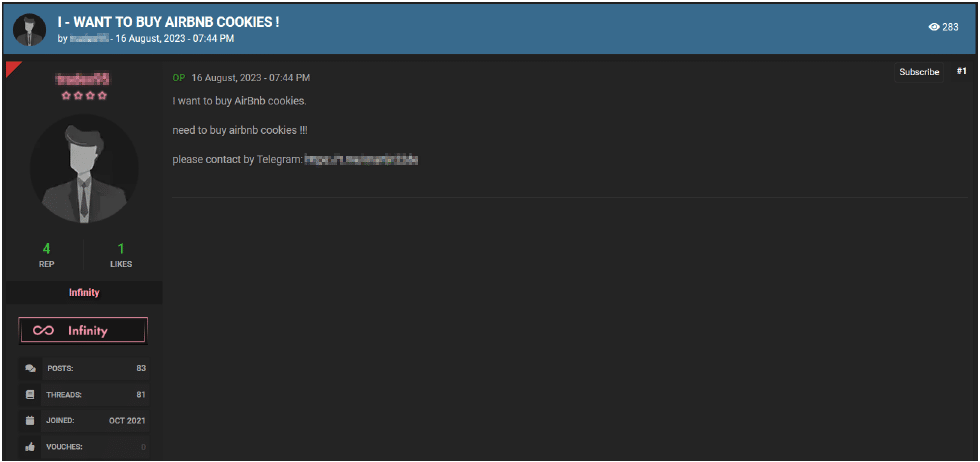
Photo: A screenshot of a user on a cybercrime forum looking to purchase Airbnb cookies
For instance, cybercriminals can purchase databases of stolen Airbnb cookies from compromised accounts, load them into their browser, and gain access to victims’ accounts. With this illicit access, they can impersonate real users and book properties or perform other unauthorized actions without raising any alerts. However, it’s crucial to note that most session cookies expire quickly, so cybercriminals must act fast before the session expires.
The Lucrative Services Available
Once cybercriminals gain access to user account information or obtain stolen cookies, their next objective is often to profit from the data. One standard method is to sell the compromised account information or stolen cookies directly to other cybercriminals.
This can be accomplished through advertising on online forums or by uploading rows of data to popular stores that facilitate these types of transactions.
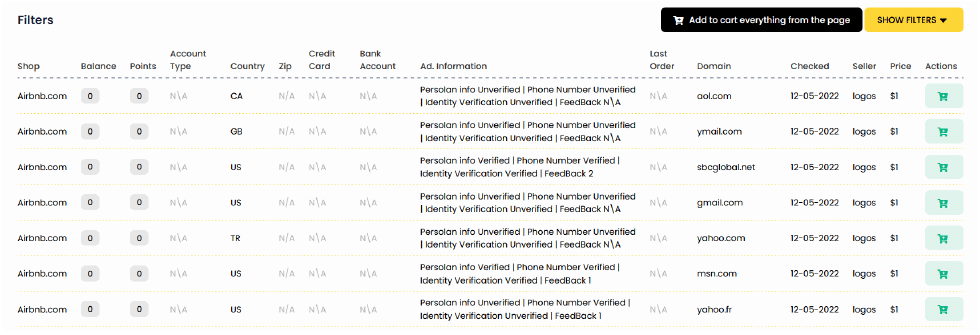
Photo: A screenshot of a popular cybercrime store offering Airbnb accounts for sale
At the time of writing this blog post, there are thousands of Airbnb accounts available for purchase on the digital store referenced above. Shockingly, the large number of stolen accounts has devalued each account to just one dollar.
In fact, the scale of Airbnb account theft is so significant that attackers sell “account checkers,” which are automated programs that rapidly test Airbnb accounts located in a text file.
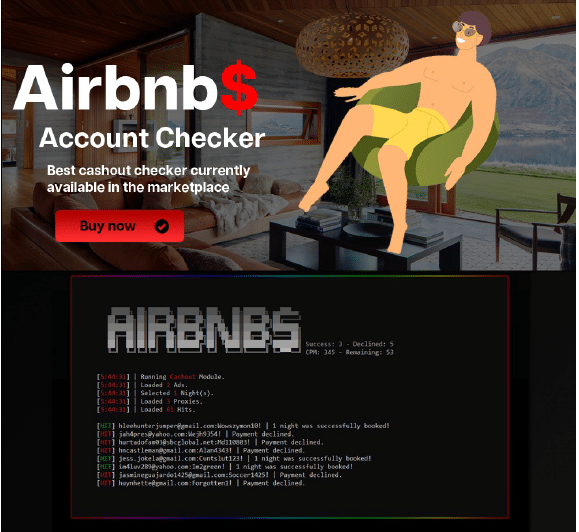
Photo: A screenshot of an advertisement for an Airbnb account checker
The concept behind these account checkers is relatively simple. Attackers can load a text file filled with stolen credentials into the checker, verifying which credentials are valid and which are not. Some checkers can also perform specific actions, such as making bookings.
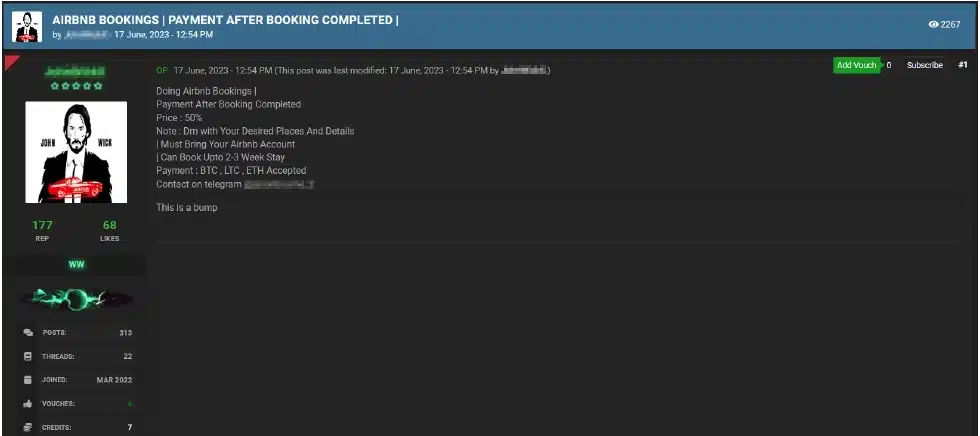
Cybercriminals also offer services that provide up to a 50% discount on Airbnb bookings.
Photo: A screenshot of a service that offers a 50% discount on all Airbnb bookings
It’s clear that these services are profitable because the forum threads advertising them have received tens of thousands of views and hundreds of replies.
In conclusion, cybercriminals have discovered various methods to exploit Airbnb for fraudulent activities by using stealers and stolen cookies to gain unauthorised access to user accounts. The compromised information is then sold to other cybercriminals or used to offer discounted services to buyers. The scale of account theft is substantial, with thousands of Airbnb accounts available for purchase on digital stores for as low as one dollar. It is essential to be aware of the risks and take necessary precautions to protect personal information from such cyber threats.
Browser Security With SlashNext
If you’re looking for integrated browser security, we have a solution for you. Our HumanAI technology offers real-time detection with exceptional accuracy that identifies malicious websites. By blocking threats in real time, we can safeguard users from malicious content that bypasses multi-layer enterprise defenses.
To book a demo, click here or watch the short video to learn more about our product: SlashNext Browser Phishing Protection