
It’s no secret that cybercriminals love to exploit our trust in well-known brands. From big-name retailers to popular online services, attackers will latch onto anything that seems safe. In this post, we will explore a real-life example of this: the abuse of DocuSign’s actual application to deliver malicious links. Then, we’ll dive into how our new URL analysis functionality can expose these hidden threats in real-time. Think of it as a detective story where DocuSign is the unwitting getaway car, and our URL analysis tool is the forensics team piecing together the entire crime scene.
The DocuSign Dilemma: Real Emails, Real Danger
In recent months, attackers have abused trusted cloud application infrastructure much more frequently to launch their scams. They send out a request from a legitimate DocuSign email sender, complete with the real DocuSign branding and professional design. Unlike a typical phishing email that tries to imitate DocuSign, these attackers use legitimate DocuSign accounts—either free ones they’ve signed up for or compromised accounts they’ve hijacked. This means any email you receive from these attackers truly comes from DocuSign’s servers, with no spoofing involved. The unsuspecting recipient clicks on the link in the email, assuming that everything is on the up and up.
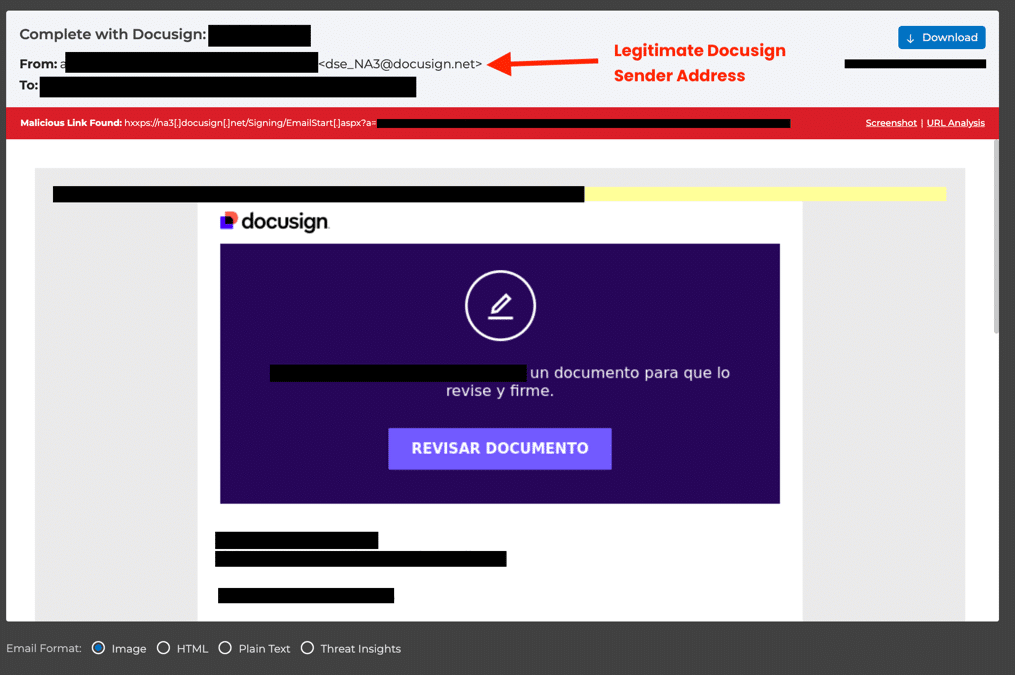
The danger lies in what’s inside the document or message. Attackers upload malicious links or files to an actual DocuSign workspace. When DocuSign does what it’s supposed to—send an official-looking email to let you know you have a document to sign—most people assume it’s safe. After all, it comes from a known domain and includes real DocuSign branding. But one click on that link can create a chain reaction of redirects that eventually land you on a page designed to steal your login credentials or deliver ransomware to your system.
Because the email and initial page are genuinely hosted on DocuSign’s infrastructure, traditional security filters often give them a pass. We’ve added an extra layer of AI-driven analysis—using computer vision and natural language processing—to recognize malicious content that might otherwise blend into a real DocuSign document. By the time you or your security tools realize something is off, you’ve already followed the trail to a malicious site.
A Layered Attack Hiding Behind Trust
What makes these attacks so sneaky is their layered nature. Once you open the legitimate DocuSign document, you might see a link or a QR code that points to a second website. That site might look harmless at first, but it can hide more redirects or malicious code. Our AI capabilities can automatically interpret each page along the redirection chain—spotting suspicious logos, hidden text, or unusual language patterns before you ever realize you’ve been sent somewhere dangerous. Some attacks even branch into multiple steps, forcing you to pass through several web pages before finally landing on a credential-harvesting form or a file-download prompt carrying malware.
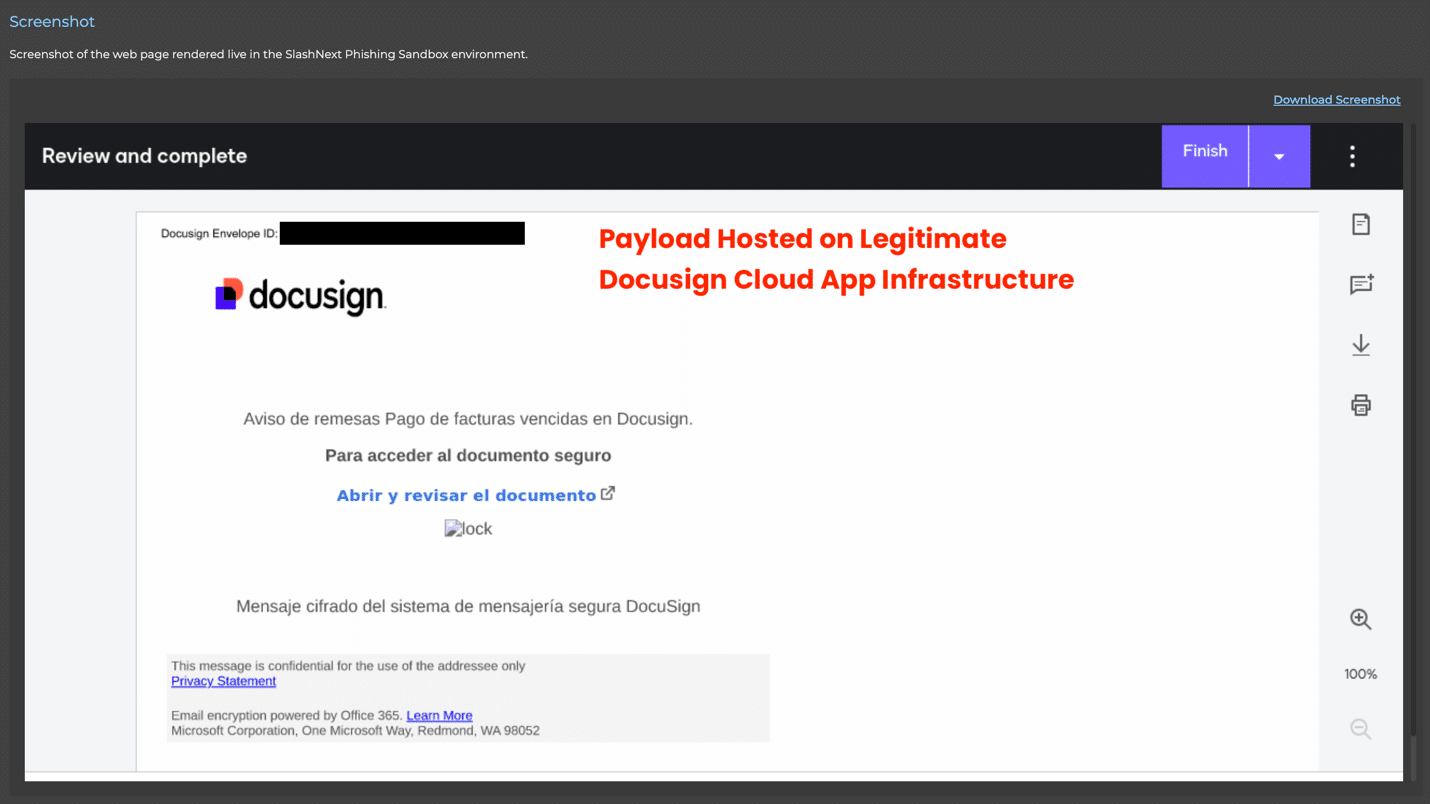
Each layer of redirection helps the attackers stay one step ahead of detection. Security tools that scan only the first domain might see nothing wrong, because DocuSign itself is trusted. By the time the tool inspects the final page, the link may have changed, or the site might have gone offline. It’s a game of cat and mouse that relies on short-lived malicious pages and the good reputation of DocuSign.
How Our URL Analysis Reveals the Full Story
This is where our advanced URL analysis tool steps in. Instead of relying solely on static lists of known bad links—which can quickly become outdated—our tool performs live, in-depth scanning of every unknown URL, even those that have never been seen before. When a URL is analyzed, our tool follows every redirection, tracking the journey from the original link to its final destination.
In the process, the tool gathers a wealth of information that paints a complete picture of the potential threat. For example, it shows:
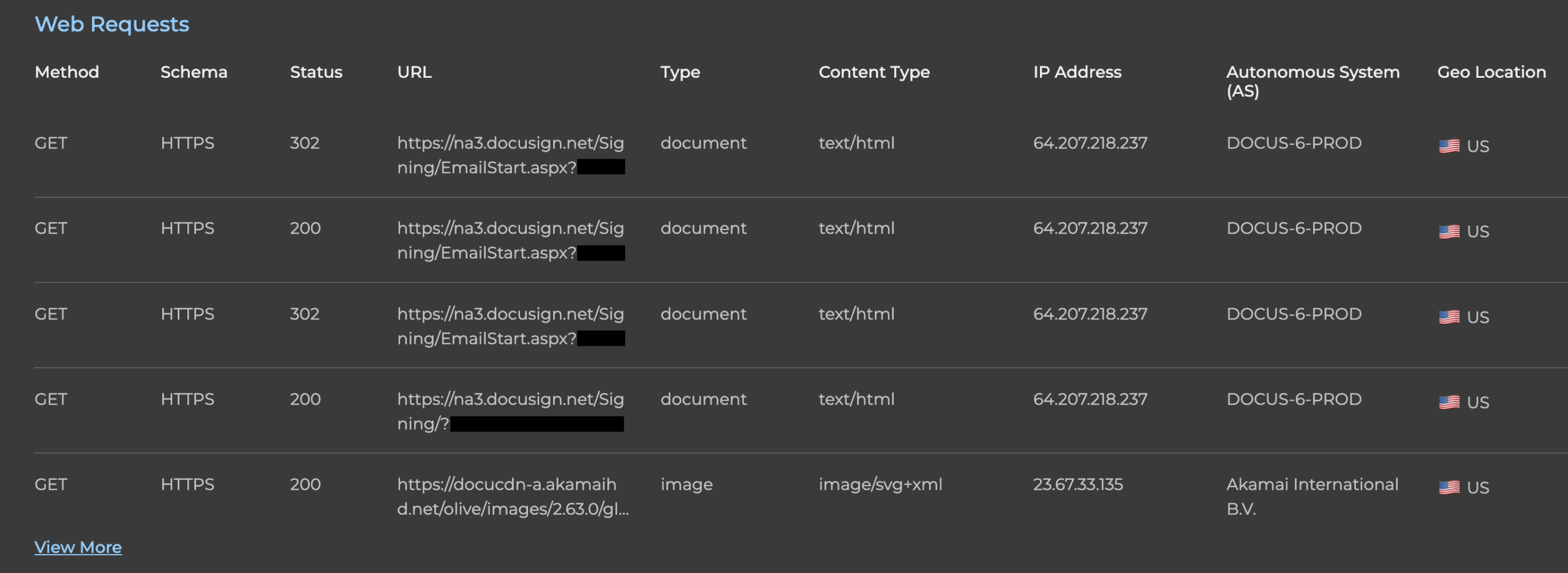
- Every web request made along the journey: From the original URL to every redirection, including details like the method, status, and content type.
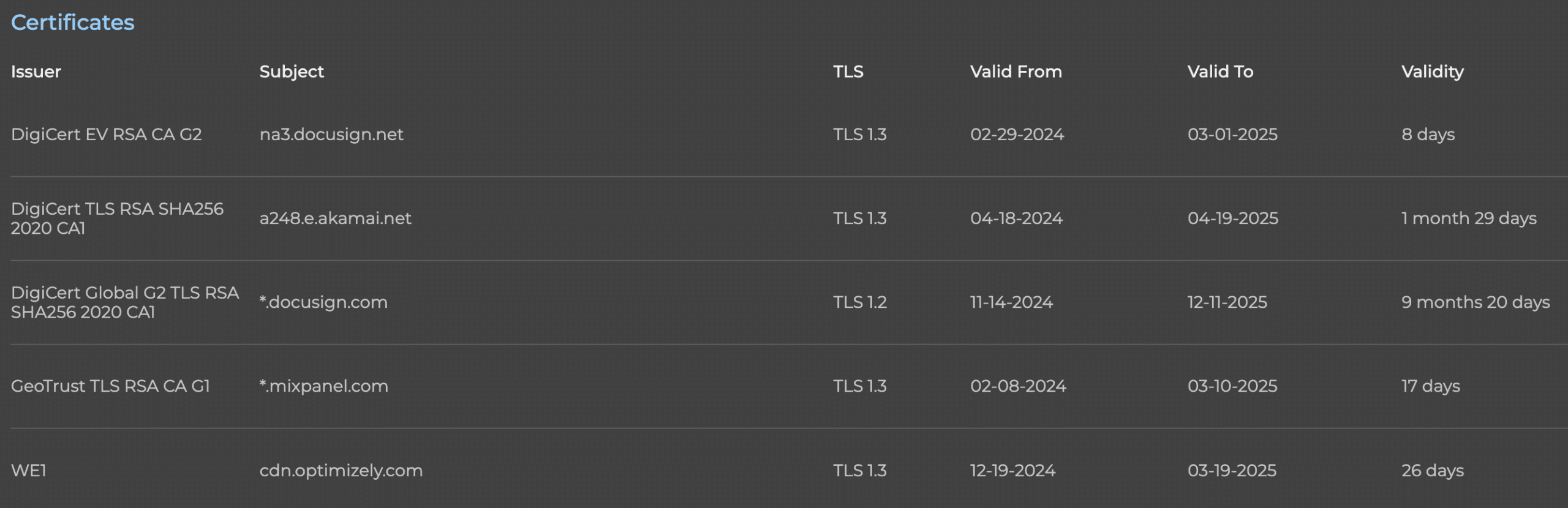
- Certificate details: It checks who issued the security certificate, when it’s valid, and other important metadata.
- Visual snapshots: Screenshots capture what the page looks like at key moments, especially when the content appears suspicious.
- Redirect Chain – Every hop from the initial DocuSign link to the final landing page, along with HTTP methods and status codes.
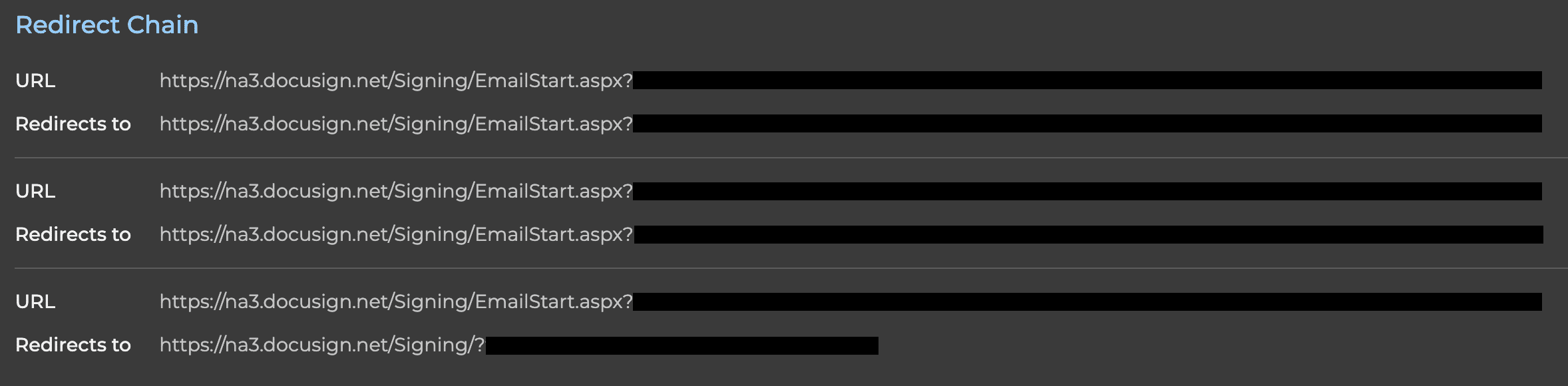
- Obfuscation detection: The tool can identify nested links, QR codes, and other attempts to hide malicious content.
By combining AI-powered computer vision with advanced NLP, we can identify subtle red flags—like brand impersonations or misleading text—that slip past traditional scanning. After compiling all this information, our URL analysis tool doesn’t just tell you that a link is bad—it shows you exactly how the URL portion of the attack was constructed, step by step. This detailed report is invaluable for security teams, as it provides them with all the clues needed to understand the attack and to take appropriate measures to block it.
Because we follow the entire journey, we can spot malicious behavior in real time, even if the link changes or the final site only stays up for a short while. Our system also uses computer vision and natural language processing to read the page the same way a person would—scanning for dangerous text, suspicious forms, and other indicators of a scam.
Why This Matters
With legitimate DocuSign emails, spotting something fishy at a glance is almost impossible. Even security teams can be fooled because there’s no obvious forgery or imitation. That’s what makes these attacks so potent. When an email truly comes from DocuSign’s infrastructure, people are more likely to trust it, and spam filters rarely block it.
Our URL analysis tool cuts through that confusion by revealing the entire sequence of events. Instead of checking just the front door (DocuSign’s domain), we follow every hallway and side passage until we find out exactly where the link is trying to take you. This level of detail doesn’t just help you stop a single attack—it helps you understand the methods attackers use so you can train your team and refine your defenses against future threats.
Conclusion: Stay Vigilant, Stay Curious
DocuSign isn’t the problem—bad actors are. Since DocuSign is a recognized and widely trusted brand, it’s a cloud app that has become a convenient vehicle for delivering malware or phishing pages. The good news is that you can fight back with tools that go beyond traditional filtering. By using URL analysis that investigates each step of the redirection process, you stand a far better chance of catching these clever attacks before they compromise your data.
So, pause momentarily the next time a DocuSign email lands in your inbox. Even if everything looks normal, remember that attackers use legitimate services in illegitimate ways. The only difference is that their end goal is malicious. By pairing a healthy dose of skepticism with a robust, real-time analysis solution, you’ll be well-equipped to spot these hidden threats and keep your organization safe.
At SlashNext, we don’t just react to threats—we redefine email security. Our AI-based approach delivers speed, accuracy, and continuous innovation so businesses can stay protected without slowing down.
What information are you missing out on? Fill out the contact form to learn more about our URL Analysis capabilities and how we uncover these complex attacks.


