
In the world of cybersecurity, it often feels like we’re revisiting familiar problems, albeit with a modern twist. The essence of the issue isn’t about the emergence of entirely new types of cyberattacks but rather how attackers ingeniously reinvent old tactics. A prime example of this is obfuscation—a method deeply rooted in the annals of history, such as the Caesar cipher, famously used by Julius Caesar. The Caesar cipher, an encryption technique used by Julius Caesar over two millennia ago, was a rudimentary yet effective form of obfuscation that allowed him to pass encoded messages to his generals. It relied on shifting the alphabet to keep messages secret from prying eyes. Fast forward to today, and we see the same principles at play in obfuscated phishing scams when we see folks using ROT13 cipher, but they add many other techniques at a level of complexity that Caesar could never have imagined. These methods were designed to make information unintelligible, a strategy that has not only persisted but evolved.
Today, obfuscation attempts to confound the advancements of machine learning and sophisticated text analysis, making it a formidable tool in the cyberattacker’s arsenal. Despite technological progress, deciphering these obfuscated messages remains a challenge for a lot of tools. Attackers blend old-school techniques with modern technology to bypass security measures. Let’s look a sample phishing threat we caught in the wild.
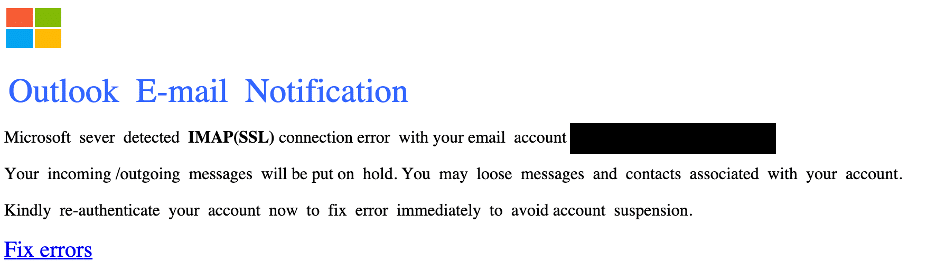
Take, for instance, a seemingly benign request to update IMAP/POP settings. While a cybersecurity expert might immediately sense something amiss, the average user could easily be led astray. One of the most sinister manifestations of this strategy is found in these phishing emails, a domain where attackers exploit the thin line between familiarity and deception. When we use SlashNext to look at the HTML view, nothing stands out heavily beyond the obvious IMAP Settings request. Now, when we look at the Image view though this message starts to look a little odd. Notice the weird spacing below?
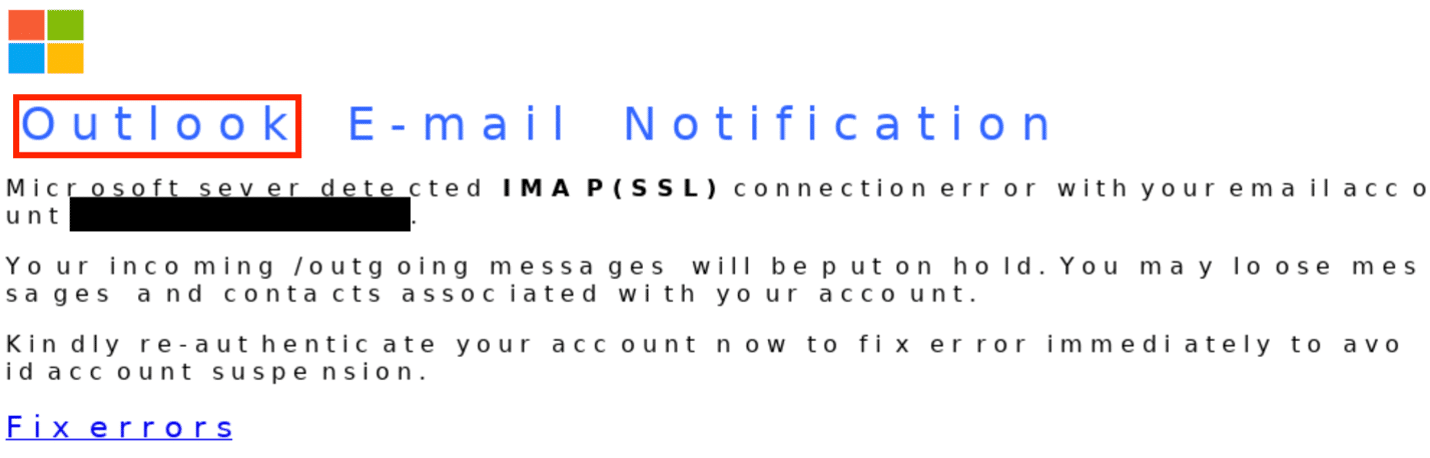
We can see something is up, and as we dig into the Plain Text View we see a common obfuscation trick in their playbook, typical of what we see at SlashNext regularly. The familiarity of this email from “Outlook” is precisely what attackers count on. Hidden within what seems to be a mundane part of an email is a string of characters and numbers designed to obfuscate the real intent: ‘O 4236 u 7982 t sent from thanks. l 9851 o 6777 o 5739 k’. To the untrained eye, the word ‘Outlook’ is lost in this jumble, showcasing a clever use of obfuscation to hide malicious intent in plain sight.
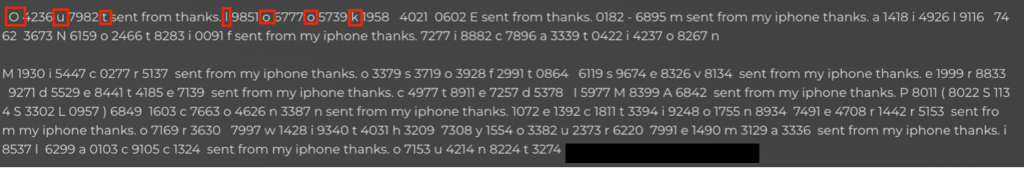
Moreover, the tactic of inserting ‘sent from my iPhone thanks’ attempts to feed normal language to disrupt natural language processing to replicate the signoffs of genuine messages, further adding a layer of authenticity to deceive the recipient. This strategy is not just about concealing malevolent purposes but also about creating an email that mirrors the ones we receive and trust daily, exploiting our familiarity to breach defenses.
Such sophisticated ploys underscore the limitations of traditional cybersecurity approaches. As attackers continually refine their methods, using obfuscation to mask dubious requests or embed malicious content in seemingly innocuous emails, the need for advanced detection tools becomes evident. Solutions like SlashNext offer a glimpse of hope, equipped to identify anomalies that might otherwise go unnoticed, such as unusual spacing or the presence of hidden strings and numbers within what appears to be straightforward text.
The reliance on user vigilance or basic cybersecurity tools is no longer sufficient to combat these stealthy attacks. The complexity and cunning nature of these strategies demand a more sophisticated response, one that can preemptively identify and neutralize threats before they inflict harm.
As we navigate the digital age, the constant threat of being duped into compromising our security looms large. However, the goal is not to eradicate an unfixable issue but to stay ahead of adversaries. With the right tools and a comprehensive understanding of modern obfuscation techniques, we can confront these challenges, safeguarding our digital environment against the evolving landscape of cyberthreats.
We invite you to join us in the fight against modern advanced phishing attacks. Embrace the legacy of the ancient emperors who leveraged the strongest tools to stay ahead of those seeking by arming yourself with the next generation of cyberdefense. You and your customers deserve nothing less than the best. Take a look around the SlashNext site and discover how we can help you decipher the undecipherable, ensuring that your organization remains impervious to the ever-evolving tactics of cyber adversaries. Stand with us, and let’s secure the future by learning from the past.
Discover how SlashNext can extend your protection across email, mobile, and web messaging apps. Request your personalized demo today.


