
Phishing attacks continue to evolve, pushing even the most secure authentication methods to their limits. First advertised on cybercrime networks in late January 2025, Astaroth is a brand new phishing kit that bypasses two-factor authentication (2FA) through session hijacking and real-time credential interception.
Astaroth utilizes an evilginx-style reverse proxy to intercept and manipulate traffic between victims and legitimate authentication services like Gmail, Yahoo, and Microsoft. Acting as a man-in-the-middle, it captures login credentials, tokens, and session cookies in real time, effectively bypassing 2FA.
What Makes Astaroth Unique
Astaroth distinguishes itself by not only intercepting login credentials but also by rapidly capturing 2FA authentication tokens and session cookies as they are generated. This real-time interception, enabled by a reverse proxy mechanism, allows attackers to bypass 2FA defenses with remarkable speed and precision.
In contrast, traditional phishing kits typically rely on static fake login pages that capture only primary credentials, often leaving the 2FA layer intact. By dynamically intercepting all authentication data in real time, Astaroth significantly raises the bar, rendering conventional phishing methods and their inherent security measures largely ineffective.
How Astaroth Works
Having introduced Astaroth and highlighted its innovative approach to bypassing traditional security measures, let’s explore the detailed mechanics of how this phishing kit operates within the context of an attack. The attack begins when victims click a phishing URL, which redirects them to a malicious server operating as a reverse proxy. This server mirrors the target domain’s appearance and functionality while relaying traffic between the victim and the legitimate login page.
With SSL certificates issued for the phishing domain, victims see no security warnings and believe they are on the real site. Astaroth forwards user requests to the legitimate service while stealthily intercepting responses and sensitive data.
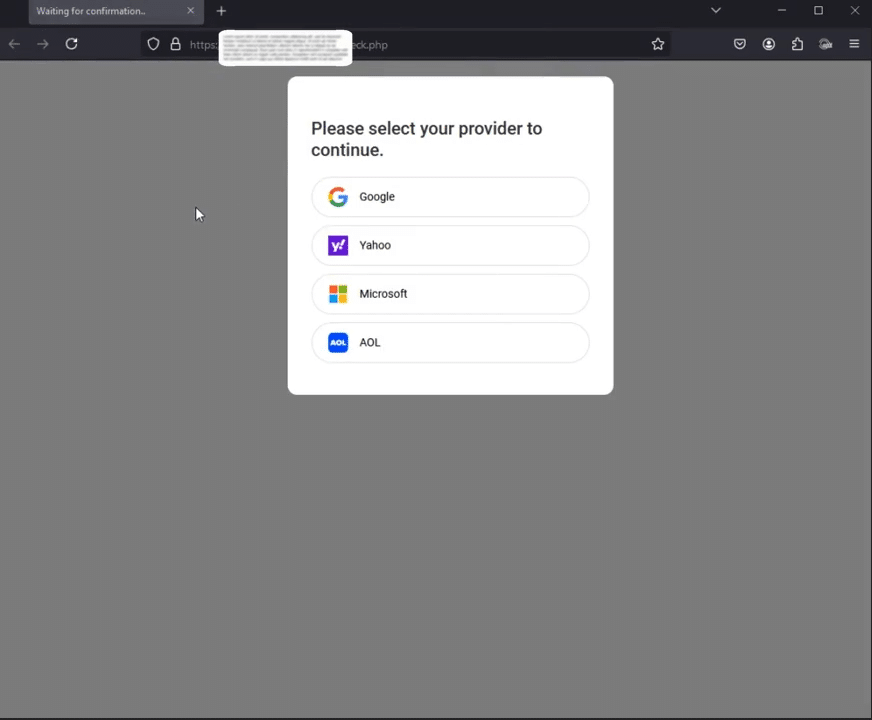
When victims enter their login credentials (username and password), user agent string, and IP address on the phishing page, Astaroth captures them before forwarding the request to the legitimate server. The user agent and IP address allow attackers to replicate the victim’s session environment and reduce detection risks during login.
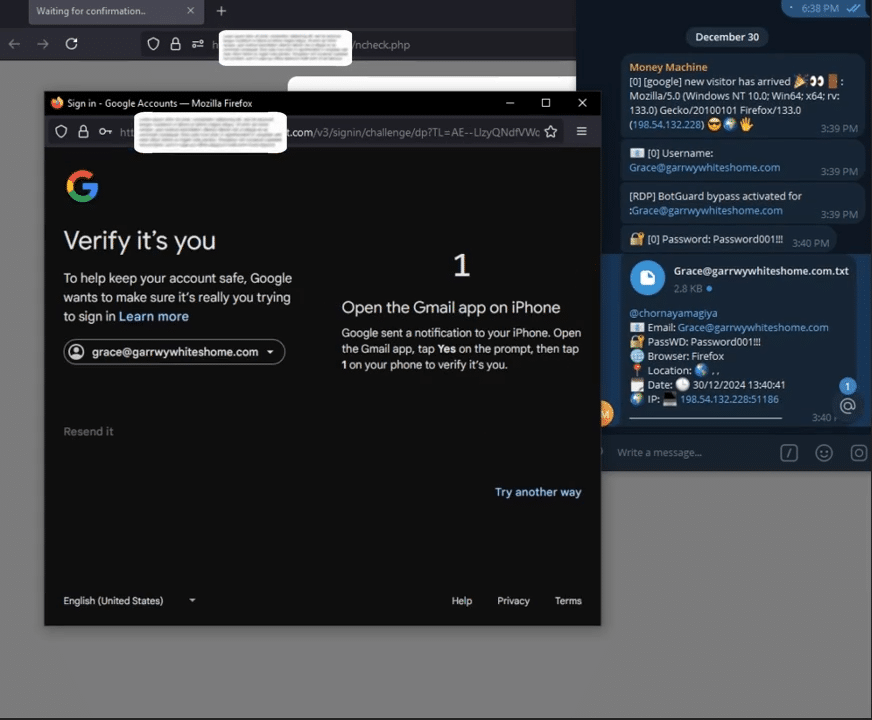
Because 2FA is always involved (e.g., via SMS codes, authenticator apps, or push notifications), Astaroth automatically captures the entry of the 2FA token in real time. It also ensures that any token entered by the victim is intercepted immediately—the attacker is instantly alerted through a web panel interface and Telegram notifications.
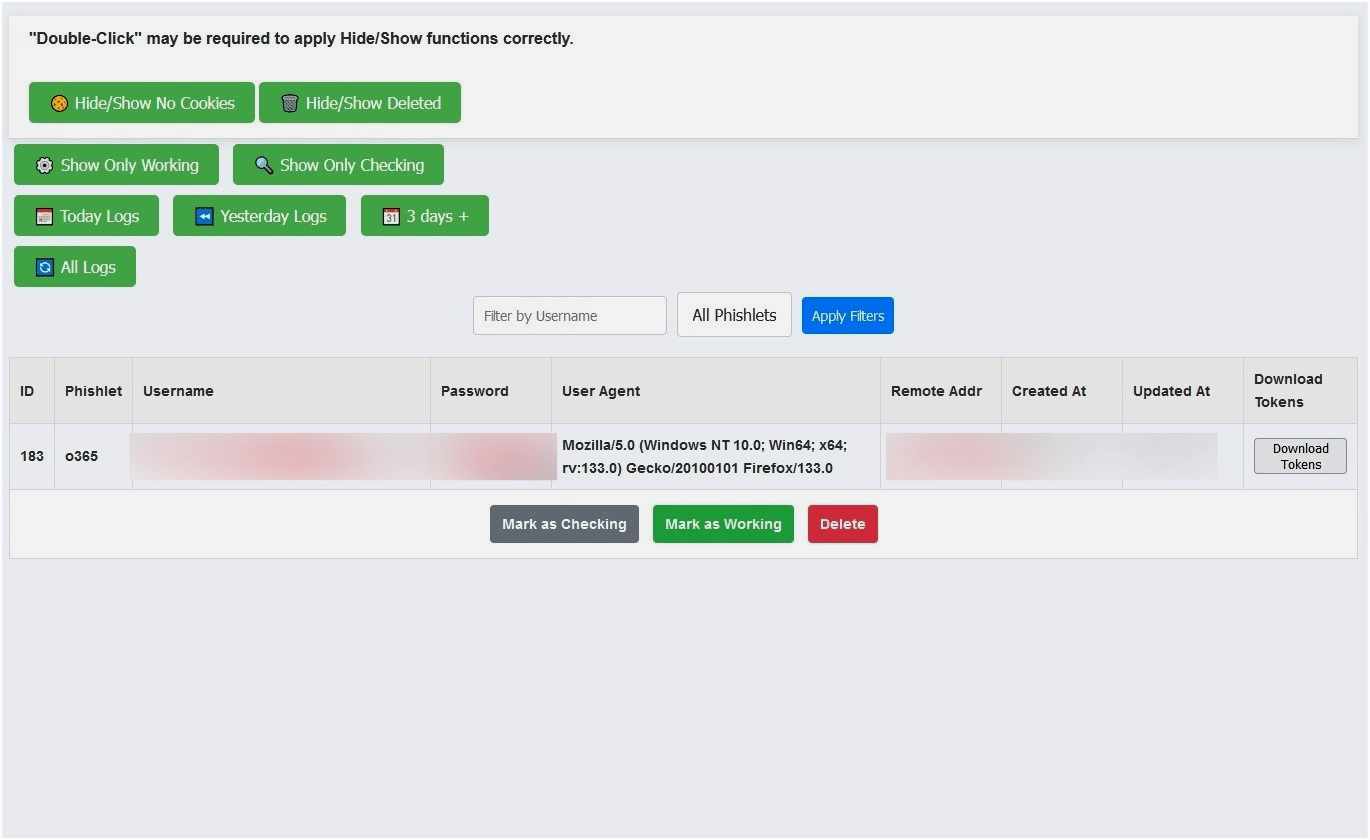
The final step involves capturing session cookies, which are issued by the legitimate server after successful authentication. Astaroth intercepts and delivers them to the attacker, who can inject them into their browser using manual header modifications or tools like Burp Suite. This bypasses 2FA entirely – no further credentials are needed, as the session is already authenticated.
Beyond its primary interception methods, Astaroth includes extra functionalities aimed at improving its durability and attractiveness to threat actors. The next section dives deeper into these features and how they fit into the larger phishing ecosystem.
Key Features
Some of its other key features include custom hosting options, like bulletproof hosting, which help it resist takedown attempts by law enforcement and ensure the long-term availability of its infrastructure. This allows cybercriminals to host their operations in jurisdictions with limited cooperation from Western authorities.
For $2,000, users receive six months of continuous updates, gaining access to the latest improvements and bypass techniques. To build trust, Astaroth offers testing before purchase, showcasing its legitimacy on cybercrime marketplaces.
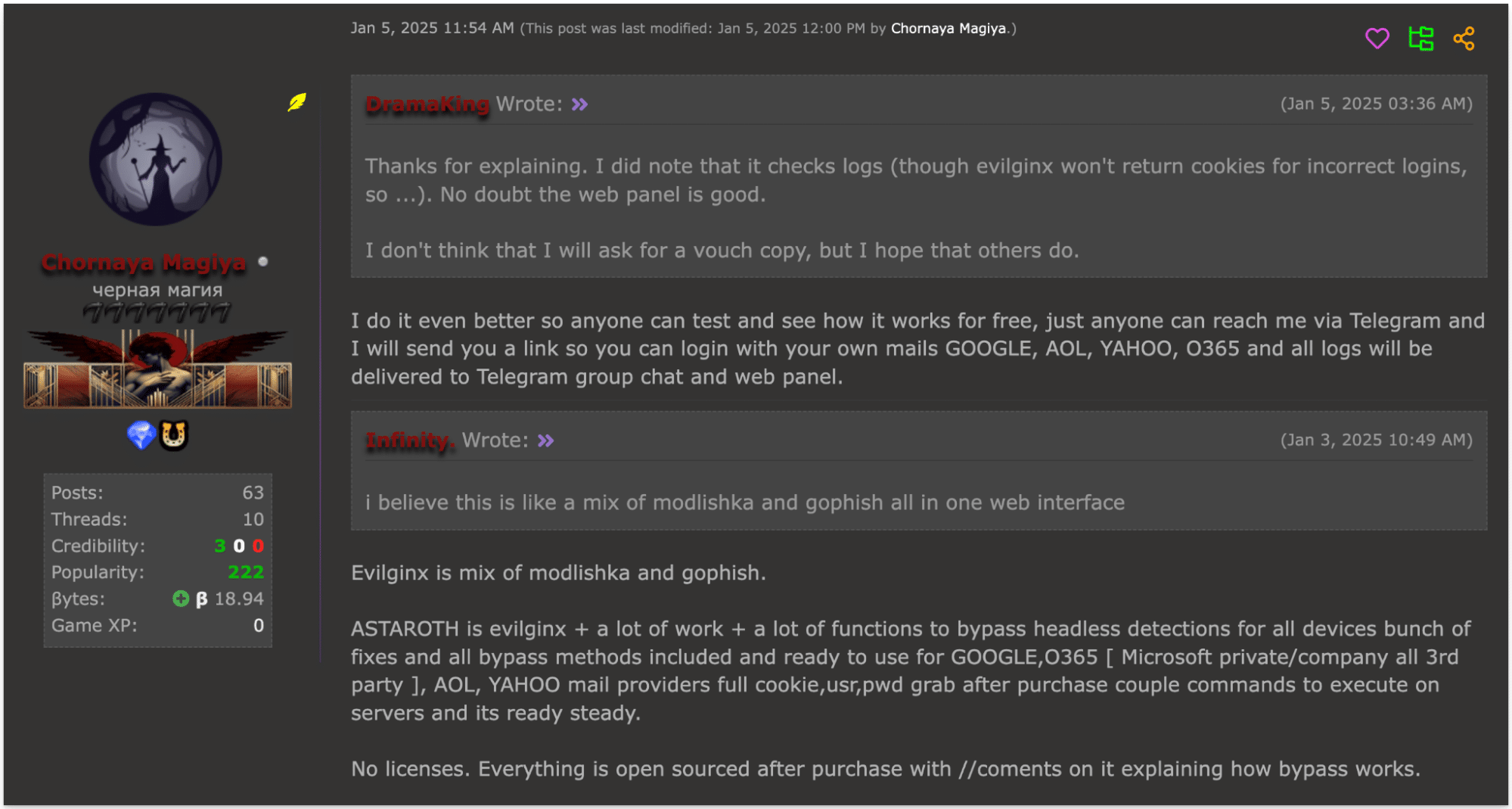
The seller is notably transparent, openly sharing details on how the phishing kit works, including techniques for bypassing reCAPTCHA and BotGuard protections. This level of openness is designed to attract both experienced attackers and newcomers by addressing common problems with manual phishing setups.
Finally, Astaroth is primarily distributed through Telegram and promoted across cybercrime forums and marketplaces. Unfortunately, the accessibility of these platforms, combined with the anonymity they offer, makes it quite difficult for law enforcement to track and disrupt its sales.
Get Protection With SlashNext
SlashNext can assist in defending against a variety of phishing kits, including Astaroth. SlashNext Complete™ is a comprehensive cloud messaging security platform that provides 99.99% accurate real-time threat detection for web, mobile, and email messaging apps.
Through the protection of email, browsers, and mobile communications, SlashNext shields businesses against financial fraud and data theft. Our cutting-edge approach protects against new phishing threats, including those that employ complex tactics. Get started with SlashNext Complete™ today.


