The latest wave of DocuSign attacks has taken a concerning turn, specifically targeting businesses that regularly interact with state, municipal, and licensing authorities. Since November 8 through November 14, we have observed a 98% increase in the use of DocuSign phishing URLs compared to all of September and October. In the last few days, our threat researchers are seeing hundreds of instances each day, many of which involve government impersonations. What’s more, the specific tactics employed in these attacks are evolving on a daily basis. Contact us for more information about DocuSign attack metrics.
This sophisticated campaign is particularly dangerous because it exploits the trusted relationship between businesses and their regulatory bodies. We’re seeing impersonations of various groups like the Department of Health and Human Services, the Maryland Department of Transportation, the State of North Carolina’s Electronic Vendor portal, the City of Milwaukee, the City of Charlotte, the City of Houston, and the North Carolina Licensing Board for General Contractors.
The Anatomy of a State-Focused DocuSign Impersonation Attack
A typical attack scenario unfolds when a general contractor receives what appears to be an official DocuSign request from their state licensing board. The request appears authentic because attackers create these templates using legitimate DocuSign accounts and APIs.
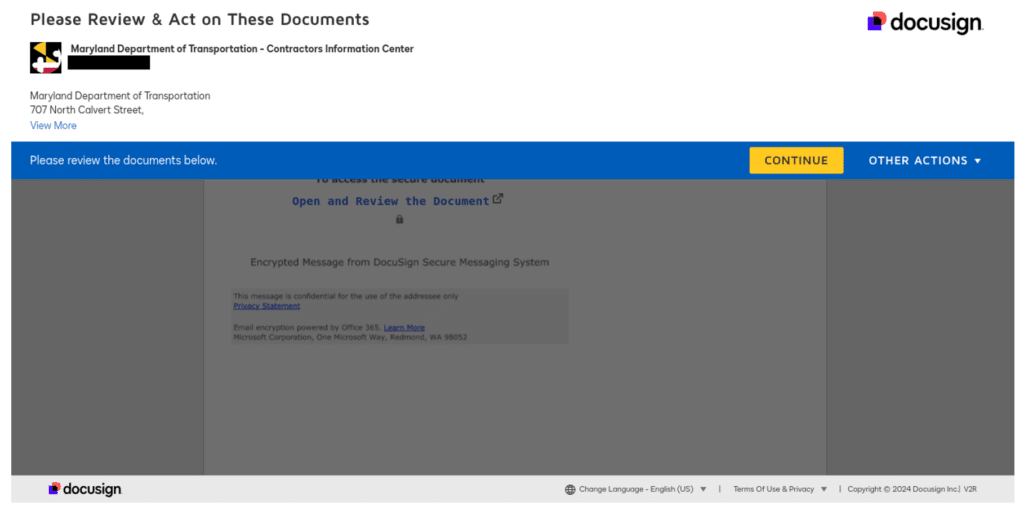
Maryland Department of Transportation DocuSign Impersonation
How Does This Work? Impact Examples
Let’s walk through a few hypothetical scenarios on how this might work in practice if SlashNext wasn’t already blocking these for customers. Click here to see real scenarios and a SlashNext demo. Below are two hypothetical scenarios of how this attack strategy could be used in the real world.
Municipal Construction Project Scenario
In Milwaukee a general contractor receives a DocuSign notification appearing to be from the City’s Department of Public Works regarding a $2.8 million renovation project for a public building. The document claims to be a change order requiring immediate signature for additional materials and labor costs of $175,000. The contractor, familiar with such change orders and eager to avoid project delays, signs the document without verifying through their usual city contact.
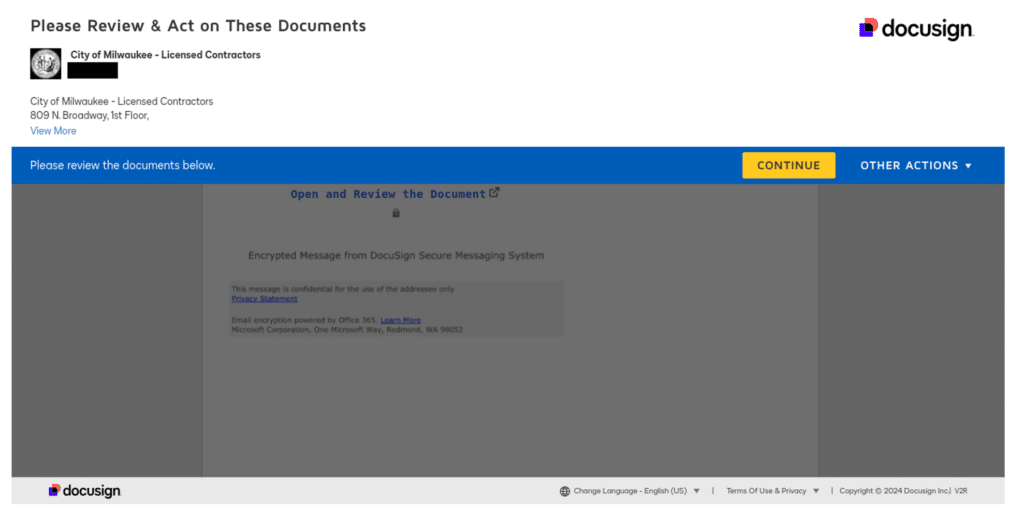
City of Milwaukee DocuSign Impersonation
State Licensing Compliance Scenario
A North Carolina commercial contractor receives an urgent DocuSign request supposedly from the NC Licensing Board. The document states their $12 million hospital construction project is at risk of immediate shutdown because of a compliance issue. The notice demands a $85,000 “emergency compliance bond” to prevent work stoppage. The time pressure and potential project impact make the contractor vulnerable to acting quickly without proper verification.
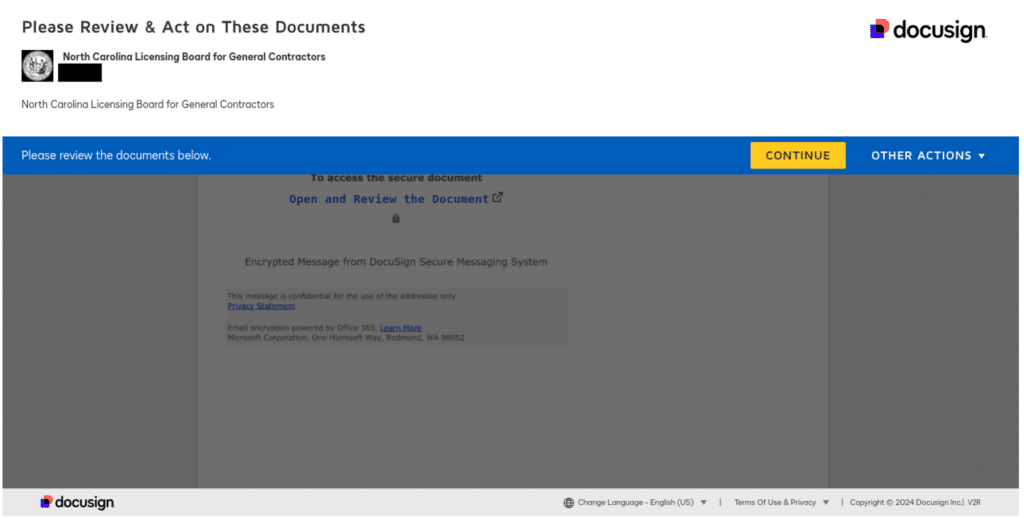
North Carolina Licensing Board for General Contractors DocuSign Impersonation
Why These Attacks Are Successful
These attacks are particularly effective because they:
- Use legitimate DocuSign infrastructure, making them appear authentic
- Target businesses during predictable licensing cycles
- Include accurate pricing and terminology familiar to the industry
- Bypass traditional email security filters since they come from actual DocuSign accounts
State Agency Impersonation Tactics
The campaign has evolved to target vendors who specifically interact with state agencies. Attackers create templates that mimic official state documentation, including:
- Licensing renewal notices
- Compliance documentation requests
- Vendor portal registration requirements
- Municipal contract modifications
The Financial Stakes
These attacks pose a dual threat for contractors and vendors – immediate financial loss and potential business disruption. When a fraudulent document is signed, it can trigger unauthorized payments while simultaneously creating confusion about actual licensing status. This uncertainty can lead to delays in bidding on new projects or maintaining current contracts.
Industry-Specific Warning Signs
Beyond standard phishing indicators, watch for these specific red flags:
- Unexpected timing for license renewals
- Unusual payment routing instructions
- Requests for immediate action on state contracts
- Documentation requirements outside normal renewal periods
The sophistication of these attacks, combined with their focus on state-level interactions, makes them particularly dangerous for businesses that regularly engage with government agencies. Understanding these specific threats and implementing proper verification procedures is crucial for protecting your business operations and maintaining regulatory compliance.
Defeat Phishing With SlashNext
SlashNext provides a comprehensive solution to address the growing threat of DocuSign cloud service abuse and multichannel phishing. SlashNext Complete™, an integrated cloud messaging security platform, detects threats in real time across email, mobile, and web messaging apps with 99.99% accuracy.
SlashNext protects organizations from data breaches and financial fraud by offering integrated cloud messaging security for email, browser, and mobile. Our approach helps defend against the most recent phishing tactics, including those that use advanced techniques.
Protect your organization with SlashNext. Learn about SlashNext Complete™.