SlashNext Incident Response
for Cortex XSOAR
Scalable, cloud-based analysis engine – purpose-built for analyzing suspicious URLs for phishing and social engineering attacks.
Featured PLAYBOOK
Automation Rising 2020 Hackathon Security Playbook Winner
Fully automate the process of reviewing emails sent by customers and the public to your brand abuse inbox. Detects brand impersonators and malicious URLs using deep inspection of website content and packages everything required to request a take-down to forward to the domain registrar.

Get Started with SlashNext and Cortex XSOAR
Online Brand Protection Detect and Respond Playbook
Fully automates the process of reviewing the emails sent by customers and the public to online brand abuse inboxes. It detects brand impersonators and malicious URLs using deep inspection of website content and packages everything required to request a take-down (IOCs, forensics, and screenshots) into an email sent to the abuse department to simply forward to the domain registrar.

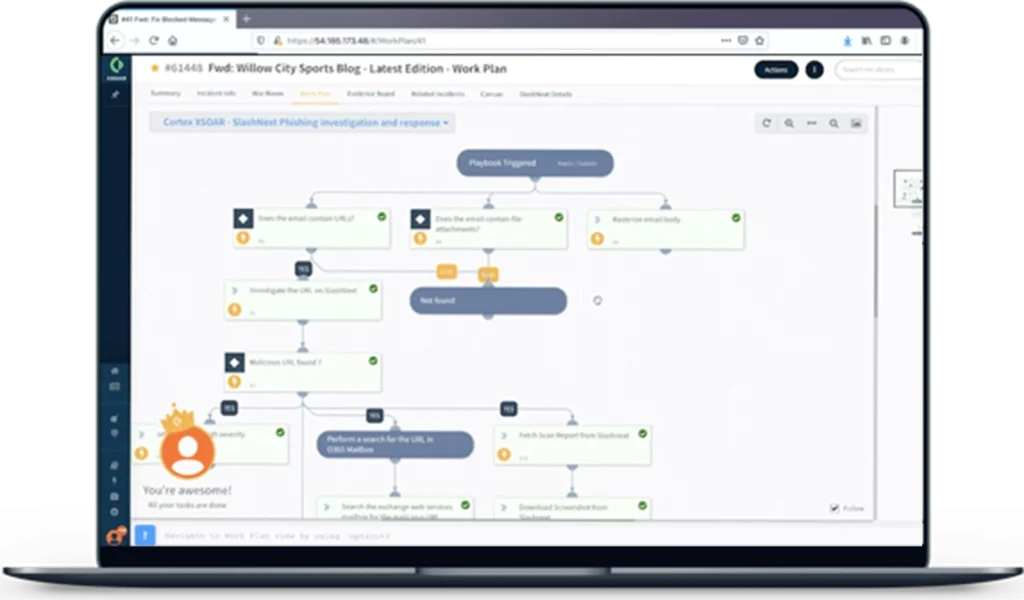
Abuse Inbox Management and Phishing IR
Effectively identify and remediate phishing threats and compromised machines faster with real-time threat intelligence on phishing URLs and C2s with SlashNext Agentless Phishing Intelligence and URL Analysis and Enrichment services using Cortex XSOAR threat hunting playbooks.
Phishing and C2 Threat Hunting
Effectively identify and remediate phishing threats and compromised machines faster with real-time threat intelligence on phishing URLs and C2s with SlashNext Agentless Phishing Intelligence and URL Analysis and Enrichment services using Cortex XSOAR threat hunting playbooks.
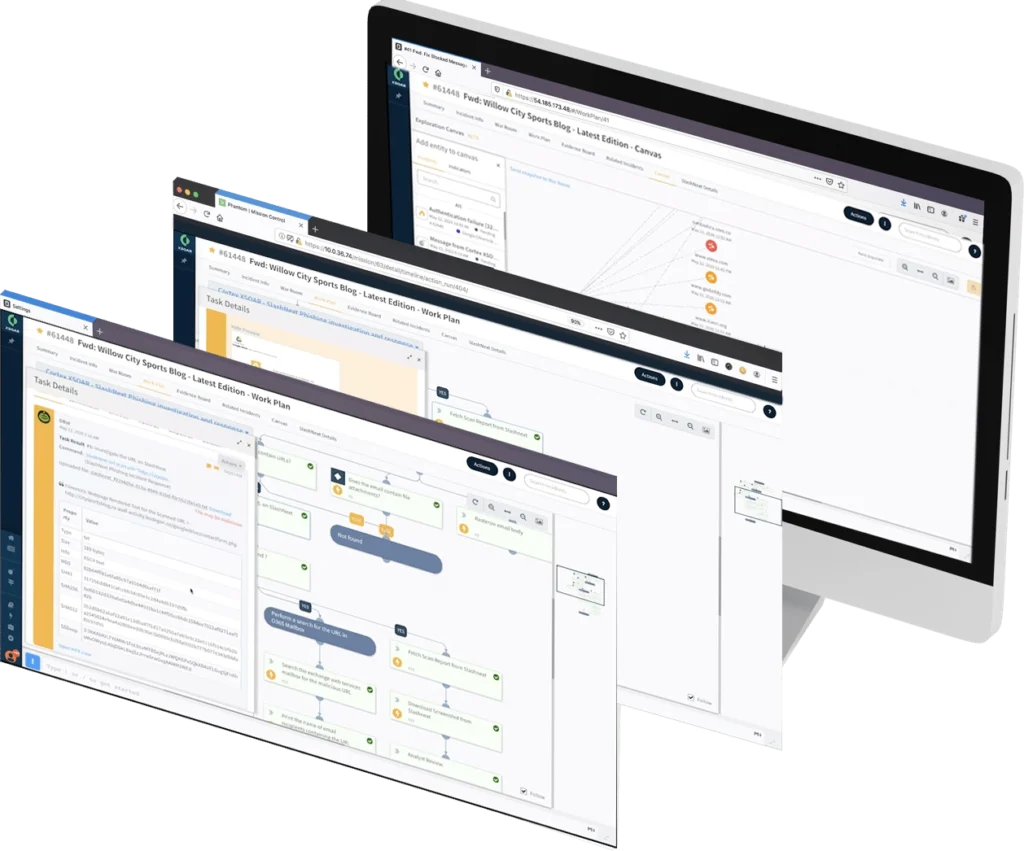
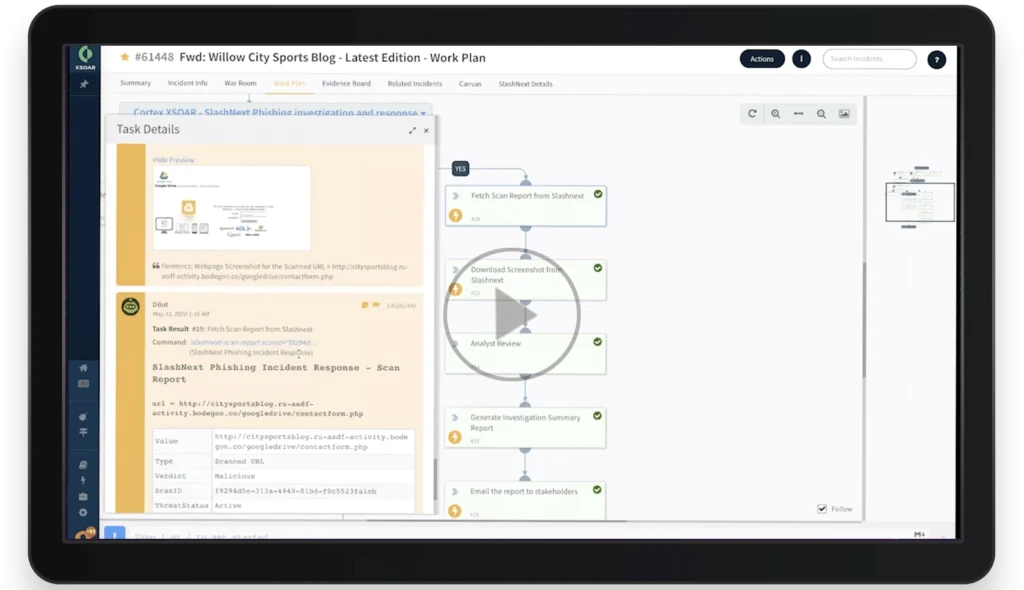
Phishing IR Integration Guide
and Video
Cortex XSOAR platform can access SlashNext URL Analysis and Enrichment to get accurate verdicts and rich IoC data, including screen shots, to expedite phishing IR and threat hunting playbooks.
Additional Resources
Get started using the following resources:
“Through this integration, Cortex XSOAR users now benefit from the enhanced protections of SlashNext’s phishing URL analysis to speed incident response, analysis, and
protection from fast-moving phishing threats.”
Rishi Bhargava, vice president of product strategy, Cortex XSOAR at Palo Alto Networks.
Featured Webinar
Automate Phishing IR with Precise On-Demand URL Analysis
Fully automate online brand abuse inboxes to detect brand impersonators & malicious URLs by using SlashNext deep inspection. Initiate take down request by automating the process of packaging the required IOCs, forensics, & screenshots.

Try RTPD APIs in Your Own Environment Risk-Free
Real-Time Phishing Defense APIs gives security teams access our scalable, cloud-based APIs for high volume real-time threat intelligence lookup, plus dynamic live scanning that leverages our patented SEER™ threat detection technology.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.


