See the Threats Bypassing Your Current Defenses
Reveal and analyze phishing threats that are evading your current defenses in your Microsoft 365 inboxes, web logs, or both:
- Reveal phishing threats evading your current email defenses
- See which users actively participated in live phishing threats with a web log analysis
Completing the complimentary secure assessment is quick and easy:
- No hardware or software to install. Simply request access to the secure SlashNext Cloud Manager to begin the assessment
- Available for Microsoft 365 using OAuth 2.0 to authorize the scan of inboxes (admin access required)
- Receive a personalized risk assessment report
- Request a meeting with a security expert to review the results
- Easily deploy protection to target users
Start Your Phishing Risk Assessment Today
Please note, admin access is required to complete the OAuth 2.0 Authorization

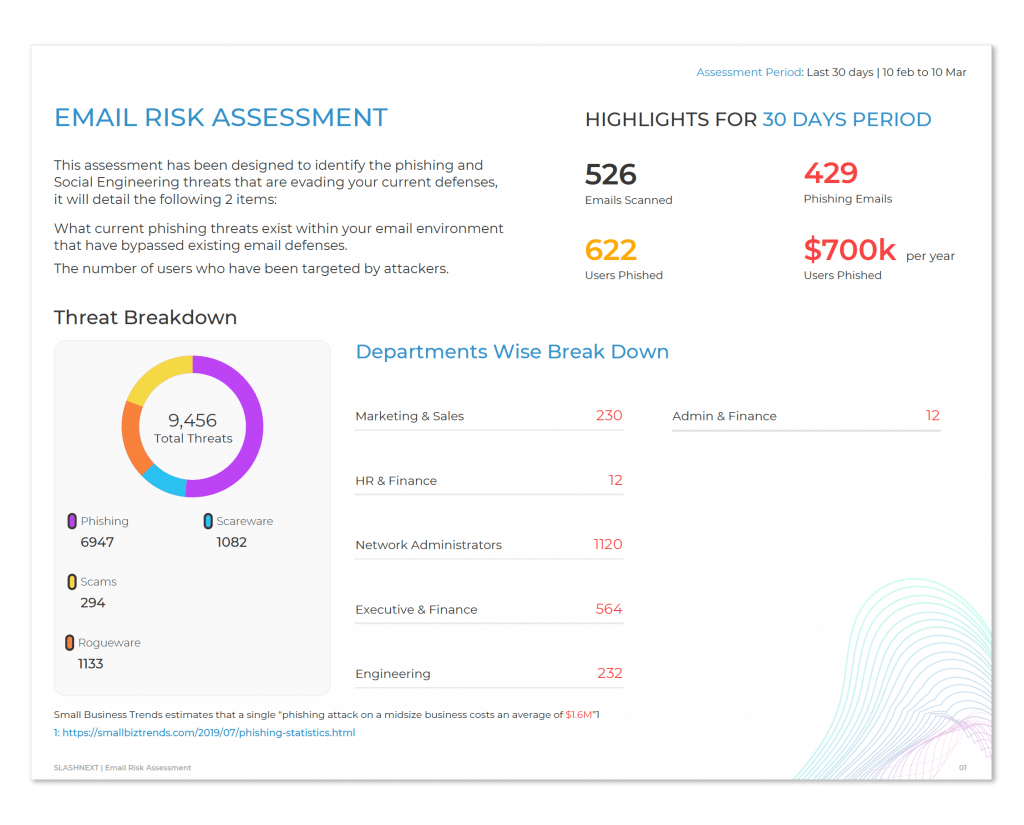
The Top Phishing Threats Getting Through Current Defenses
Phishing attacks found in recent risk assessments clicked on by business users could lead to $2.4M in costs and damages.
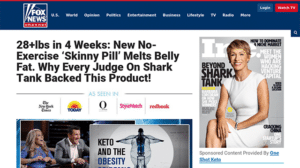
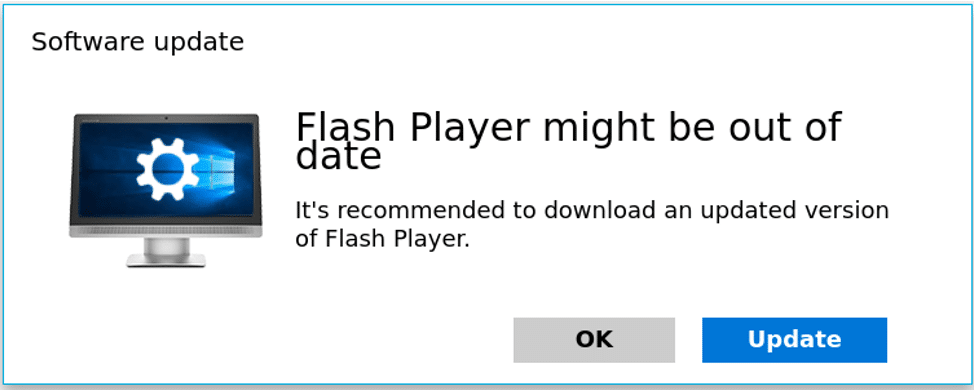
Credential
Stealing
70% of phishing attacks lead to account takeovers. Popular types of credential stealing are spoofed pages for brands like Google, Microsoft, and Dropbox.
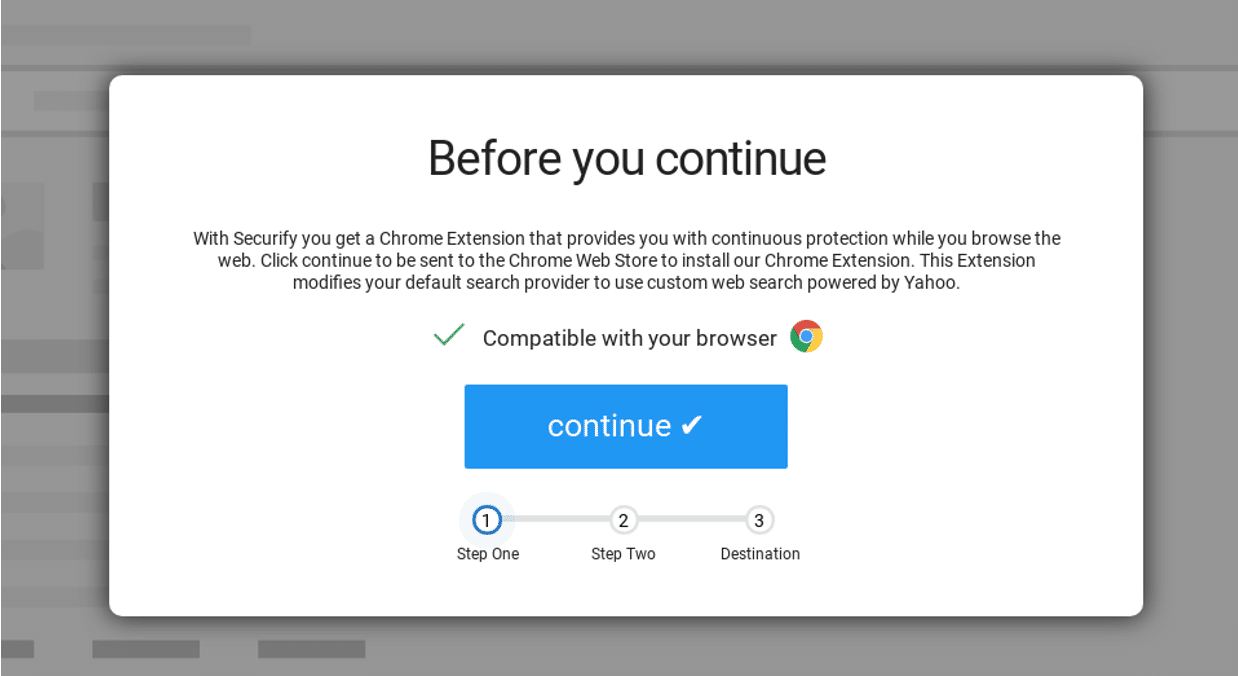
Rogue Browser Extension
Rogue browser extensions can permit malware onto an employee’s system for data exfiltration up to $2.4M in costs and damages.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.