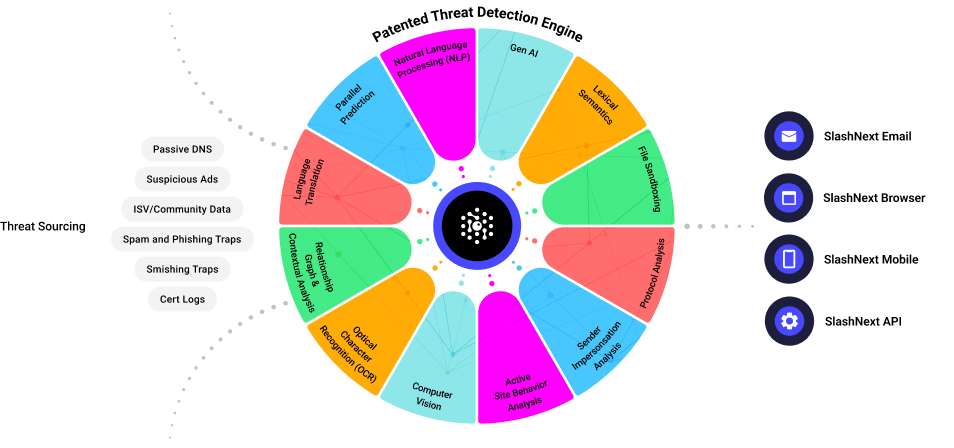
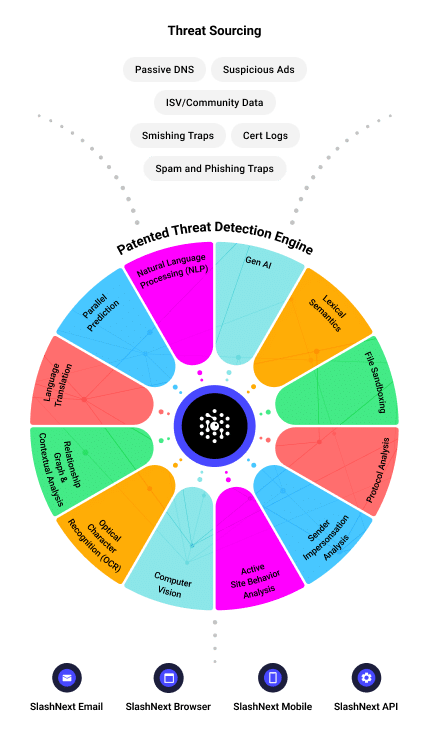
Patented Next Gen AI Technology
Integrated cloud security platform leveraging a combination of relationship graph, contextual analysis, computer vision, natural language processing, and generative AI to detect threats in real-time with 99.9% accuracy.
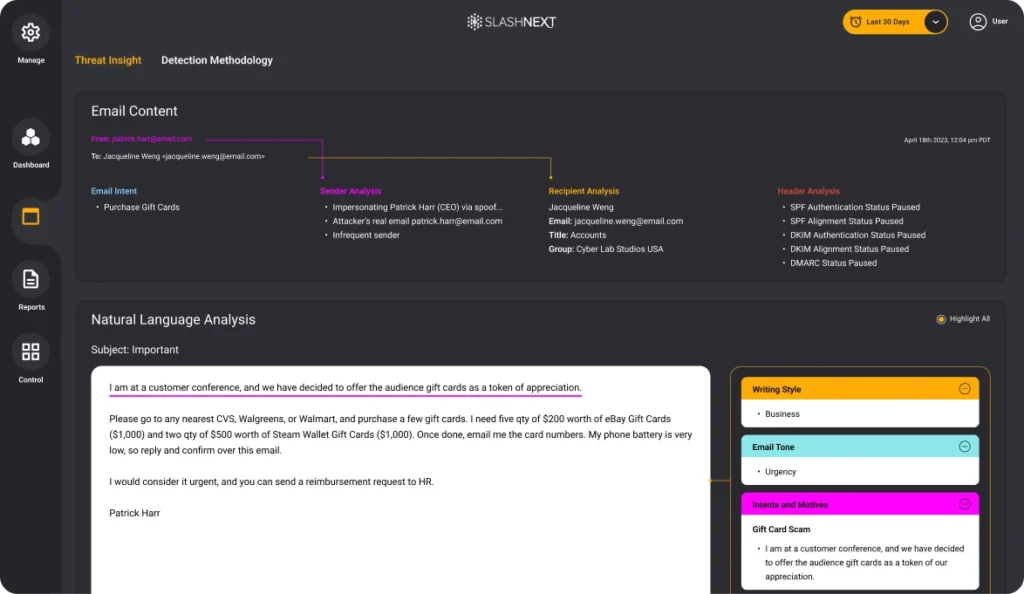
Next Gen AI Message Security Technology
SlashNext utilizes its patented AI threat detection technology to protect users from the widest range of linked-based attacks, attachment-based attacks, and natural language payloads.
Stop The Attacks That Impact Your Business

Social Engineering, Scams and Fraud
Deception to manipulate users into divulging information for misuse.

Trusted Services Compromise
Uses trusted domains to obfuscate cyber attacks to increase success.
Ransomware, Malware and Exploits
Intended to inject code, take-over browser canvas or download malware.

Malicious Attachments
Malicious HTML, PDF and Office files used to harvest credentials or download malware.

BEC, ATO and Supply Chain Attacks
Targets execs or financial teams to defraud a company for financial gain.

Credential Stealing
Cyber attack designed to steal passwords with the intent of accessing protected data.
Spear Phishing
Personalized targeted attack designed to trick users into a data breach or for financial gain.
Smishing and BTC
Using SMS text messages to trick users into divulging passwords or other PII for fraudulent use.
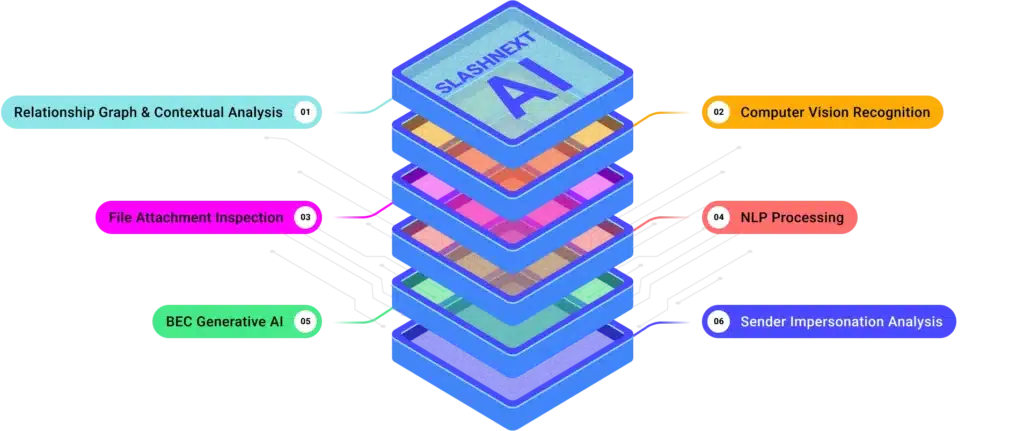
SlashNext's GenAI Threat Detection and Prediction Engine
A unique combination of techniques sees through evasion tactics and accurately detects threats, even those hosted on compromised websites and legitimate infrastructure.

AI Preemptive Threat Identification
Patented detection engine using, behavioral analysis, relationship graph, virtual browsers, and machine learning to preemptive detect unknown threats

AI LiveScan Real-Time Detection
Scan URLs and attachments with virtual browser to fully renders content and apply ML classifiers to detect threats in real time
The SlashNext Advantage is Your Advantage

Preemptive
Global, proactive threat hunting provides advance visibility, detection, and protection from emerging threats
Real-Time
Real-time, automated scanning provides more effective protection from zero-hour threats

Quick and Accurate
48 hour detection advantage with a 99.9% detection rate and 1 in 1 million false positives

Fast Deployment
Works out of the box in 5 minutes
Overcomes Evasion Tactics
Overcomes evasive techniques like Captcha & IP restrictions, URL obfuscation, and attacks using compromised websites and trusted hosting infrastructure

Multi-Channel
Protection
Protect corporate email to personal mailboxes, web and mobile threats, including, M365, Zoom, SMS, LinkedIn, WhatsApp and other messaging channels

Multi-Payload
Protection
Stop account takeover, credential harvesting, BEC, ransomware, malware, exploits, social engineering and advanced zero-hour phishing attacks.

Integrated Cloud
Security
Protection for email, mobile, web and brand protection.
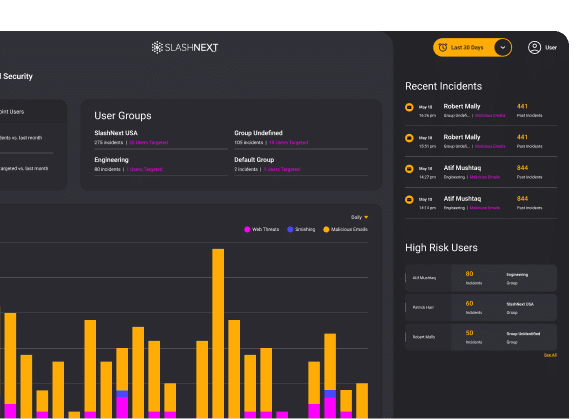
See SlashNext Complete™
in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.


