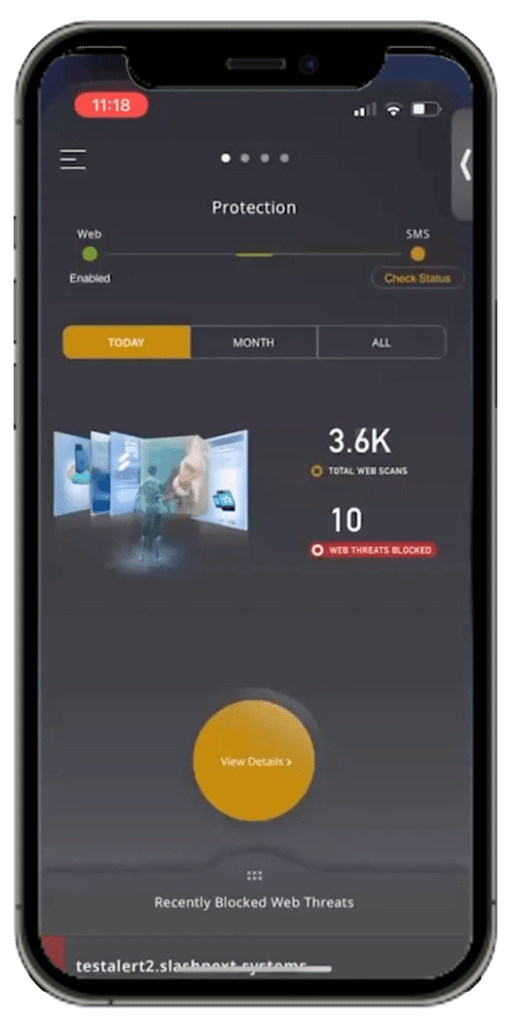
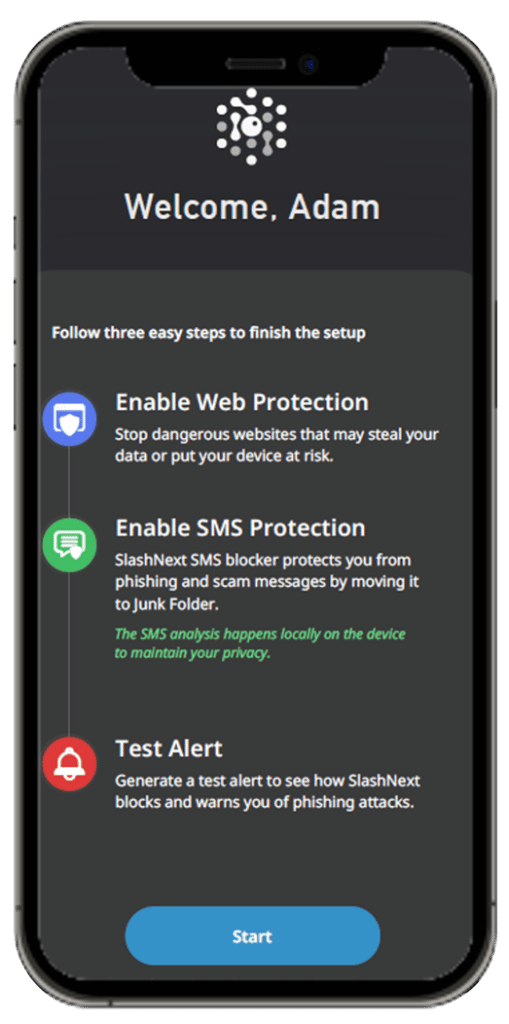
SlashNext Mobile Security
Stop smishing and business text compromise with zero-hour phishing protection against the broadest range of phishing threats in any mobile application. Available for business, personal BYOD, and home use.

Today Mobile Phishing Attacks Are On The Rise

of organizations report mobile device threats are growing more quickly than other device threats.
Verizon Mobile Security Index 2022
Mobile Security Product Portfolio
Protect iOS and Android users from Smishing and targeted phishing threats in all Apps
Centrally managed, with multiple deployment options, incidents written to CMS, and supports all device types.
Direct to consumer. Purchase on Apple Pay and Google Pay. No incidents recorded in CMS Family sharing for 5 devices.
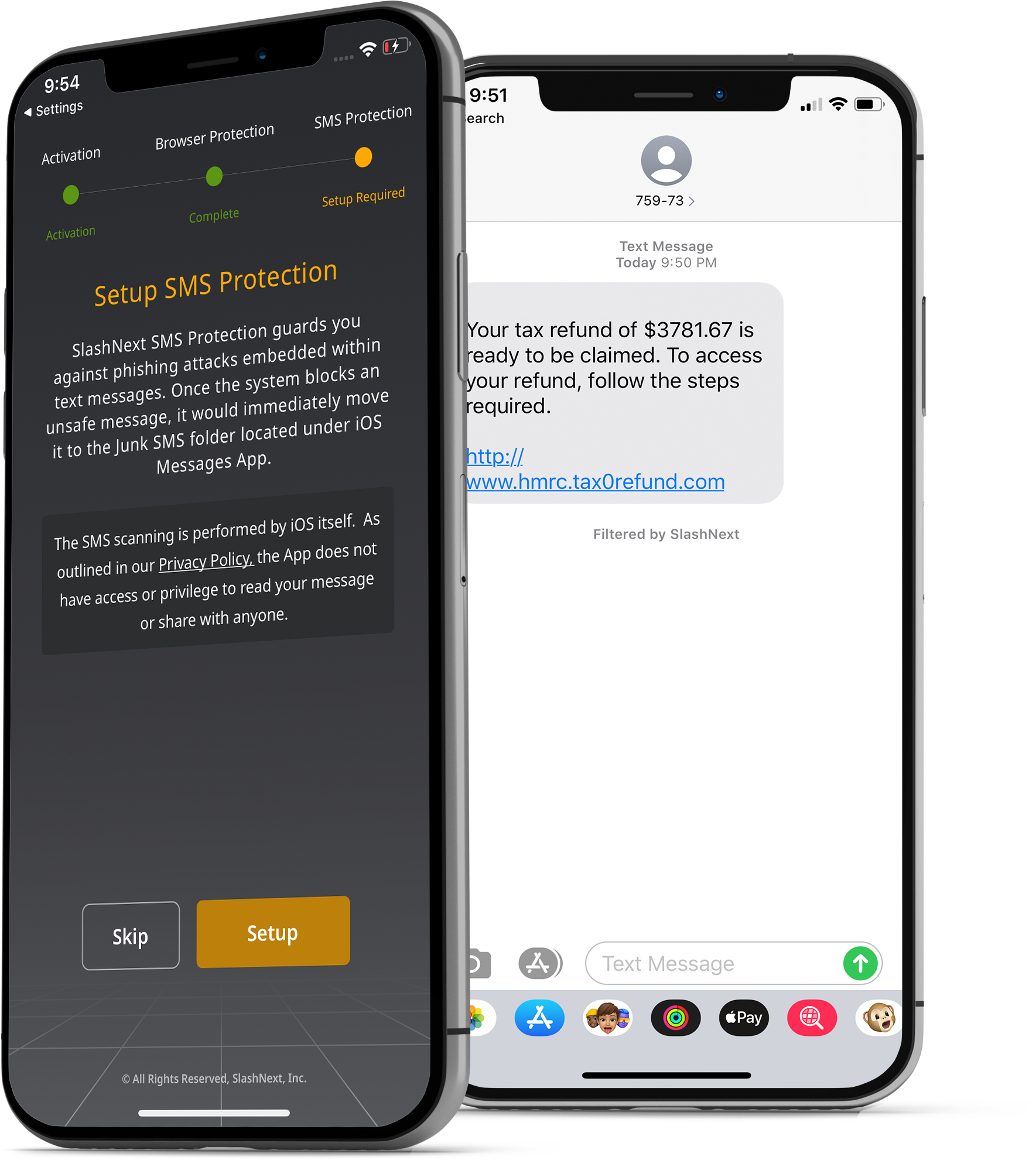
Smishing and Business Text Compromise (BTC) Protection
Smishing and BTC are a growing threat on mobile. With SlashNext, malicious SMS/text messages are accurately identified and quarantined, protecting users from taking the bait.
Enterprise-Grade User Experience
State-of-the-art protection and user experience, including:
- Safe preview of the phishing site
- Helpful threat information to educate users
- Ability to submit a support ticket about the incident
- Automated notifications and reporting
- Lightweight memory consumption and battery usage
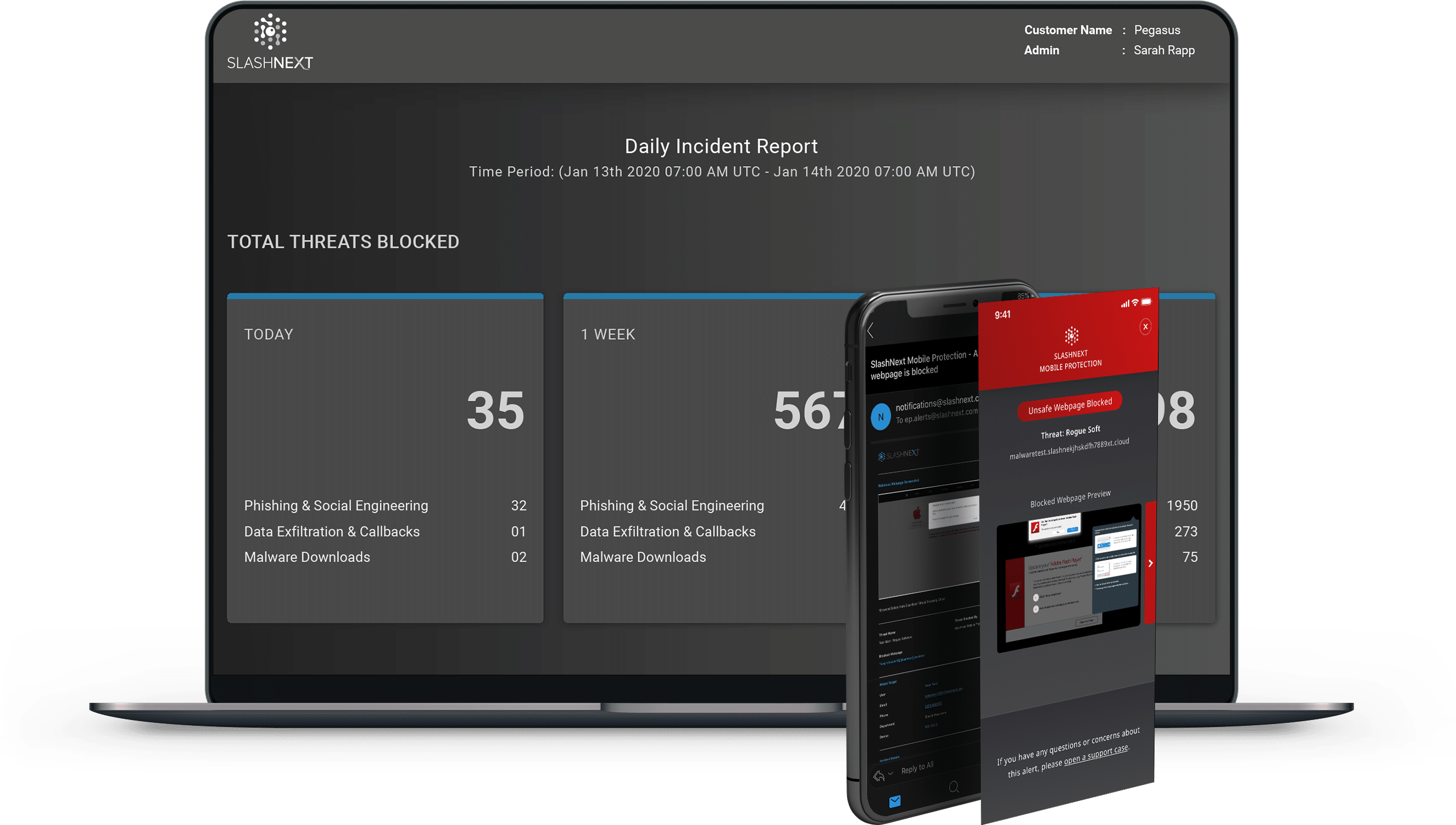
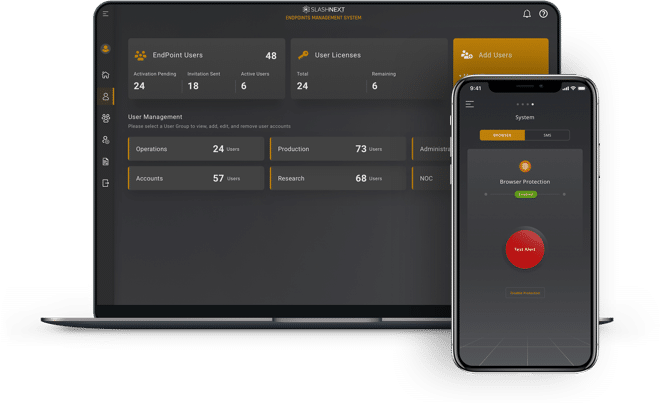
Advanced Reporting and Analytics
Easily manage groups, policies, users, and licenses. Advanced reporting and analytics features include filters to view data by threats, endpoints, and users for a full view across the enterprise.
Drill-down into high-risk users, timelines, and detailed forensics information. Automate daily or weekly reporting, including incidents and executive summaries.
Stop The Mobile Attacks That Impact Your Business
The SlashNext Multi-Channel Platform Advantage

Zero-Hour AI Detection & Extreme Accuracy
99.9% detection rate and 1 in 1 million false positives

Multi-Channel
Protection
Covers the most phishing and social engineering payloads across all channels

Great User Experience & Guaranteed Privacy
Fast real-time protection with no latency with no personal data transmitted

Fast ROI &
Time to Value
Deploy in minutes with automated updates
Close the Gaps with SlashNext Complete™
Multi-channel phishing protection platform for users across email, web, mobile and API. Stop 65% more spear phishing, legitimate service compromise, BEC, rouguewqre, SMiShing, social engineering and other human compromise attacks in Microsoft 365, Teams, Zoom, Box, SMS, LinkedIn, WhatsApp and other messaging channels.
Experience SlashNext Protection in Action
Request a free trial to see how SlashNext detects zero-hour threats in real-time and stop the attacks that impact your business.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.