Stop Rising EDU Cybercrime in the Era of Gen AI
Explore the challenges of protecting educational institutions from swiftly advancing phishing threats and learn how generative AI is stopping BEC, payment scams, spear phishing, and other social engineering attacks.
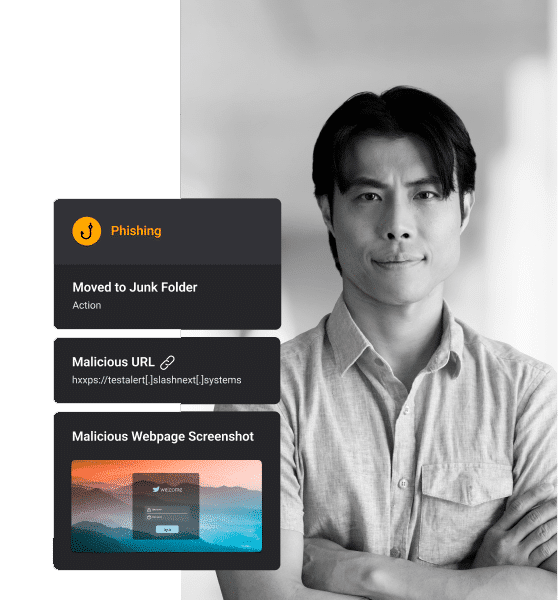
There is a serious concern in the EDU community about the increase in email cyber threats targeting faculty, staff, alums, and students that could lead to a breach, resulting in financial loss and the loss of critical sensitive data.
Combine increases in attacks with complacency within the user community, and security teams need to have a layered security approach to prevent malicious emails from reaching users in the first place.
Educational institutions, particularly university and college campuses, are a favorite target for cybercriminals to test out the latest threats because higher education has large distracted populations, research facilities, many vendors, and multiple invoices circulating through their email. Business email compromise, QR code phishing (Quishing), and other sophisticated social engineering threats are increasing rapidly.
Watch the video to learn about the challenges of protecting a large university and how to use generative AI to stop BEC, payment scams, spear phishing, and other social engineering attacks.
Hear from Education and Security Experts

Douglas Lomsdalen,
ISO, California Polytechnic State University

Higher Ed Embraces Generative AI for Cloud Email+ Security
There is a million-dollar business impact when a breach occurs from these attacks. Harnessing the power of GenAI to stop phishing is on the minds of all security professionals.

Hackers Are More Effective at BEC
The diversity and sophistication of BEC types have received a significant boost from the public availability of generative AI chatbots.
Growth of Mobile Phishing
Mobile phishing is on the rise as it’s also the most unprotected of all communication channels and most threats on mobile start with SMS text. Threats are customized for mobile delivery but use familiar credential stealing, malware, and exploit tactics.
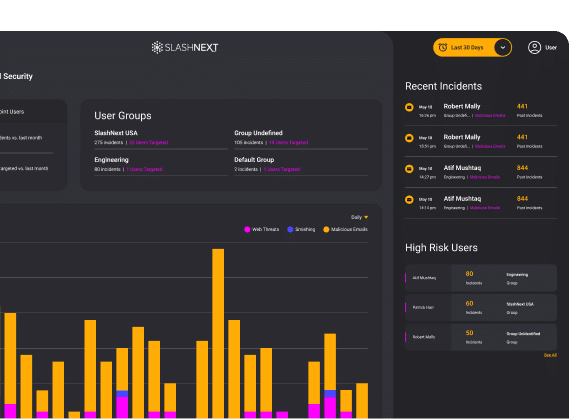
See SlashNext Complete™
in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.


