Why Chose SlashNext Over Proofpoint


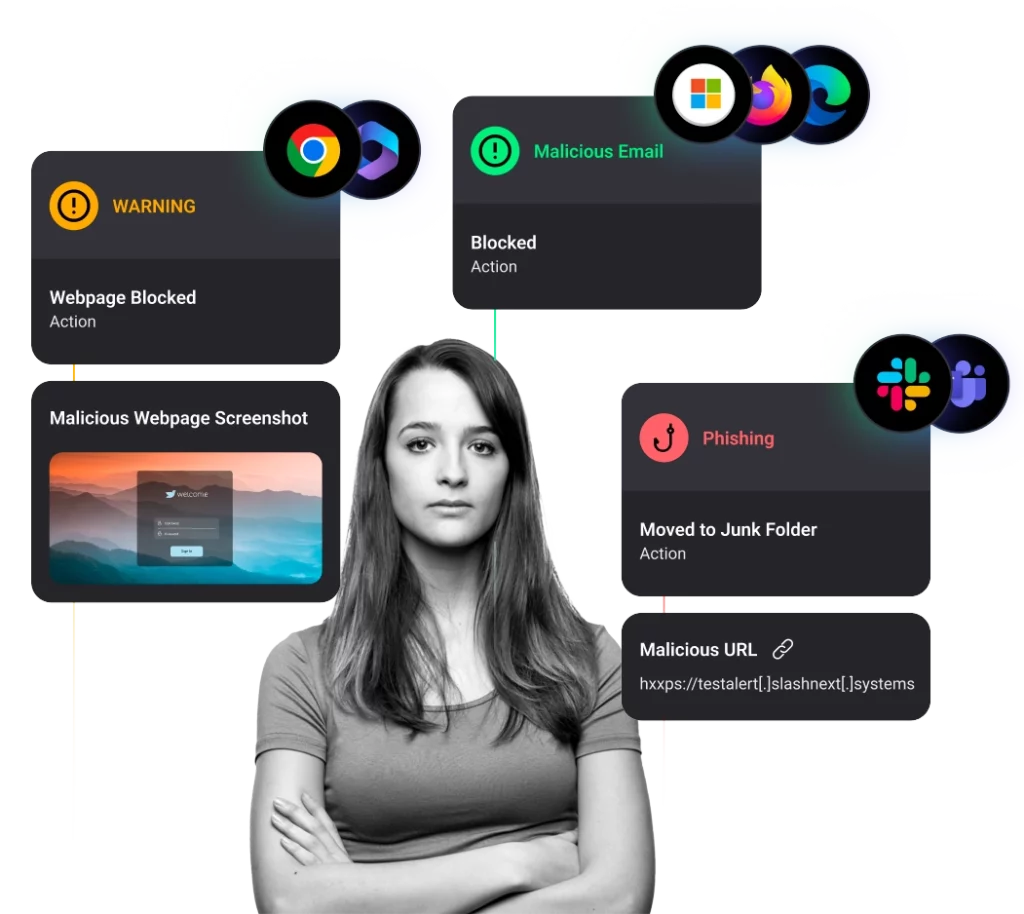
Proofpoint’s Security Email Gateway (SEG) technology solves half of the problem
Proofpoint effectively detects and remediates malicious emails, but its limited multi-channel offering does not address how people work today.
SEGs began as a powerful solution to stop malicious emails from arriving in users’ mailboxes.
However, SEGs legacy technology has limitations:
- SEGs prevent the implementation of a full defense-in-depth strategy. SEGs use domain reputation, URL rewriting, and static block lists, which aren’t enough to offer the real-time protection needed to keep users safe
- SEGs require disabling the built-in protections from the email service provider
- SEGs are not seeing internal traffic. While SEGs receive all of the inbound and outbound emails, they do not see internal emails, so they cannot identify compromised account takeovers.
SlashNext is uniquely qualified to achieve complete defense-in-depth security
SlashNext’s HumanAI technology, unique from other ICES solutions, offers powerful layers of protection.
- Relationship Graph and Contextual Analysis
- Generative AI for Advanced BEC Protection
- File Attachment Inspection
- Computer Vision, Natural Language Processing, and Sender Impersonation Analysis
With the real-time detection of Live Scan, plus mobile and browser protection, SlashNext blocks phishing threats missed by Microsoft 365, SEG, and ATPs technologies for true zero-hour phishing protection.
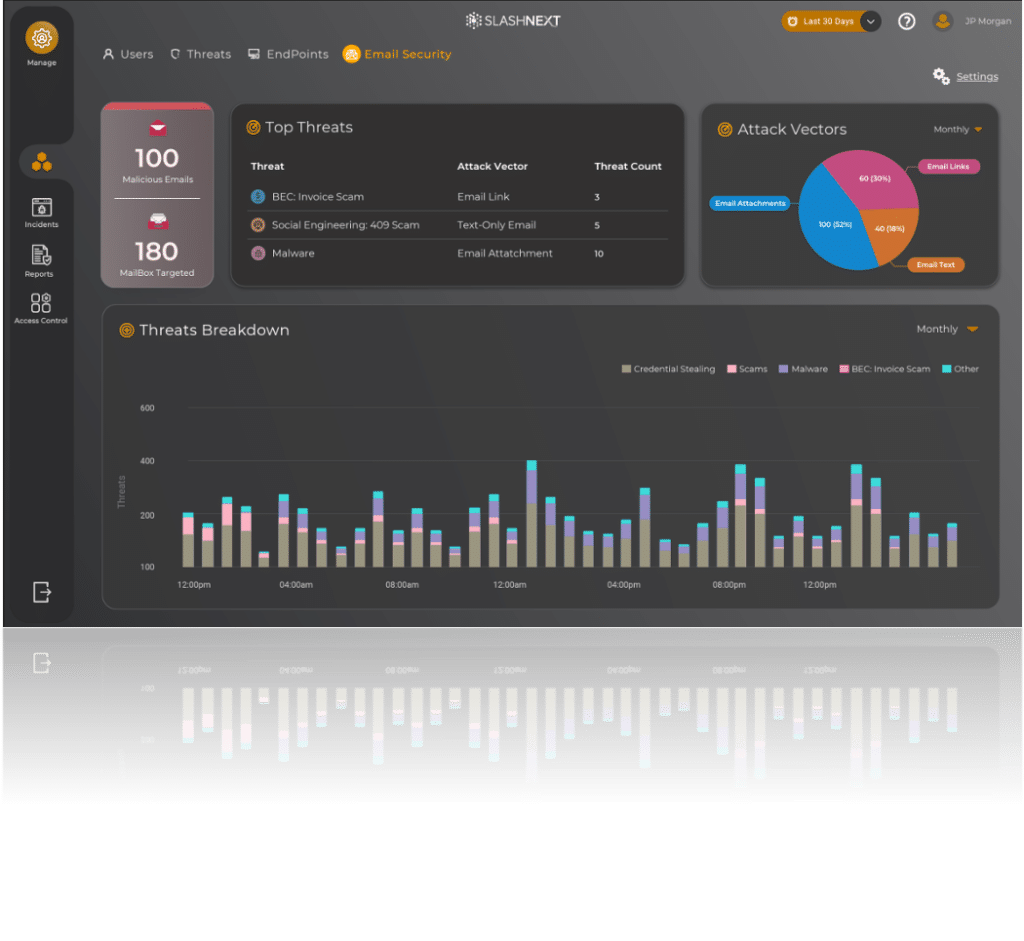
See How SlashNext Stacks Up Against the Competition
| FEATURE | SLASHNEXT | PROOFPOINT |
|---|---|---|
| Zero-hour BEC and ATO Protection Relationship graph, natural language processing of email body, header analysis, contextualization, and behavioral AI. |  |  |
| Generative AI for BEC and BMC Clones and synthetically generates BEC/BMC threat iterations to train models and continuously predict the next threats. |  |  |
| Relationship Graph and Contextual Analysis Baselines communication patterns in your environment to identify relationship patterns and anomalies. |  |  |
| Zero-Hour Link Protection Use pre-emotive sourcing and real-time scans by combining computer vision, NLP, and behavioral AI to identify malicious links. |  |  |
| Zero-Hour File Protection Use pre-emotive sourcing and real-time to identify malicious file payloads, including for HTML, doc, pdf, and zip. |  |  |
| Smishing Protection Accurately identifies and quarantines malicious SMS/text messages. |  |  |
| Multi-Channel Protection Stops zero-hour threats in email, mobile, and web messaging apps across M365, Gmail, LinkedIn, WhatsApp, Telegram, Slack, Teams, and other messaging apps. |  |  |
| Operational Security Controls Implement by group, country, and organization, configurable in the admin portal. |  |  |
See How SlashNext Stacks Up Against the Competition
| FEATURE | SLASHNEXT | PROOFPOINT |
|---|---|---|
| Zero-hour BEC and ATO Protection |  |  |
| Generative AI for BEC and BMC |  |  |
| Relationship Graph and Contextual Analysis |  |  |
| Zero-Hour Link Protection |  |  |
| Zero-Hour File Protection |  |  |
| Smishing Protection |  |  |
| Multi-Channel Protection |  |  |
| Operational Security Controls |  |  |
Trusted By Our Customers
8M Mailboxes, Devices and APIs Protected





Industry Recognition
Compare SlashNext with your current email security solution
- Set up in minutes without impacting your existing email infrastructure or mail flow
- Full visibility and immediate transparency of threats identified in your environment
- Get personalized insights into how we do it
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.







