Advanced URL Inspection & Analysis
Our sophisticated URL analysis technology provides real-time protection against the most deceptive phishing attacks hiding in your email.
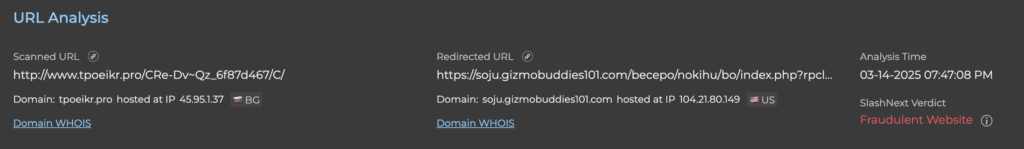
URL Analysis
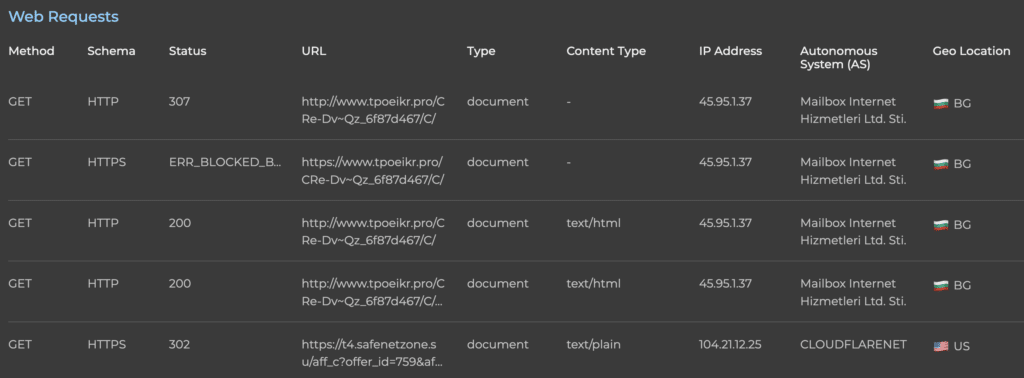
Unlike traditional security measures that do signature matching with third party intelligence feeds, our solution does deep URL inspection to reveal the details behind the malicious content even that content hosted on legitimate services.
Exposing Hidden Threats in Trusted Platforms
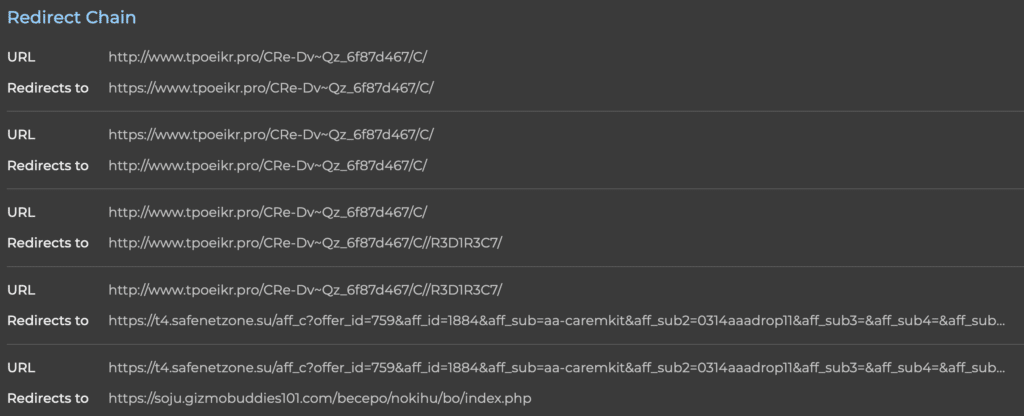
- Following complete redirect chains from initial links to final destinations
- Capturing visual snapshots at key points in the journey
- Analyzing certificate details for suspicious patterns
- Detecting obfuscation techniques including nested links and QR codes
The Complete Picture Advantage
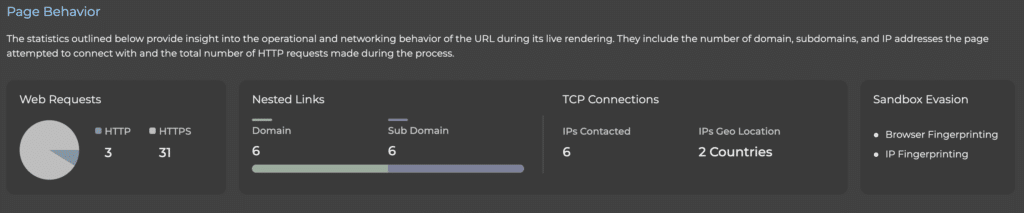
- Real-Time Request Tracking: We document every web request along the journey, including methods, status codes, and content types to reveal the complete attack path.
- Visual Intelligence:
Our AI-powered computer vision captures and analyzes screenshots, identifying brand impersonations and suspicious page elements that traditional scanning misses.
- Certificate Analysis: We examine security certificate details to identify recently registered or suspicious domains that might indicate malicious intent.
- Layered Defense: By combining advanced natural language processing with visual analysis, we identify subtle red flags in both text and design elements that signal deception.
The SlashNext Advantage is Your Advantage
Preemptive
Global, proactive threat hunting provides advance visibility, detection, and protection from emerging threats
Real-Time
Real-time, automated detection provides more effective protection from zero-hour threats
Extreme Accuracy
Near-zero false positives results in immediately actionable, block-ready threat intelligence
Overcomes Evasion Tactics
Detects threats missed by URL inspection and domain reputation analysis methods
Multi-Vector, Multi-Payload
Covers more types of phishing and social engineering payloads across all phishing attack vectors, not just email
Deployment Flexibility
Deploy to mobile, endpoints, and existing tools and infrastructure
Related SlashNext Products
SlashNext Integrated Mobile Messaging Security
Protect iOS and Android users from mobile-centric phishing threats with a lightweight, cloud-powered agent.

SlashNext Integrated Browser Messaging Security
Shield employees from live phishing sites with cloud-powered browser extensions for all major desktop browsers.
See SlashNext Complete™ for Email, Mobile and Browser in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.


