As a global infrastructure advisory firm, Moffatt & Nichol provides engineering and consulting services to clients in the marine terminal, transportation, energy, environmental, federal, and urban development markets around the world.
At Moffatt & Nichol, threat actors were using Business Email Compromise (BEC) to initiate vendor impersonation and invoice fraud against the company through a multi-stage attack. Lookalike domains were used and emails were coming from free Gmail accounts to evade IP reputation detection. The company was vulnerable to attacks launched using Google, Adobe, Dropbox, and other widely used trusted domains. The bad actors first “instructed” a company user to provide a mobile number for the next stage of an attack. Then, the bad actors requested wire payments to the attacker’s account.
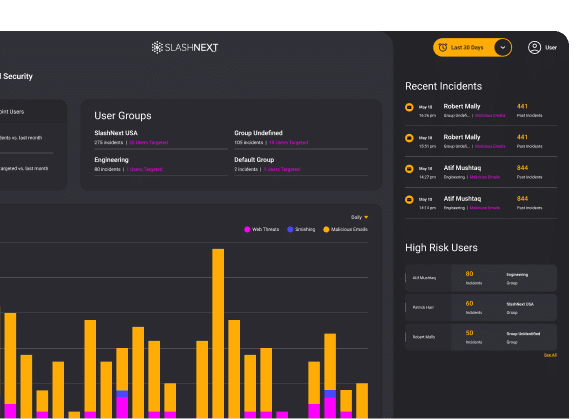
Moffatt & Nichol implemented SlashNext’s Cloud Email Security, plus protection for SMS, Slack, Zoom, Teams, Gmail, and other messaging apps for AI-powered platform combining natural language processing, computer vision, and machine learning with relationship graphs, generative AI, and deep contextualization immediately detected 92% more multi-stage BEC and natural language attacks in the first 30 days after deployment.
SlashNext Email+ Security immediately detected 92% more multi-stage BEC and natural language attacks in the first 30 days after deployment. The types of attacks included BEC impersonation, invoice fraud, payroll theft, and others, in addition to social engineering threats associated with purchase renewals, beneficiary information, donations, investments, and loans. SlashNext found a significantly high number of users targeted with threats that included executive impersonation, payroll theft, and invoice fraud.