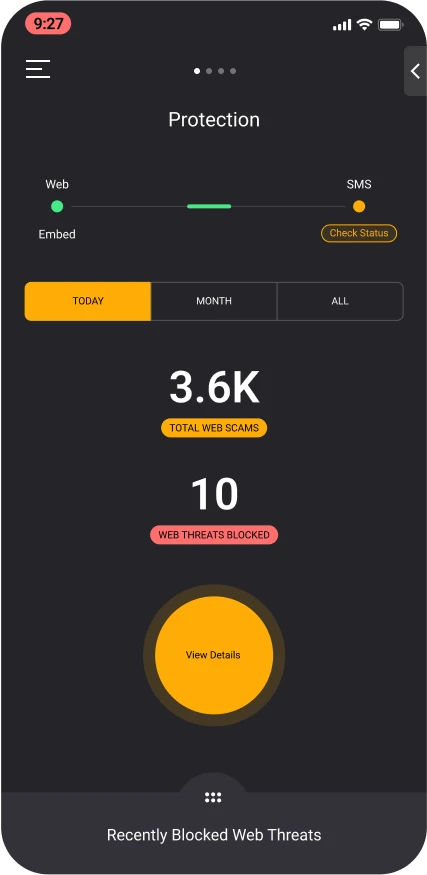
Protection for SMS and Mobile Apps
Stop smishing and business text compromise with zero-hour phishing protection against the broadest range of phishing threats in any mobile application. Available for business, personal BYOD, and home use.
Today Mobile Phishing Attacks Are On The Rise

Mobile Threats
83% of organizations report mobile threats are growing more quickly than other device threats and lead to successful breaches.

Smishing Targets
43% of employees have been the target of a work-related attack on their personal device.
Data Breach Cost
The average global cost of a data breach is $4 million with losses exceeding $10.3 billion annually.
Mobile Security Apps
Protect iOS and Android users from Smishing and targeted phishing threats in all Apps
Centrally managed, with multiple deployment options, incidents written to CMS, and supports all device types.
Direct to consumer. Purchase on Apple Pay and Google Pay. No incidents recorded in CMS Family sharing for 5 devices.
How SlashNext Stops the Widest Range of Attacks from Entering Your Organization
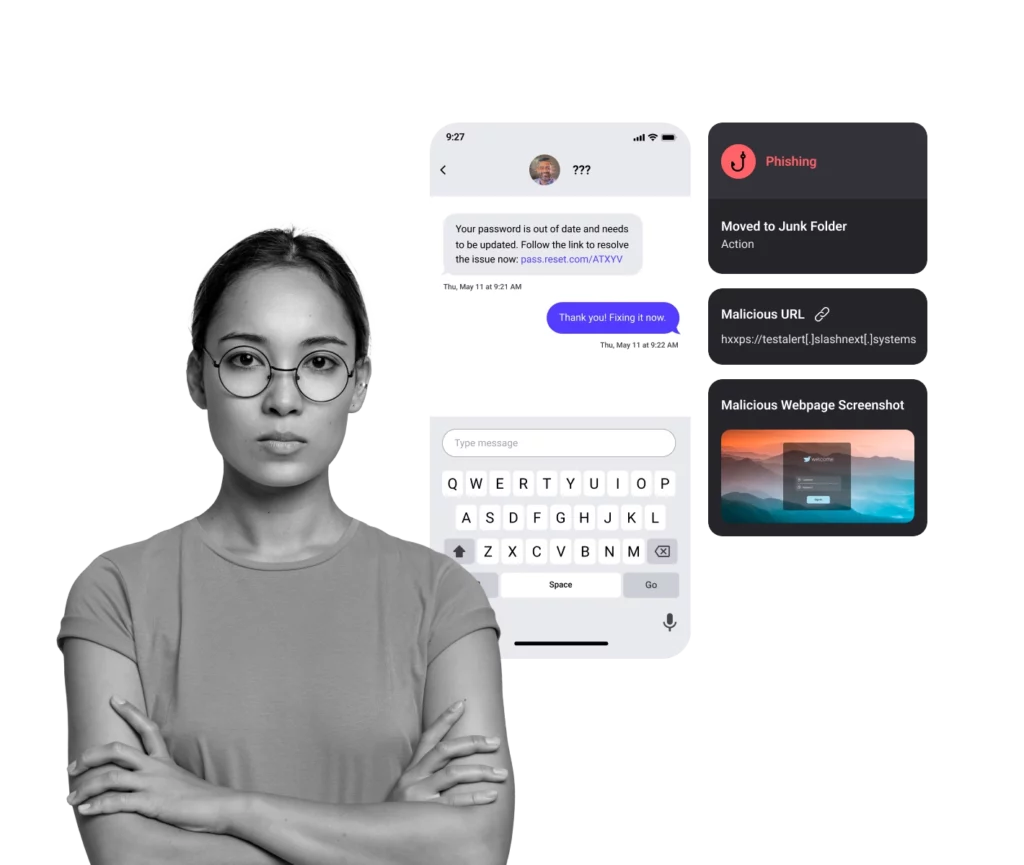
Smishing and Business Text Compromise (BTC) Protection
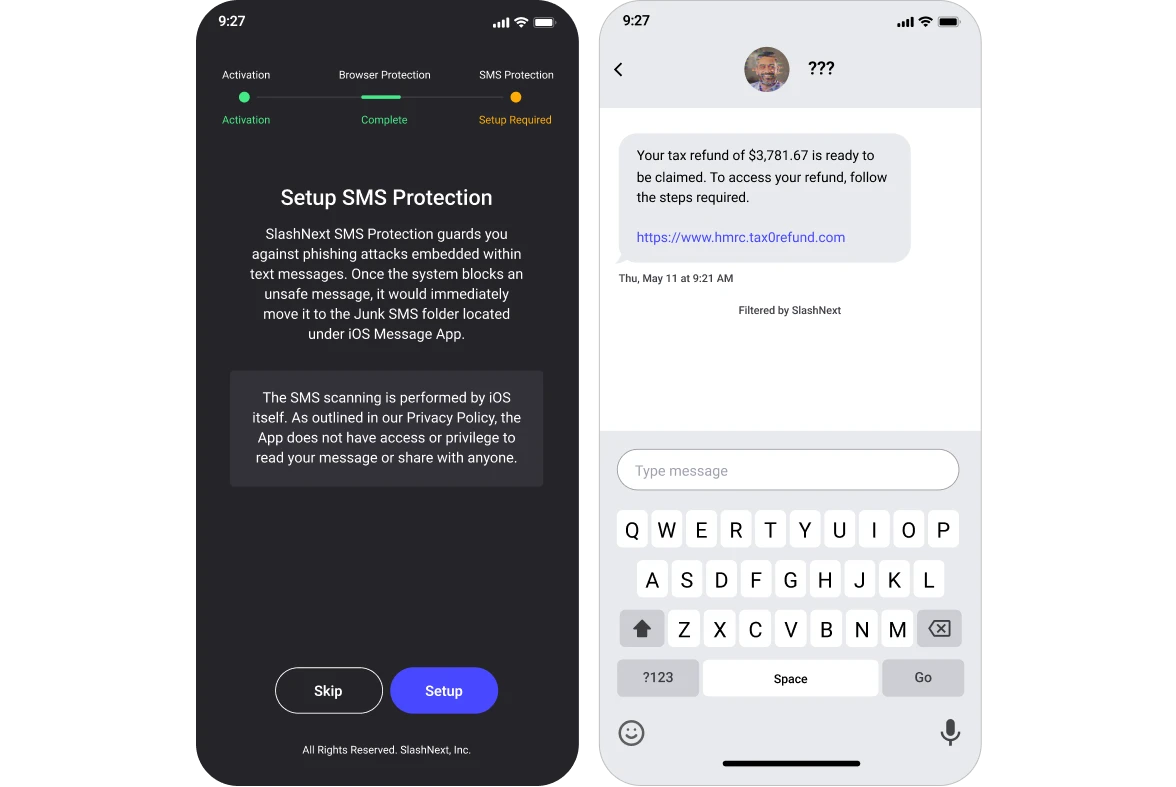
Enterprise-Grade User Experience
State-of-the-art protection and user experience, including:
- Safe preview of the phishing site
- Helpful threat information to educate users
- Ability to submit a support ticket about the incident
- Automated notifications and reporting
- Lightweight memory consumption and battery usage
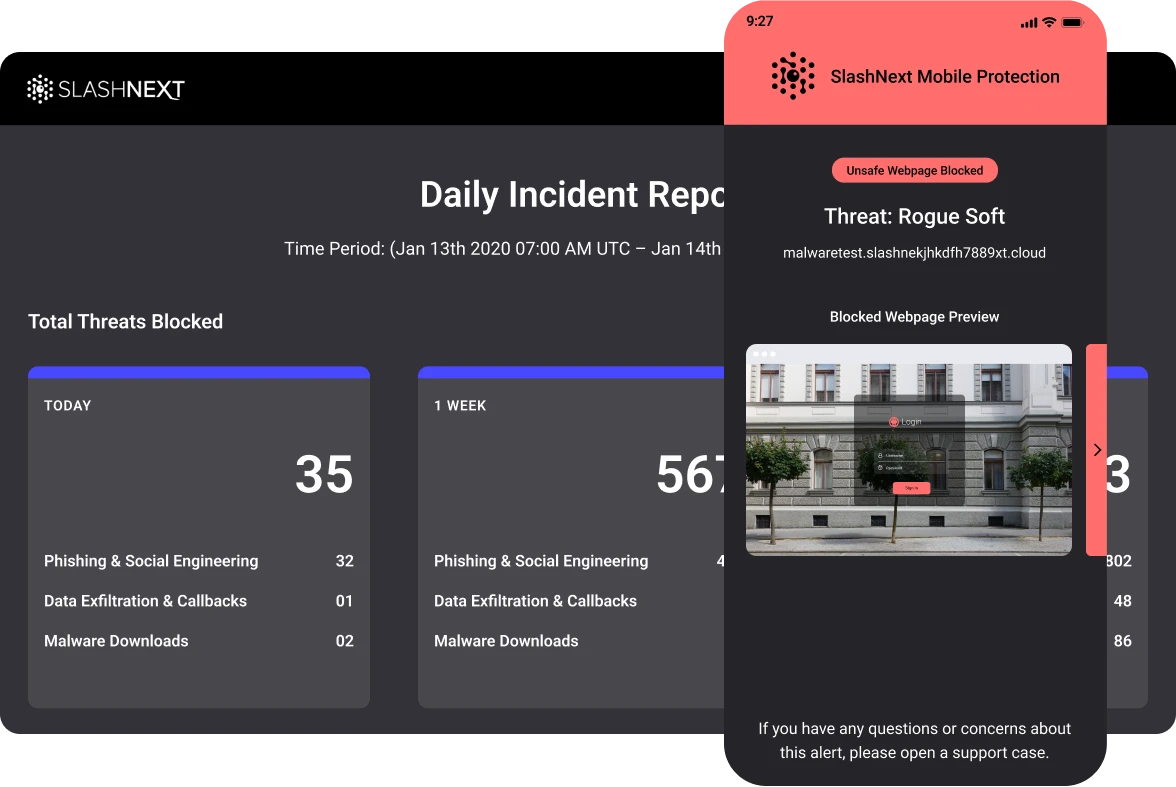
Advanced Reporting and Analytics
Easily manage groups, policies, users, and licenses. Advanced reporting and analytics features include filters to view data by threats, endpoints, and users for a full view across the enterprise.
Drill-down into high-risk users, timelines, and detailed forensics information. Automate daily or weekly reporting, including incidents and executive summaries.

We found a lot of value in their (phishing) protection. Overall a great addition to our cybersecurity protection suite.
CIO, Moffatt & Nichol
Stop The Attacks That Impact Your Business

Social Engineering, Scams and Fraud
Deception to manipulate users into divulging information for misuse.

Trusted Services Compromise
Uses trusted domains to obfuscate cyber attacks to increase success.
Ransomware, Malware and Exploits
Intended to inject code, take-over browser canvas or download malware.

Malicious Attachments
Malicious HTML, PDF and Office files used to harvest credentials or download malware.

BEC, ATO and Supply Chain Attacks
Targets execs or financial teams to defraud a company for financial gain.

Credential Stealing
Cyber attack designed to steal passwords with the intent of accessing protected data.
Spear Phishing
Personalized targeted attack designed to trick users into a data breach or for financial gain.
Smishing and BTC
Using SMS text messages to trick users into divulging passwords or other PII for fraudulent use.
SlashNext Delivers Best in Class Results on Day One
5 mins.
Quick deployment via MDM or App story
99.9%
Detection rate with 1 in 1 million false positives
2x more
Blocks two times more phishing threats than competing solutions
1 hr.
Incidents caught within the first hour of deployment for incredibly quick time to value
100%
Guaranteed user privacy
48 hrs.
Detection advantage
Related Resources
FEATURED WHITE PAPER
Microsoft 365 + Integrated Cloud Email Security
Due to the demands of the modern workforce, there has been an exponential shift in the use of native cloud email protection capabilities, like Microsoft 365, in the last 12 months.

FEATURED DATA SHEET
Mobile BYOD Security Report
With 50% of phishing happening outside of email, security leaders need to address the risk of attacks via personal mobile devices.

Featured Blog
SMS Gateways Allow Cybercriminals to Flood Phones With SMS Phishing Messages
See SlashNext Complete™
in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.