Cloud Manager
Elegant CMS for full visibility, administration and reporting to see the high-risk users, timelines and forensics.
Boost Your Visibility and Controls
Advanced Reporting Features
Visualize Threats Across the Organization
Detailed Forensics
Advanced Reporting Features
Advanced Reporting Features
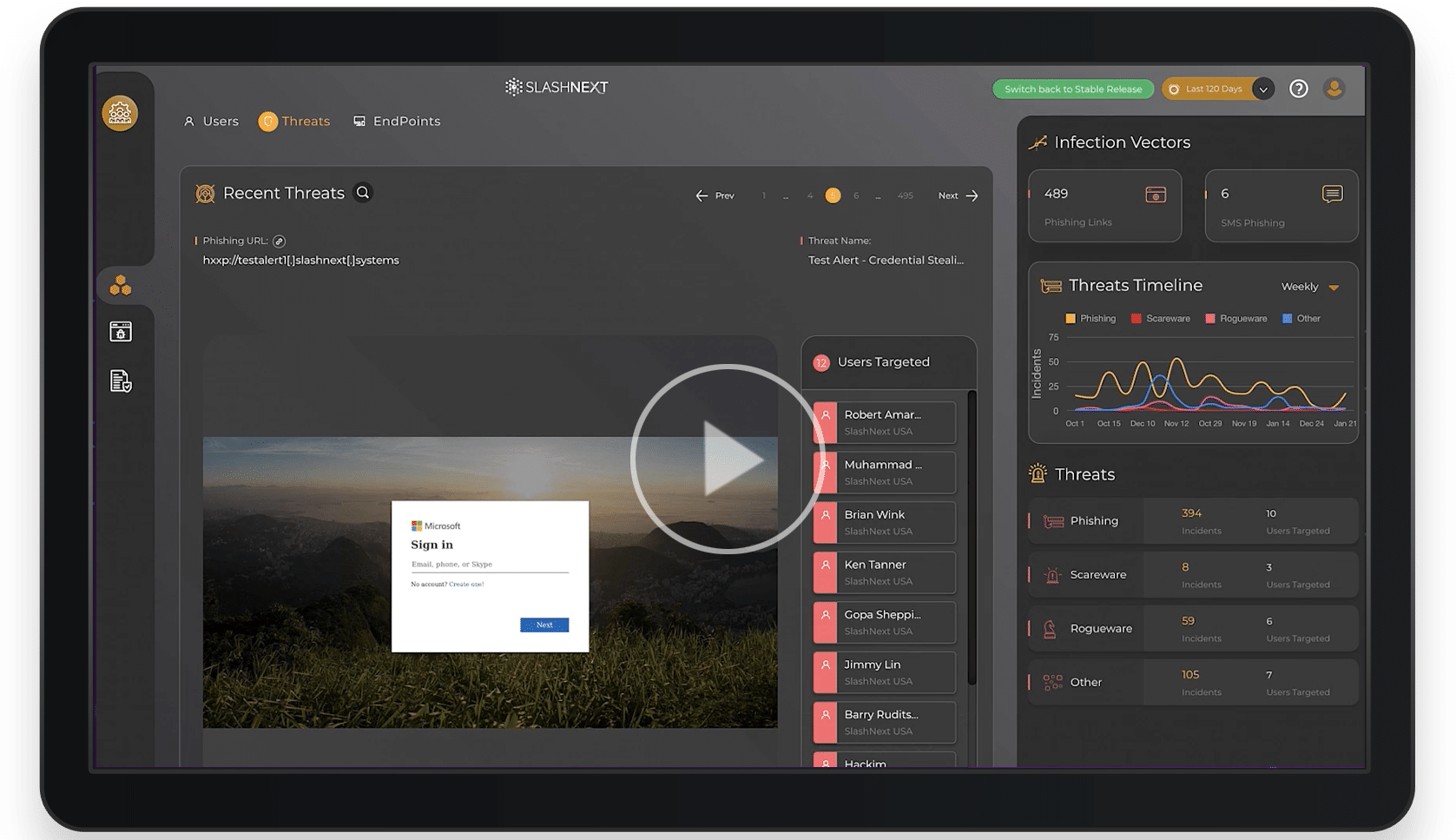
At any time, all the threats blocked within the organization can be viewed and investigated. View threats by users, to see the users clicking the most, and gather intelligence on how high-value users are being targeted.
Available as CMS Web Portal or can be ingested through CMS SIEM Apps and QRadar.
Visualize Threats Across the Organization
Visualize Threats Across the Organization
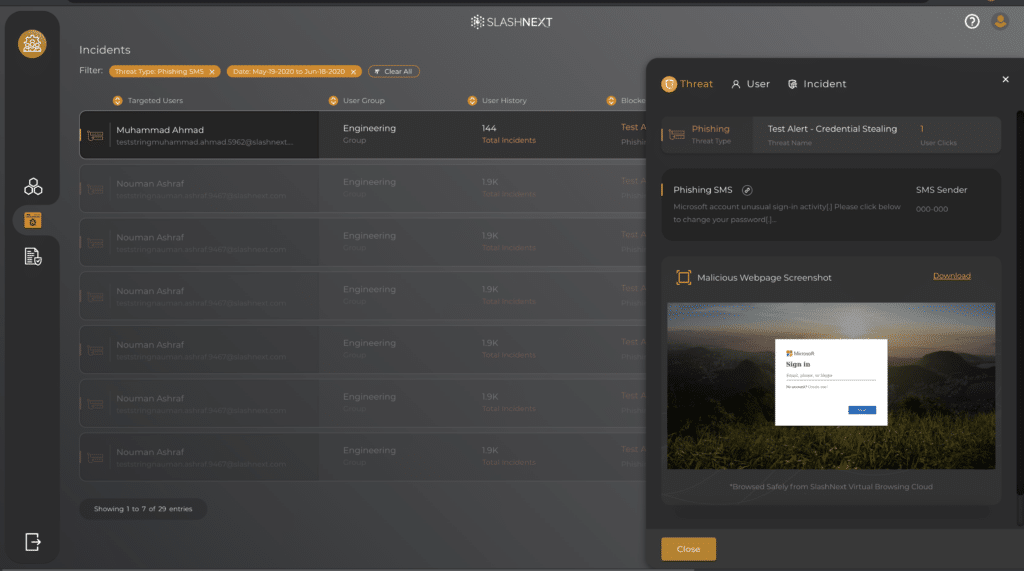
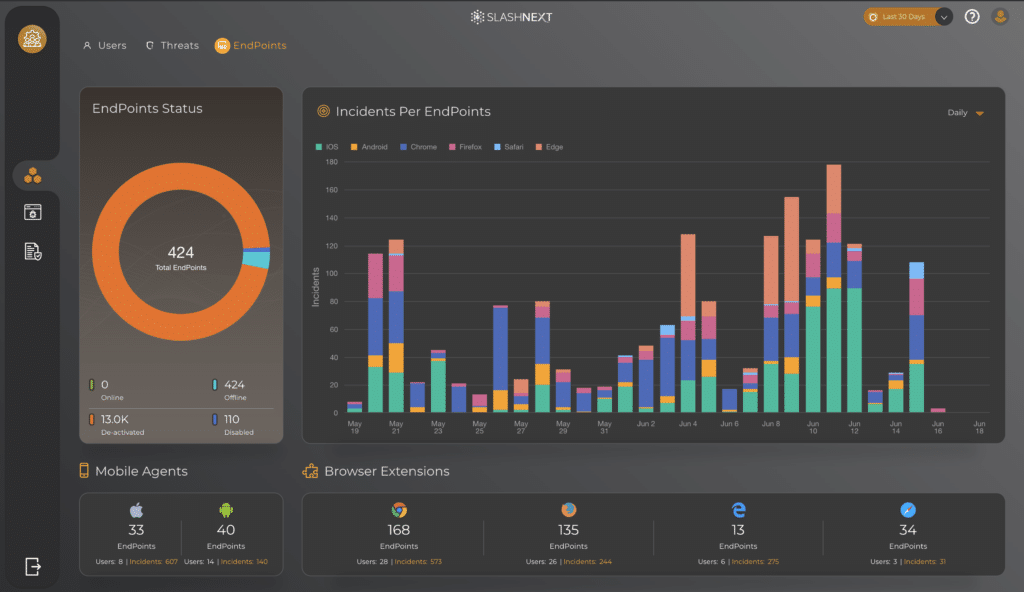
Viewing threats by browser or phone type can illuminate issues being exploited during release updates or a new type of attack targeting the user base. Administrators can drill down into the exact details of the threat on one page.
Detailed Forensics
Detailed Forensics
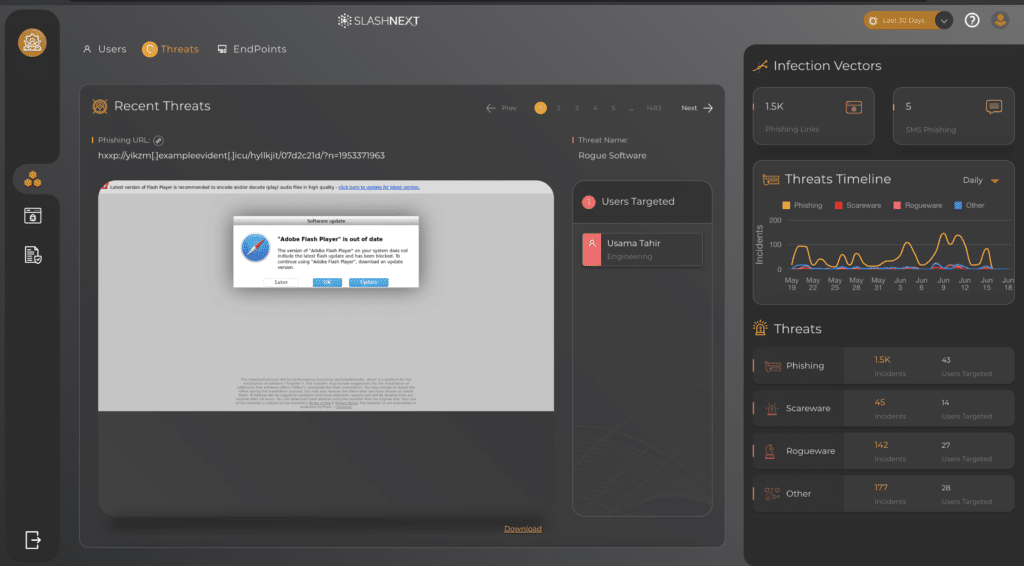
Dive into any threat for detailed forensics and to correlate data on users susceptible to certain threats. Heuristics can be viewed on the right-hand panel to see all types of phishing incidents, including credential stealing, scareware, rogue software, and callbacks that have been detected.
Related SlashNext Products
Mobile Protection
Protect iOS and Android users from mobile-centric phishing threats with a lightweight, cloud-powered agent.

Browser Protection
Shield employees from live phishing sites with cloud-powered browser extensions for all major desktop browsers.
Key SlashNext Advantages
Broad Threat Coverage
AI Phishing Defense SEER technology cloud discovers thousands of new phishing threats every day across all six major phishing categories.
Multi-Vector Threat Sourcing
SlashNext gathers intelligence in real-time from a variety of infection vectors including email, ads, mobile, and social media.
Higher
Accuracy
Near-zero false positives with 99.07% precision, yields high-fidelity blocklist of live phishing domains and phishing C2s.
Live
Threats Focus
Automated URL rechecking and retirement yields a continuously updated list of live, not inactive, phishing threats.
Real-Time
Detection & Access
Real-Time – Preemptive, automated threat detection with API access enables real-time protection.
AI Phishing Defense SEER™ Technology
Uses virtual browsers in a purpose-built cloud to accurately detect phishing sites, even those hosted on compromised websites and legitimate hosting infrastructure.
Rapid
Deployment
Pre-built integrations with leading TIP, DNS, and NextGen Firewall vendors provide rapid, automated deployment.
It’s Time to Get Started with SlashNext
Learn how to leverage the industry’s best zero-hour phishing protection and IR solutions in your environment.


