SlashNext Blog
Phishing, social engineering, and modern threats.
Featured Article
Think Security Training Will Save You From Phishing Attacks? Think Again!
What’s Required: Intercept phishing attempts before they reach the intended targets In the vast and intricate web of cybersecurity threats, phishing attacks stand out for their deceptively simple yet alarmingly effective tactics. As we delve into the anatomy of a typical phishing scam, it becomes apparent why these attacks not only persist but thrive in […]
Featured Article
10 Ways URL Analysis & Enrichment Can Help Ease Your SOC’s Challenges in 2020
On-demand phishing URL analysis solutions can help ease your SOC teams’ pain and challenges.
Blog Subscription

Thousands of Zero-Day Spear Phishing Attacks Continue to Target Covid-19 Pharmaceuticals
Three days before the …

You Want to Know How to Stop Phishing for Good. Hint: It’s Not a Silver Bullet
In a recent survey, se…

Constant Vigilance Required to Defeat Continually Evolving Phishing Threats
It’s been a year since…

URL Scanning vs. URL Analysis and Enrichment: What’s the Difference and Why it Matters.
Researching URLs in su…

Next-Gen Protection Essential to Prevent Evolving Phishing Attacks
In early February, Sla…

SlashNext Named in The Top 25 Cybersecurity Companies Of 2020
The companies selected…
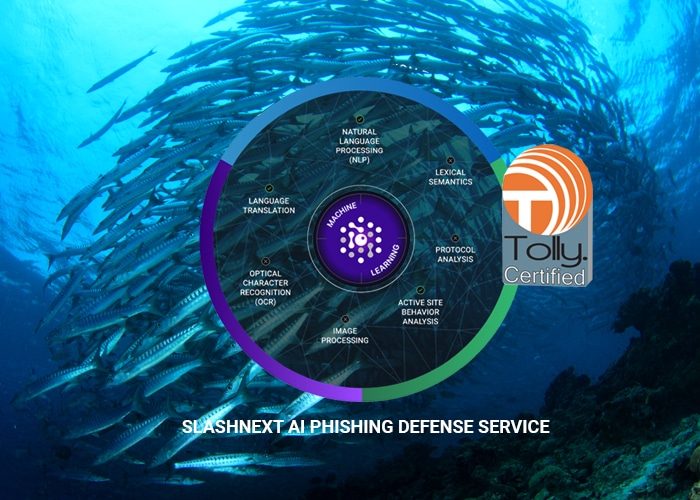
As Phishing Attacks Increase in Success, SlashNext Spear Phishing Detection Rates Highest Among K...
Cybercriminals are usi…

SMiShing Spawns the Need for a Better AI Mobile Phishing Defense
There has been a 600 p…
It’s Time to Get Started with SlashNext
Learn how to leverage the industry’s best zero-hour phishing protection in your environment.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.





